“`html
A proof-of-concept (PoC) exploit pertaining to CVE-2025-55182, a critical remote code execution (RCE) vulnerability in React Server Components, emerged publicly this week, raising concerns for developers globally.
Referred to as “React2Shell” by several researchers, the security flaw has a CVSS rating of 10.0 and impacts React versions 19.0.0 to 19.2.0, along with Next.js 15.x and 16.x utilizing App Router. Additionally, even applications that do not directly implement server functions remain vulnerable if they incorporate React Server Components (RSC).
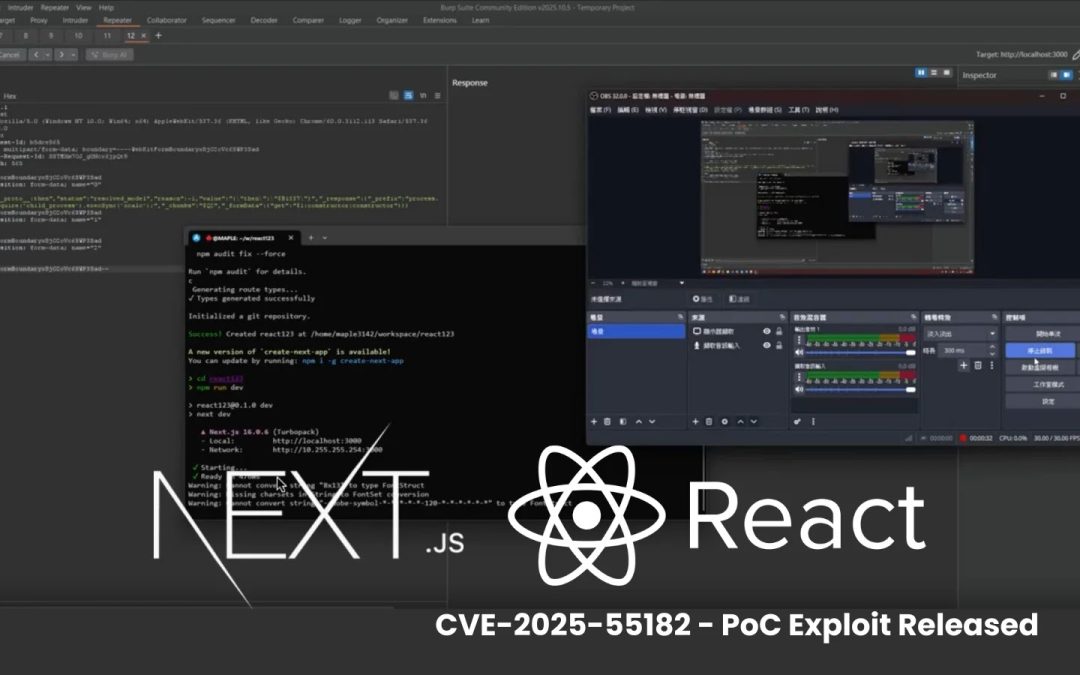
Security analyst @maple3142 showcased the exploit in a Twitter announcement, demonstrating a straightforward multipart HTTP request that embeds a Node.js payload.
The demonstration activates child process, launching a Linux calculator on the affected server without requiring authentication.
A supplementary video displays a curl-like command leveraging the vulnerability through React’s Flight protocol, evading serialization defenses using tactics such as Blob references tagged as “$B1337.” Presented as a CTF-style “JS jail” challenge, the public gist received admiration from the community as well as queries about evasion strategies.
The fundamental issue stems from inadequate deserialization within the RSC Flight protocol, where corrupted payloads contaminate object prototypes and seize control of server-side execution.
Identified by Lachlan Davidson and responsibly reported to Meta and Vercel on November 29, the problem became publicly known on December 3, leading to rapid patches.
A new scanning tool has also been launched to detect vulnerable endpoints across the network for CVE-2025-55182.
Amazon threat intelligence indicated exploitation attempts by China-linked groups, such as Earth Lamia, within hours of the disclosure. Wiz Research estimates that 39% of cloud environments harbor vulnerable instances, scanning over 968,000 servers.
Palo Alto Networks Unit 42 and others validated that the attack requires merely a crafted POST request to RSC endpoints, achieving nearly 100% reliability in testing. React’s formal advisory calls for immediate upgrades, highlighting that the flaw persists in default setups of widely used frameworks.
Developers are advised to review deployments, implement patches from React 19.2.1+ and Next.js updates, and keep an eye out for unusual activities.
Although no extensive breaches have been confirmed thus far, the PoC’s simplicity intensifies risks in production settings. This incident highlights the dangers of server-side rendering in contemporary JavaScript frameworks.
“`