Cyber Security
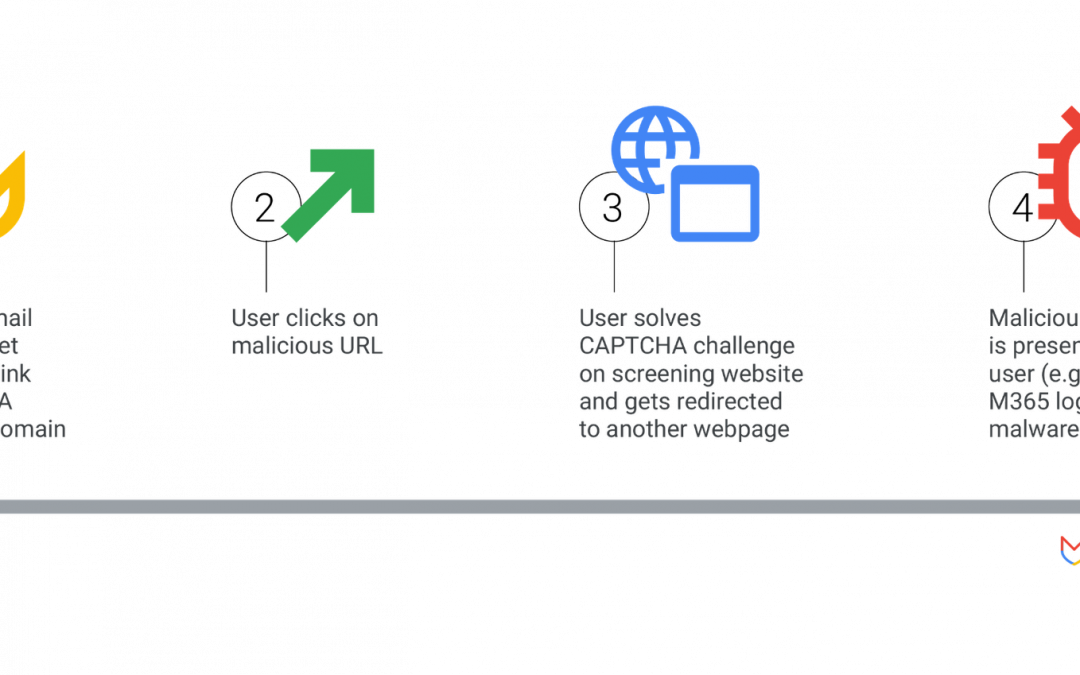
Scientific investigators from Mandiant and Google have revealed the ways in which cyber offenders are repurposing digital analytics and advertising utilities to amplify their harmful operations. These utilities, commonly utilized by promoters and advertisers to convey...

Cyber Security
When it comes to cybersecurity, the emphasis is often placed on technology — specifically, how cyber attackers utilize it to execute assaults and the resources that organizations can utilize to safeguard their systems and data. However, this disregards the most...

Cyber Security
The Paris 2024 Olympic Games unfolded as a resounding success, with around 10,000 competitors from 204 countries participating in 329 contests across 16 days. However, the authorities encountered substantial cybersecurity challenges both before and during the event....

Cyber Security
Quoting Yogi Berra, “It feels like we’re reliving the same moments again.” If seeing the global average expenses of data breaches escalating annually seems like a recurring theme, that’s because it is. Data protection solutions evolve, but so do cyber...
Cyber Security
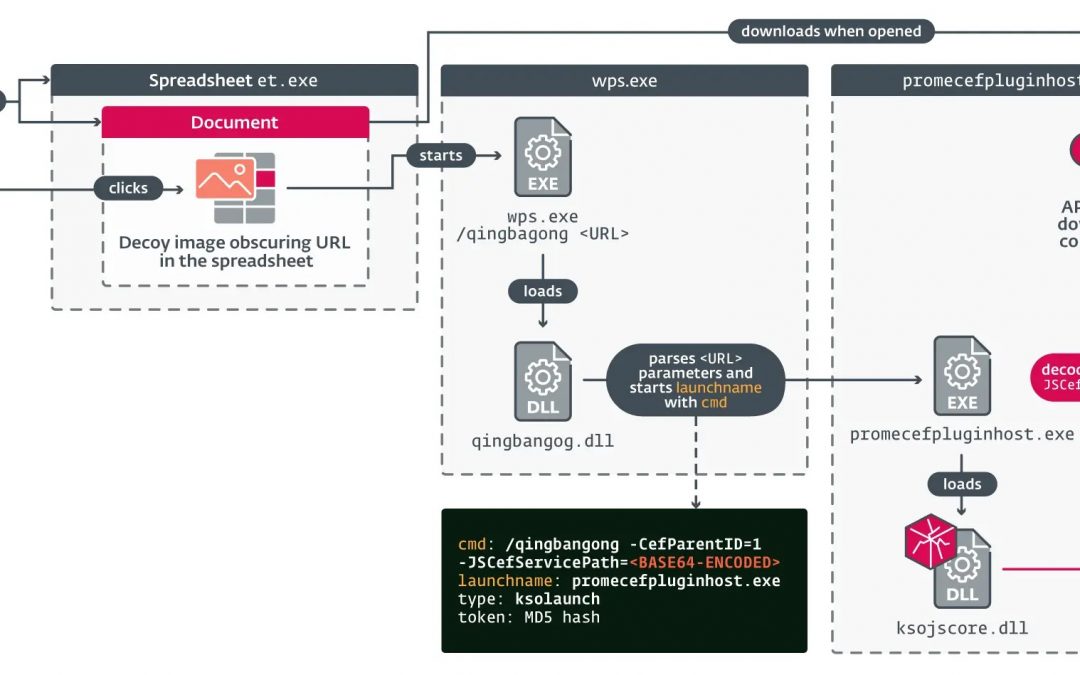
ESET analysts have discovered two crucial previously unknown weaknesses in WPS Office for Windows, which have been utilized by the APT-C-60 advanced persistent threat group. This cyberespionage group aligned with South Korea has been focusing on users in East Asian...






