“`html
A threat actor has allegedly placed a sophisticated FortiGate API exploit tool for sale on a dark web marketplace, sparking considerable alarm within the cybersecurity sector.
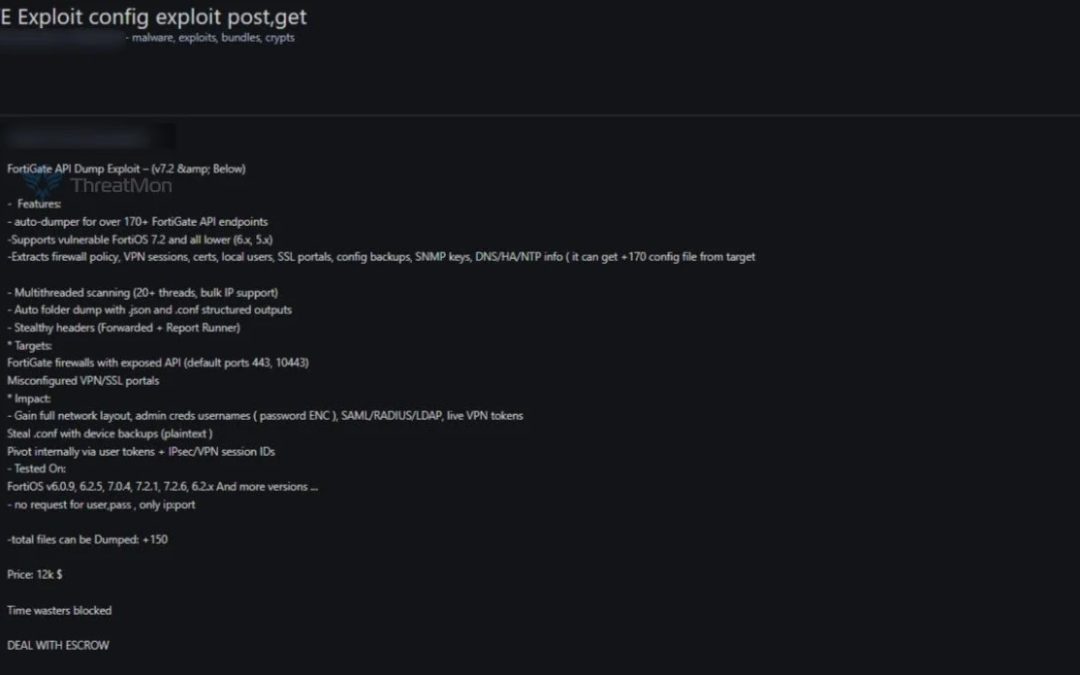
The tool, which is being offered at a price point of $12,000 and includes escrow services to facilitate the transactions, is purported to target Fortinet’s FortiOS systems by taking advantage of over 170 unprotected API endpoints, enabling attackers to gather extensive amounts of sensitive data from compromised devices.
Information regarding the tool’s functionalities has surfaced through leaked promotional content and image postings on clandestine forums.
Alleged API Exploit Tool Assertion
As per those revelations, the exploit incorporates an automated module that can scan and pull data from a wide array of FortiGate firewall appliances operating on vulnerable FortiOS versions, specifically 7.2 and earlier, but also confirmed to impact earlier releases from the 6.x series.
It employs multi-threading techniques for swift, bulk data extraction, allowing attackers to target several devices simultaneously and extract over 150 distinct configuration files in a single action.
The exploit reportedly grants access to highly sensitive and crucial configuration data. Among the types of information said to be retrievable are firewall policies, VPN session logs, user credentials, SSL portal configurations, SNMP community and encryption keys, along with other intricate network settings, including DNS, high-availability cluster setups, and NTP server information.
Notably, the tool allegedly circumvents standard authentication measures, requiring only knowledge of the device’s IP address and the API port typically exposed at 443 or 10443 without needing a username or password.
The repercussions of such unauthorized access could be substantial, revealing organizational network structures, admin password hashes, backup configuration files, and even live authentication tokens for SAML, LDAP, RADIUS, or VPN sessions, facilitating lateral movement or privilege escalation within corporate environments.
Security experts caution that the arrival of such an exploit not only elevates the risk of opportunistic attacks but also diminishes the technical barriers for less skilled malicious actors to pursue large-scale breaches.
The tool’s automation, combined with support for structured data output and discreet HTTP header adjustments, would enable both large-scale exploitation initiatives and targeted espionage activities with relative simplicity.
Currently, there is no confirmation from Fortinet regarding the authenticity of the exploit; however, organizations operating affected FortiOS versions are urged to evaluate their security stance, restrict unauthorized API access, and apply firmware updates urgently where feasible.
The disclosures highlight the escalating threat presented by the commercialization of advanced exploitation tools in cybercriminal marketplaces, emphasizing the necessity of ongoing vigilance, effective vulnerability management, and the prompt implementation of security updates in enterprise defense plans.
The post Threat Actor Allegedly Selling FortiGate API Exploit Tool Targeting FortiOS appeared first on Cyber Security News.
“`