“`html
Concealed weaknesses in older code frequently generate hidden threats for contemporary developmental frameworks.
A recent challenge emerged in the Python community, where obsolete bootstrap scripts linked with the zc.buildout tool render users susceptible to domain takeover threats.
These scripts, intended to facilitate the installation of package dependencies, incorporate fixed connections to external domains that are no longer managed by the initial maintainers.
The essence of the issue is a particular function in these scripts, wherein they seek to obtain the obsolete distribute package from python-distribute[.]org.
This domain has been deserted since 2014 and is now available for acquisition. Should a malicious actor obtain this domain, they could deliver harmful payloads that would be automatically retrieved and executed by any developer employing the compromised bootstrap script.
.webp)
This establishes a clear pathway for supply chain threats, circumventing typical security validations.
Security analysts from Reversinglabs discovered this vulnerability, highlighting that it impacts several prominent packages, such as slapos.core, pypiserver, and tornado.
Despite numerous developers adopting more recent packaging standards, these outdated files frequently linger in repositories.
The vulnerability is not triggered during a conventional pip install but generally necessitates manual execution or invocation via a build process like a Makefile.
Upon activation, the script unconditionally trusts the external source, presenting a considerable supply chain hazard akin to the fsevents incident within the npm registry.
Examining the Execution Procedure
The technical foundation of this vulnerability resides in the insecure manner the bootstrap script processes dependency resolution. The code logic specifically checks for the availability of the distribution package.
.webp)
If it is not located, the script initiates a download sequence utilizing Python’s standard urllib libraries. As depicted in the illustration above, the distributed setup is retrieved and executed in bootstrap.py; the script explicitly requests data from the now-defunct python-distribute[.]org.
Importantly, the response from this URL is directly fed to an exec() function, executing the code instantaneously without any integrity checks or signature validation.
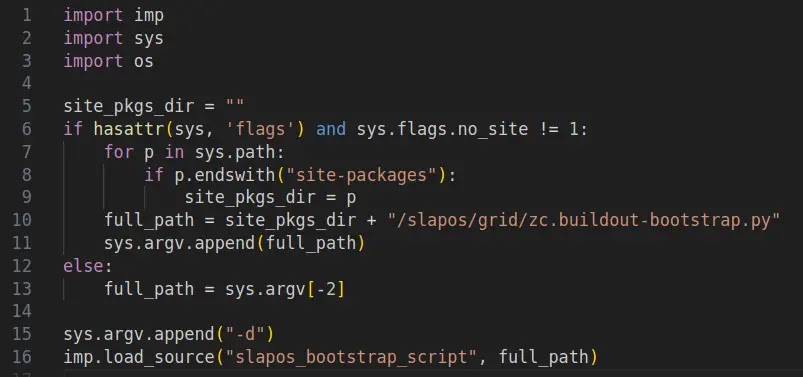.webp)
To substantiate this vector, researchers devised a proof-of-concept exploit aimed at slapos.core. The proof-of-concept script exploits the vulnerability in slapos.core by manipulating command-line parameters to direct the script into its susceptible download route.
The output observed in the terminal after executing the proof-of-concept script confirms that it establishes a connection to the external domain, validating that any code hosted there would operate under the user’s complete permissions.
“`

