“`html
Every SOC analyst understands the irritation. Your SIEM produces hundreds, occasionally thousands of alerts each day.
Each alert requires focus, yet with limited time and resources, how do you rank them efficiently? Examining each alert separately leaves teams reactive, bogged down, and ultimately exposed to advanced attacks that merge into the surrounding noise.
The Alert Triage Conundrum: Flooded with Data, Deprived of Context
The issue isn’t solely quantity; it’s context. An IP address flagged in your network may appear harmless until you realize it’s been persistently targeting firms in your sector for weeks.
A file hash that seems harmless might be part of a larger operation that has already infiltrated your rivals. Without this comprehensive intelligence overview, even adept analysts function with significant limitations.
Threat actors are capable of establishing persistence, exfiltrating information, and vanishing in mere hours, sometimes minutes. Your detection capabilities must be on par with this speed, identifying risks not only accurately but immediately upon initial contact.
This is where the principle of collective defense proves essential. While your organization may be observing a specific indicator for the first time, the global security community might have encountered it multiple times.
The obstacle is accessing this collective insight in actionable, real-time formats that blend seamlessly with your current workflows. This is the challenge that solutions such as ANY.RUN’s Threat Intelligence Lookup face.

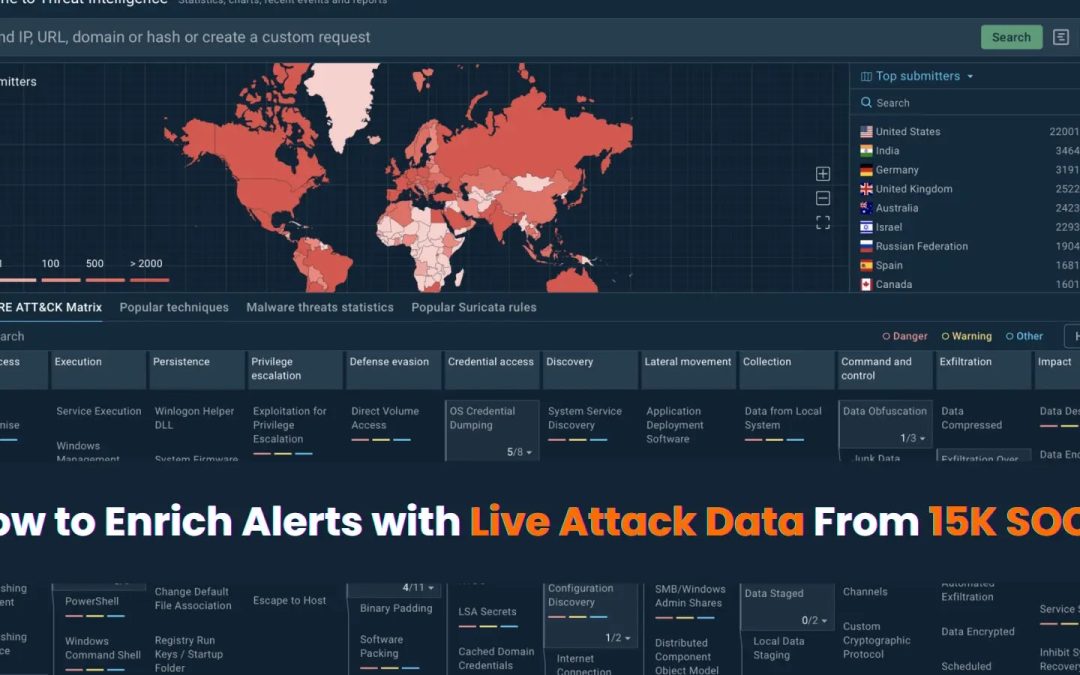
Threat Intelligence Lookup main page: search IOCs, explore TTPs, use YARA rules
Industry as a Target: You’re Not Isolated in Their Sights
Attackers seldom focus on single firms in isolation. They target entire industries, supply chains, and geographic areas. If you’re in financial services and your competitors are under siege, you’re likely next.
If you’re a healthcare provider and similar entities in your area are being compromised, prepare for the worst.
Threat actors allocate considerable resources to comprehend specific industry sectors, crafting specialized tools and techniques tailored for distinct business environments.
Once they refine their tactics against one target within your domain, they will systematically implement these proven strategies across comparable organizations.
Why External Incident Data Is Invaluable
Insights about attacks aimed at industry peers aren’t merely intriguing context; they constitute predictive intelligence.
When analysts comprehend the entire spectrum of ongoing operations against their sector, they can proactively seek early signs instead of waiting for attacks to manifest fully in their environment.
Your SOC observes what transpires in your network. But attackers often recycle domains, IP addresses, samples, and behaviors across numerous victims.
Having access to incident data from other entities provides you a shortcut: instead of spending hours verifying if an alert is malicious, you can check instantly against real-world attack data.
ANY.RUN Threat Intelligence Lookup: Instant IOC Verification
Using Threat Intelligence Lookup, SOC analysts are able to:
- Input an IOC (hash, IP, domain, URL, or file).
- Rapidly determine if it has appeared in real-world attacks observed across thousands of SOCs.
- Receive context such as malware family, behaviors, and timestamps of activity.
- Verify whether an alert relates to a tangible, ongoing threat — or merely background noise.
This transitions alert triage from labor-intensive, time-consuming validation to swift, assured decision-making backed by live attack evidence.
Start using TI Lookup for free to make rapid decisions on potential threats: Sign up to begin.The source of the threat data available through TI Lookup is ANY.RUN’s Interactive Sandbox.
It is utilized daily by over 15,000 SOCs globally: analysts at these organizations detonate questionable files, investigate malware behaviors, and analyze attack campaigns using ANY.RUN’s cloud-based platform. This creates an unparalleled repository of live attack intelligence.
For threat analysts and hunters, ANY.RUN’s Threat Intelligence Lookup offers:
- Faster triage: Quickly confirm whether an alert IOC is associated with an active attack.
- Reduced fatigue: Decrease hours of manual investigation by verifying IOCs in seconds.
- Enhanced detection confidence: Identify adversaries using the same infrastructure elsewhere.
- Improved hunting: Pivot
“““html
on connected IOCs and reveal concealed relationships in your ecosystem.
- Collaborative defense: Utilize the perspectives of 15,000 SOCs globally to bolster your own.
TI Lookup in Action: Utilizing It
ANY.RUN’s Threat Intelligence Lookup is accessible on a complimentary plan with restricted search criteria, enabling you to accomplish fundamental analyst tasks.
Let’s explore the aforementioned scenario to understand its functionality: a suspicious IP address detected in your system. Investigate it and receive an instant judgment:

An IP lookup yields a swift evaluation and extra IOCs
We can see that the IP has been marked as malevolent and has been observed in the most recent occurrences. For additional context, we can navigate to the “Analyses” tab and rapidly discover that it is associated with Agent Tesla spyware:

Malware samples examined in the Sandbox, identified through IP search
Premium Features for Superior Security Operations
When you are prepared for an upgrade, the Premium plan transforms TI Lookup into a thorough security intelligence platform:
- Enhanced Search Functions: More than 40 search parameters combined with complex operators (AND, OR, NOT) facilitate accurate threat hunting and investigative processes.
- Complete Attack Insight: Gain access to all available analysis sessions instead of just the 20 latest, offering extensive historical context.
- Confidential Intelligence: Perform private searches and investigations without visibility to other users, safeguarding sensitive security operations.
- Ongoing Monitoring: The Search Updates feature provides automated notifications when new threats align with your specified parameters, ensuring your team stays ahead of emerging campaigns.
- Expert Evaluation: TI Reports from ANY.RUN’s analyst team offer strategic insights on attack patterns and threat actor activities across various sectors.
Here is an illustration of a lookup search query you can employ on the Premium plan: more search criteria (registryKey, registryValue) and operators (NOT) are available; over 500 sandbox sessions are identified, enabling an analyst to observe specific malware behavior.
registryKey:”Run$” AND registryValue:”.url$” NOT threatName:”darkvision”

Malware samples showcasing particular behavior discovered through TI Lookup
Embrace the Strength of Collective Defense
The contemporary threat landscape necessitates a pivotal transformation from isolated defense to collective intelligence. No singular organization, regardless of scale or resources, can rival the extensive threat visibility that arises from global collaboration.
ANY.RUN’s Threat Intelligence Lookup exemplifies this collaborative methodology in practice: immediate access to intelligence gathered from 15,000 SOCs striving to analyze and comprehend active threats.
In a landscape where adversaries exchange techniques, tools, and targets across the global threat sphere, defenders must react with equal coordination and real-time intelligence sharing.
ANY.RUN’s Threat Intelligence Lookup delivers the immediate access framework to make this collective defense feasible and functional.
“`