“`html
Phishing operations are becoming increasingly difficult to detect, at times lurking in files you’d never anticipate. ANY.RUN’s cybersecurity experts recently identified a specific instance: a harmful SVG masquerading as a PDF, situated on a credible domain and filled with covert redirects. By mid-September, it had escalated into a substantial spam wave utilizing Microsoft-themed bait.
Let’s examine how it functioned, and how analysts can collect the entire sequence of information in a secure sandbox setting.
Inside the Recent SVG Assault
Here’s a sandbox demonstration that depicts the complete actions. Check the actual case to observe the redirects and payload extraction in real-time:
View the sandbox session (SVG attack)
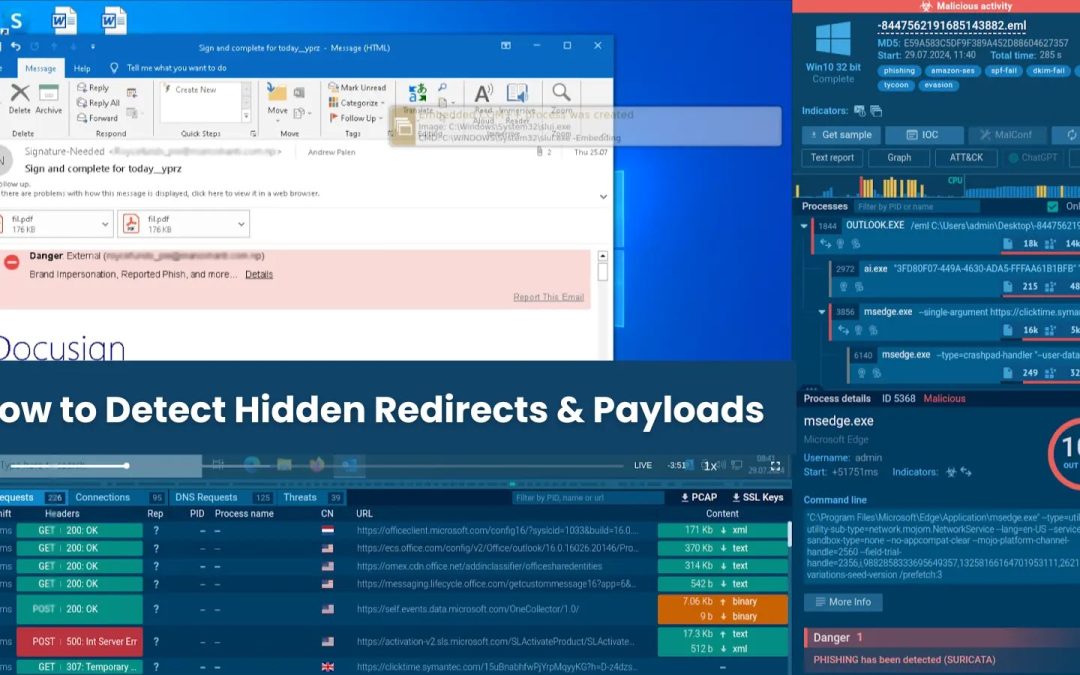
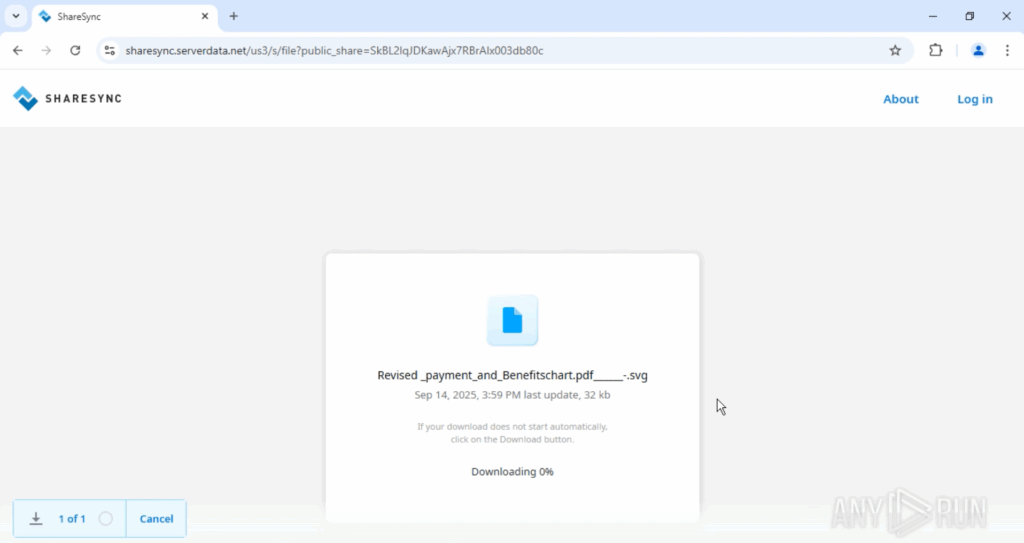
Delivery & concealment: The file arrives presenting itself as a PDF attachment but is, in actuality, an SVG (XML) file. Given that SVG permits scripts, the attackers integrate dynamic content instead of static images.
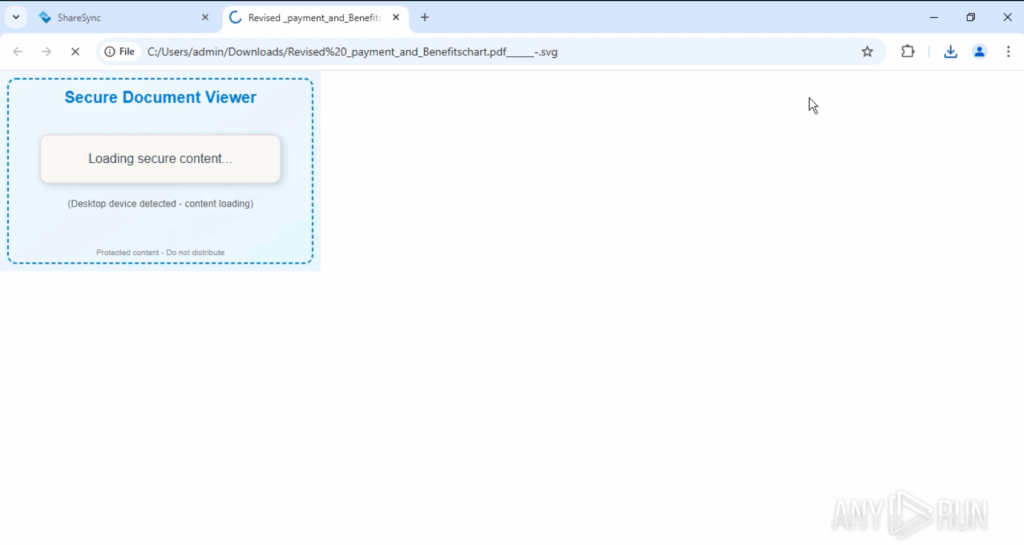
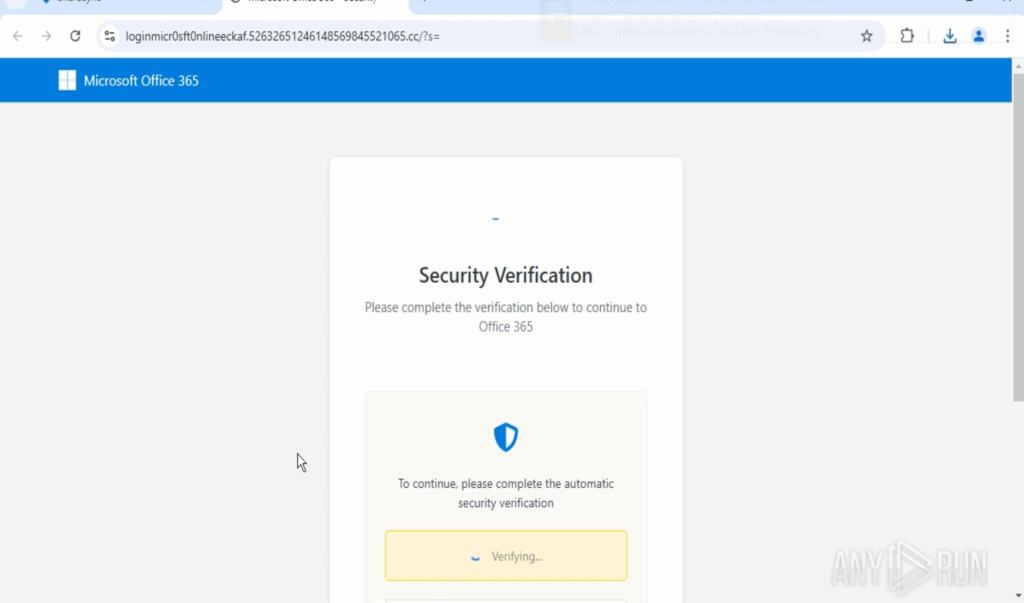
Fabricated prompt presented: Accessing the file in a browser showcases a “protected document” notification to manipulate the user into clicking or pausing.
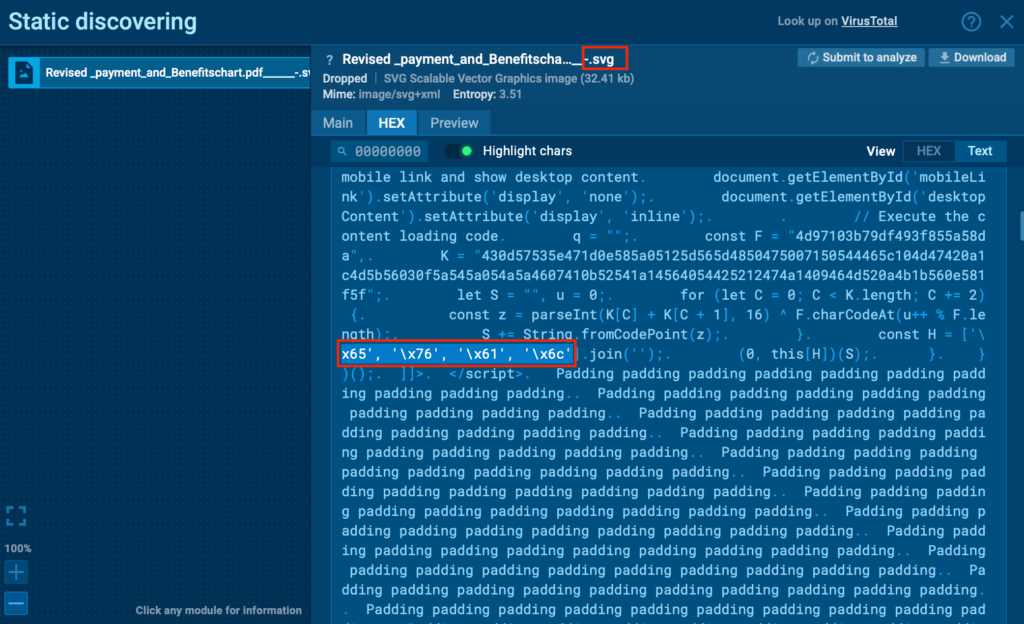
Script execution (XOR decoder): The incorporated JavaScript performs an XOR decoding process to reconstruct the genuine redirect code and then runs it (through eval).
You can directly observe this in ANY.RUN’s static/HEX view: the decoder variables, the hex/escaped bytes (for instance ‘x65′,’x76’,…) and the reassembled script are all visible in the session. That view enables analysts to extract the decoded payload and examine the precise commands that the SVG executes.
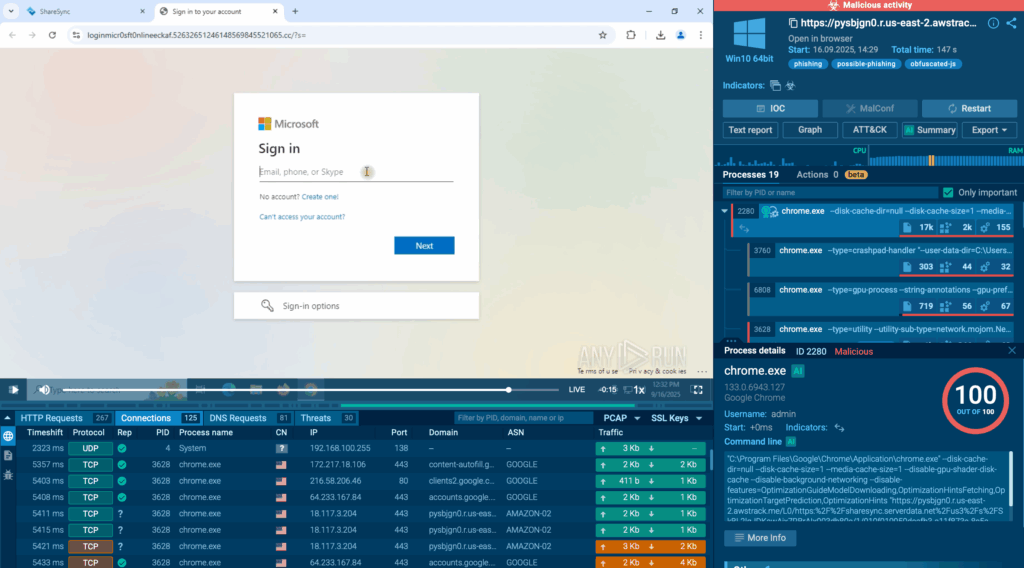
Layered redirects: The decoded code navigates the browser through several intermediary domains, obscuring the path. Instances noted in this sequence comprise:
- loginmicrosft365[.]powerappsportals[.]com
- loginmicr0sft0nlineofy[.]52632651246148569845521065[.]cc
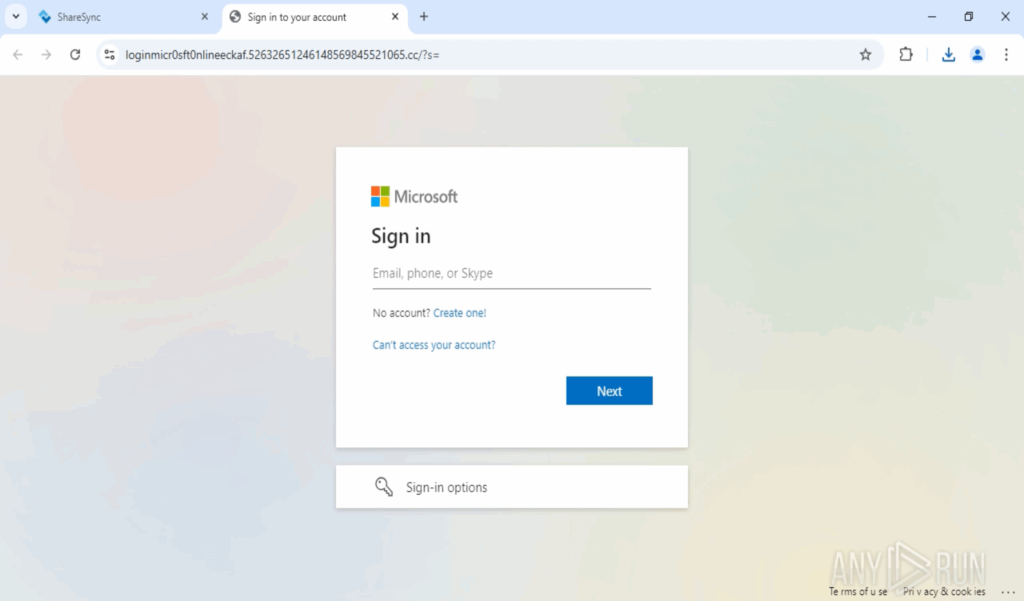
Ultimate phishing page: The individual reaches a Microsoft-branded credential page that even incorporates a Cloudflare Turnstile widget to appear credible and pass basic checks. Through ANY.RUN’s automated interactivity, these verifications are conducted automatically, allowing analysts to avoid spending time on manual clicks.
Credential accumulation & persistence: Submitted credentials are gathered and relayed to attacker-operated infrastructure designed for scalability (PhaaS-like), enabling extensive harvesting.
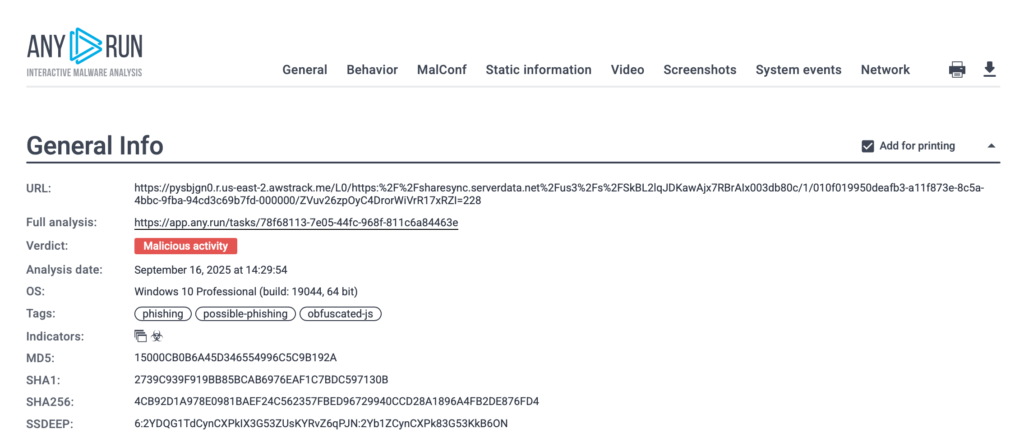
Insights from the sandbox: The interactive session illustrates every redirect and HTTP transaction, reveals the decoded JavaScript in HEX/Text, and captures runtime artifacts.
Exportable IOCs and reports can be seamlessly integrated with SIEM, EDR, and threat-intelligence platforms, enabling analysts to acquire data using the tools they already operate, thereby conserving time and eliminating redundant steps.
The Sandbox Advantage: Swift Detection of New Threats
As illustrated, interactive sandboxes are particularly essential for identifying novel and elusive attacks. Rather than depending on static signatures or delayed notifications, they execute the file in a live environment and unveil harmful activities in real-time.
With ANY.RUN, analysts can:
- Obtain malicious verdicts in under 60 seconds: 88% of threats are recognized this swiftly.
- Instantly unveil the entire attack sequence: every redirect, script, and payload delineated without uncertainty.
- Enhance triage and response: teams report up to 94% quicker triage and 3× enhanced SOC efficiency.
- Transform findings into action: export IOCs and TTPs directly into SIEM, EDR, or TI platforms to update detections and initiate hunts without delay.
By converting hours of manual effort into minutes of automated insight, sandboxes equip analysts with the speed, clarity, and context required to remain ahead of emerging attack methods.
Request your 14-day trial and discover how swiftly you can detect new attacks with ANY.RUN’s sandbox.
“`