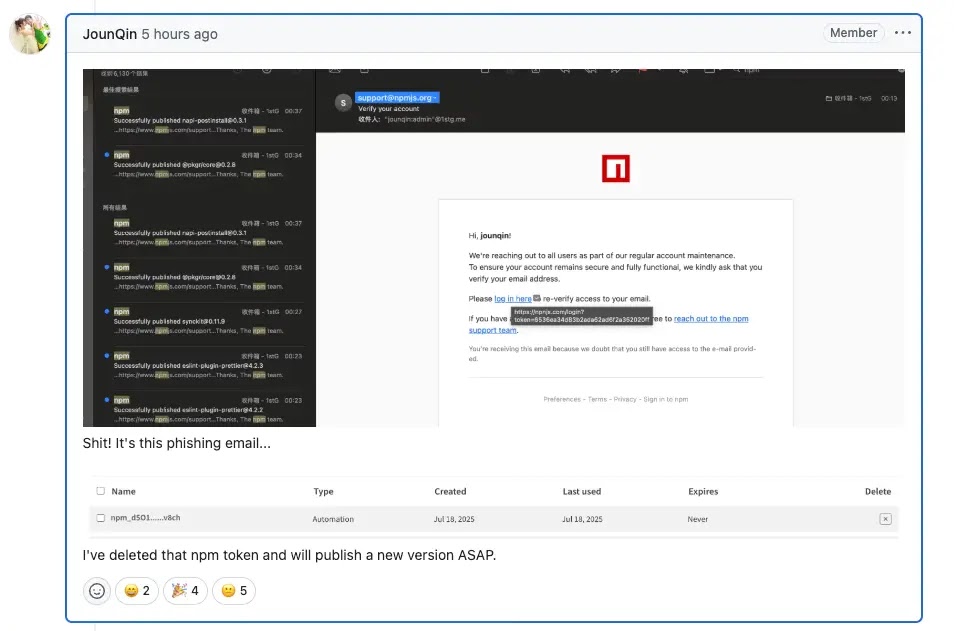
An advanced supply chain assault has compromised numerous extensively-utilized npm packages, such as eslint-config-prettier and eslint-plugin-prettier, after malicious actors successfully acquired maintainer authentication tokens via a focused phishing scheme.
The strike exploited a typosquatted domain, npnjs.com, intended to closely resemble the authentic npmjs.org website and capture developer credentials through persuasive phishing messages.
This nefarious campaign signifies a multi-phase supply chain breach that exploited the trust embedded within the npm ecosystem.
Perpetrators initially gathered maintainer credentials through cunning phishing emails, subsequently employing these pilfered tokens to distribute harmful package versions directly to npm repositories without altering any corresponding GitHub repositories, thereby making the breach considerably more challenging to identify through conventional monitoring techniques.
Socket.dev investigators discovered the breach after abnormal activity reports indicated that various versions of popular packages were published without matching commits or pull requests on GitHub.
The impacted packages included eslint-config-prettier versions 8.10.1, 9.1.1, 10.1.6, and 10.1.7, alongside eslint-plugin-prettier versions 4.2.2 and 4.2.3, synckit 0.11.9, @pkgr/core 0.2.8, and napi-postinstall 0.3.1.
The malicious code specifically aimed at Windows systems with a perilous payload intended to execute remote commands.
Examinations revealed that the inserted code attempted to load and run a DLL file named node-gyp.dll using the Windows rundll32 utility, potentially granting attackers total system access and the capability to execute arbitrary code on compromised devices.
Infection Mechanism
The assault’s complexity resides in its exploitation of npm’s metadata transparency, where registration emails and maintainer information can be easily gathered by malicious actors to formulate detailed target lists.
The harmful payload utilized Windows-specific execution methods, employing the following code pattern:-
// Simplified representation of malicious code injection
process.platform === 'win32' && require('child_process').exec('rundll32 node-gyp.dll,entrypoint');This technique allowed the malware to establish persistence and remote code execution capabilities while staying inactive on non-Windows systems, illustrating the attackers’ comprehension of cross-platform development environments and their aptitude for creating targeted payloads that maximize effect while minimizing detection across various development ecosystems.
The post Threat Actors Hijack Popular npm Packages to Steal The Project Maintainers’ npm Tokens appeared first on Cyber Security News.