
Cyber Security
“`html Microsoft has deployed its most recent cumulative update for Windows 10, versions 21H2 and 22H2, along with Windows 10 Enterprise LTSC 2021 and Windows 10 IoT Enterprise LTSC 2021. This update, designated as KB5062554 (OS Builds 19044.6093 and...

Cyber Security
“`html Officers from the Russian Federal Security Service (FSB) have apprehended two hackers in Siberia who executed cyber incursions on critical infrastructure sites at the behest of Ukrainian intelligence agencies. The concurrent detentions in the Kemerovo and...
Cyber Security
“`html Significant vulnerability in Citrix NetScaler devices mirrors the notorious 2023 security incident that incapacitated major enterprises globally. The newly discovered critical flaw in Citrix NetScaler devices has cybersecurity professionals alerting about...

Cyber Security
“`html A significant security flaw has been identified within HIKVISION’s applyCT component, part of the HikCentral Integrated Security Management Platform, enabling attackers to execute arbitrary code remotely without the need for authentication. Designated...

Cyber Security
“`html The .COM top-level domain persistently leads the cybercriminal realm as the primary medium for hosting credential phishing sites, sustaining its status as the most frequently exploited TLD by threat actors globally. Recent insights reveal that malicious...

Cyber Security
“`html The intensifying hostilities between Iran and Israel have incited an extraordinary increase in hacktivist cyber operations, with more than 80 separate collectives executing synchronized attacks across 18 essential infrastructure domains. In response to...
Cyber Security
Numerous severe vulnerabilities in D-Link router variants could permit distant attackers to run arbitrary code and acquire unauthorized access to the network framework. Summary 1. Six severe vulnerabilities in D-Link DIR-816 routers permit remote code execution (CVSS...
Cyber Security
“`html Five committed bug bounty initiatives enhanced across 1inch core elements, such as smart contracts, wallet, and infrastructure. A community-centric strategy to bolster DeFi security and robustness. 1inch, the foremost DeFi aggregator, has introduced an...
Cyber Security
“`html In our rapidly evolving, interconnected environment, the threats posed by cyberattacks are becoming increasingly common and intricate. Consequently, it is crucial to remain informed and conscious of the dangers. Each week, our newsletter provides a...
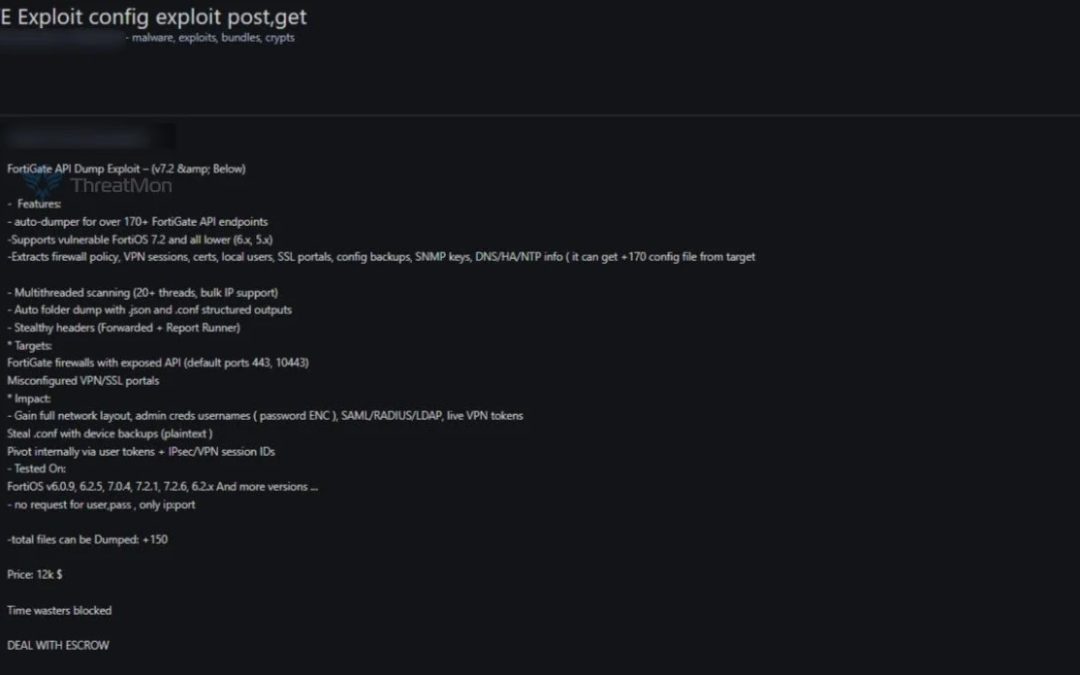
Cyber Security
“`html A threat actor has allegedly placed a sophisticated FortiGate API exploit tool for sale on a dark web marketplace, sparking considerable alarm within the cybersecurity sector. The tool, which is being offered at a price point of $12,000 and includes...








