“`html
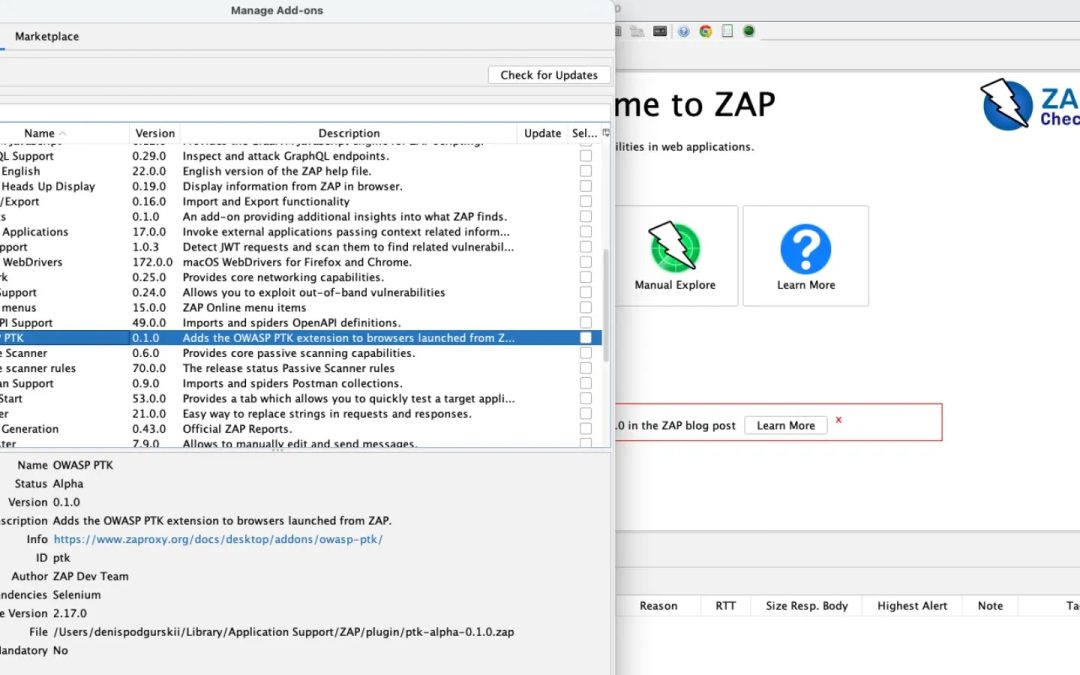
The Zed Attack Proxy (ZAP) group has unveiled the OWASP PTK extension, version 0.2.0 alpha, which incorporates the OWASP Penetration Testing Kit (PTK) browser add-on directly into browsers initiated by ZAP.
This enhances application security evaluation by embedding DAST, IAST, SAST, SCA, and distinct tools such as JWT and cookie managers without the necessity for manual configuration. Accessible through the ZAP Marketplace, this extension pre-installs PTK in Chrome, Edge, and Firefox sessions routed through ZAP.
Users can obtain the OWASP PTK extension from ZAP’s Marketplace and then start a compatible browser through ZAP’s functionality. The PTK icon appears promptly, enabling login to targets and the commencement of scans. ZAP manages traffic capture, site tree, history, and session oversight, while PTK supplies browser-integrated testing tools.

PTK’s DAST facilitates real-time scans during regular browsing: initiate a scan, navigate essential pathways like forms and admin interfaces, halt, and evaluate findings.
Optimal for SPAs dependent on user interactions, it suggests adjusting requests per second and concurrency for stability in production, along with stringent domain focusing to reduce noise. Results interconnect with ZAP for re-evaluation via request tools.
IAST observes browser runtime activities, embedding agents during scans to capture signals beyond mere response analysis. Start monitoring, navigate authenticated paths, and then assess DOM changes and client-side rendering concerns.
It excels in applications dependent on UI states, providing immediate context for penetration testers remaining within the browser workflow.

SAST evaluates inline and external scripts loaded in production, identifying sinks and patterns without repository access. Run on current pages, pivot findings to DAST/IAST for verification, particularly beneficial for third-party scripts in SPAs. SCA uncovers dependency vulnerabilities from running applications, analyzing packages with ZAP context for loading behaviors.
Request Builder promotes swift iteration: edit traffic from ZAP history, replay attacks, duplicate as cURL, or modify headers. JWT tools decode tokens, adjust claims/algorithms, and test enforcement mechanisms like exp or weak HMAC, replaying via ZAP for response comparisons. Cookie utilities allow editing, blocking, or exporting for session reproducibility.
A practical workflow begins with ZAP-proxied browser authentication, followed by PTK DAST/IAST during actions, SAST/SCA for static signals, and JWT/cookie validation.
This combination utilizes ZAP as the proxy center and PTK for focused browser testing, enhancing coverage on contemporary web applications. Highlight permission-based active scans and cautious settings.
The release, announced January 19, 2026, signifies a milestone in ZAP-PTK collaboration, developed with inputs from Denis Podgurskii. Pen testers benefit from efficient, context-aware examination for authenticated, dynamic applications.
“`