Secure browsing employs a cloud-based virtual browsing environment to examine potentially unsafe websites. This enclosed setting shields the local system from harmful activities encountered during browsing.
Users have the option to manually investigate dubious URLs within this virtual session. Real-time analysis by Safebrowsing, powered by exclusive technology, detects threats and produces a report at the conclusion of each session.
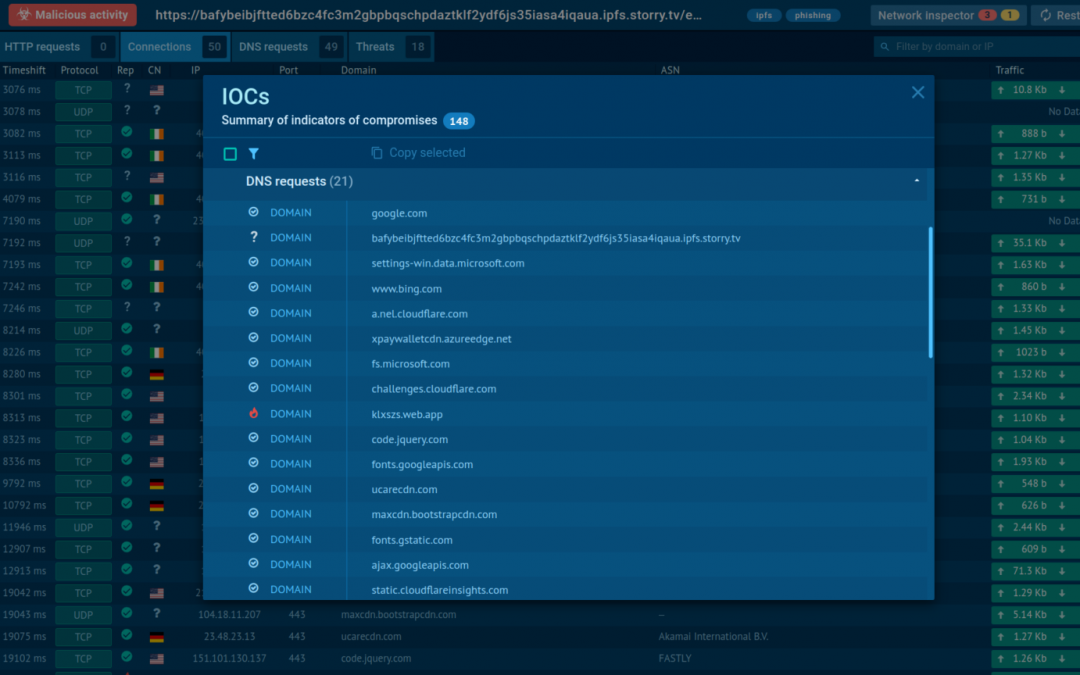
The generated report contains Indicators of Compromise (IOCs) and an elaborate network traffic analysis covering connections, DNS/HTTP requests, and threats identified by the Suricata intrusion detection system.
It presents a three-step procedure for evaluating websites. Initially, users enter a URL that is then loaded in a secure virtual browser. Users can then navigate the website as usual, while Safebrowsing supervises for malicious content.
Upon completion, the service compiles a report outlining detected threats and suspicious activities, encompassing a list of Indicators of Compromise (IOCs) and exported packet information in PCAP format.
Possible Applications of Safebrowsing
Safebrowsing is a versatile tool that can be extremely useful in various circumstances.
- Utilize secure, segregated, and full-scale virtual browsers to view URLs, preventing potential threats from impacting the local system.
- Accelerate the process of analyzing and addressing suspicious links.
- Ensure secure, straightforward, and swift link checks for non-security personnel.
- Enhance overall organizational security by preventing infections and increasing security levels.
- Demonstrate the risks associated with clicking on dubious links as part of safe browsing training.
- Monitor network traffic for malicious activities to identify threats in real time.
- Enhance phishing threat detection using ANY.RUN’s advanced functionalities.
- Retrieve traffic data and identified indicators of compromise.
- Share completed sessions as evidence of malicious content.
Operation of Safebrowsing
Enter URL
Safebrowsing, distinct from ANY.RUN’s sandbox, scrutinizes URLs exclusively within a pre-set environment, providing a simplified interface for non-experts, lacking deep system monitoring and file access capabilities.
Engage and Investigate Threats
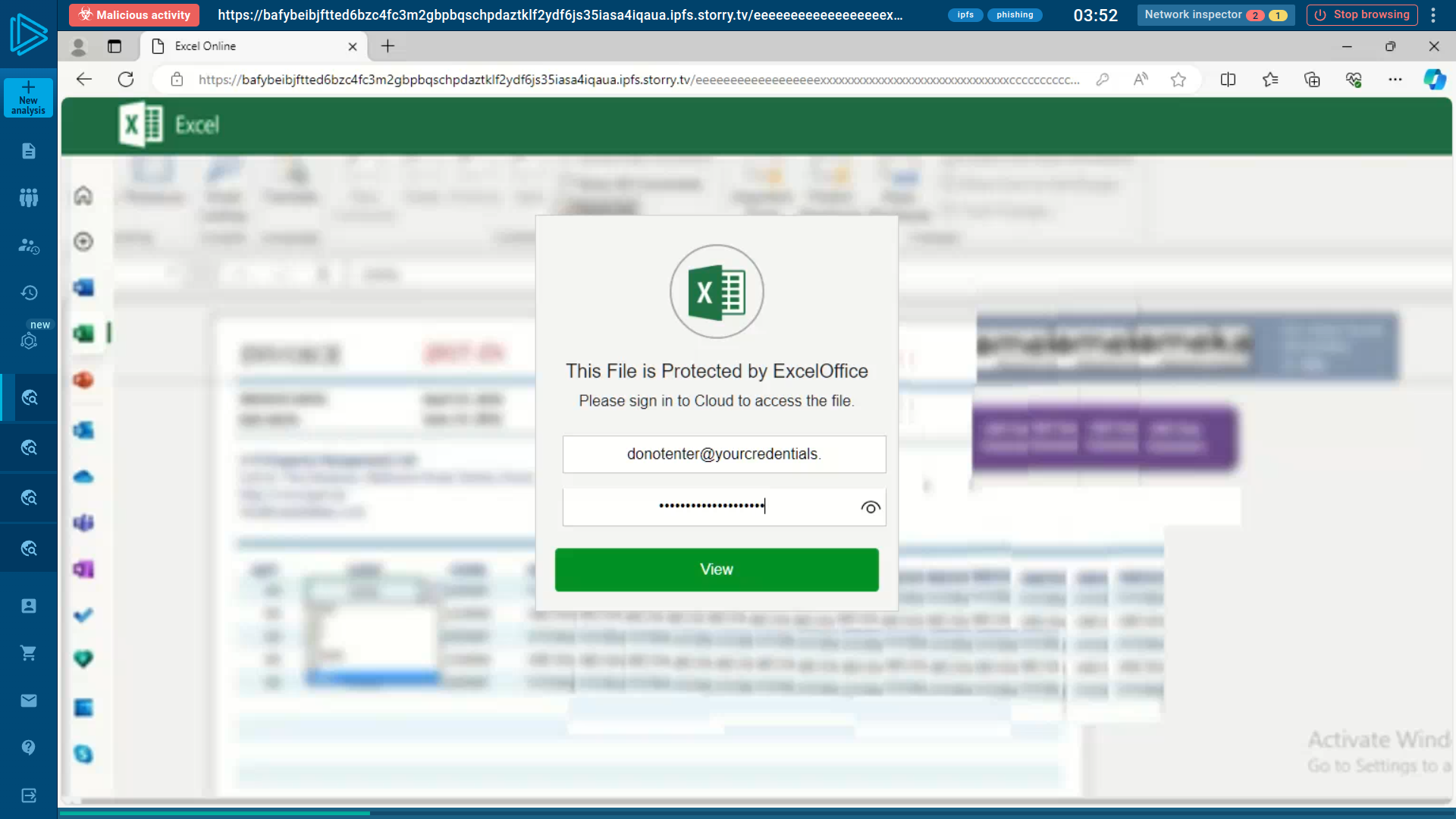
Similar to URL scanners checking against known malicious databases, Safebrowsing provides an interactive virtual browser for exploring website behavior in a controlled environment, enabling a thorough analysis beyond merely recognizing previously documented threats.
Gather IOCs
It can be utilized to enhance security in various aspects, allowing safe URL analysis within isolated virtual environments, preventing local system compromise by potential threats, streamlined investigation of questionable hyperlinks, making it accessible even to non-technical users.
It additionally protects organizations by proactively barring malicious websites and downloads, enhancing overall security posture, and serving as a tool for educational purposes, enabling security teams to illustrate the hazards of clicking on suspicious links during training sessions.
Safebrowsing empowers organizations to actively combat phishing threats. By allowing staff to securely explore dubious URLs, it aids in early detection and mitigation of data breaches and financial losses.
By being a beneficial training tool, it boosts employee awareness of web-based threats and fosters readiness by empowering non-expert staff to autonomously evaluate suspicious links, saving time and resources for security professionals.
The article “Analyse Any Suspicious Links Using ANY.RUN’s New Safe Browsing Tool” first appeared on Cyber Security News.