
Cyber Security
“`html A vulnerability concerning information leakage in M-Files Server allows verified attackers to intercept and reuse session tokens belonging to active users, potentially granting unauthorized entry to sensitive document management systems. This defect,...

Cyber Security
“`html A significant vulnerability in LangChain’s fundamental library (CVE-2025-68664) permits malicious actors to extract confidential environment variables and potentially execute code via deserialization vulnerabilities. Identified by a researcher from Cyata...

Cyber Security
“`html Microsoft has revealed hardware-accelerated BitLocker, a notable security upgrade aimed at eliminating performance restrictions caused by encryption on contemporary high-speed NVMe drives. This innovative technology tackles the increasing worries...
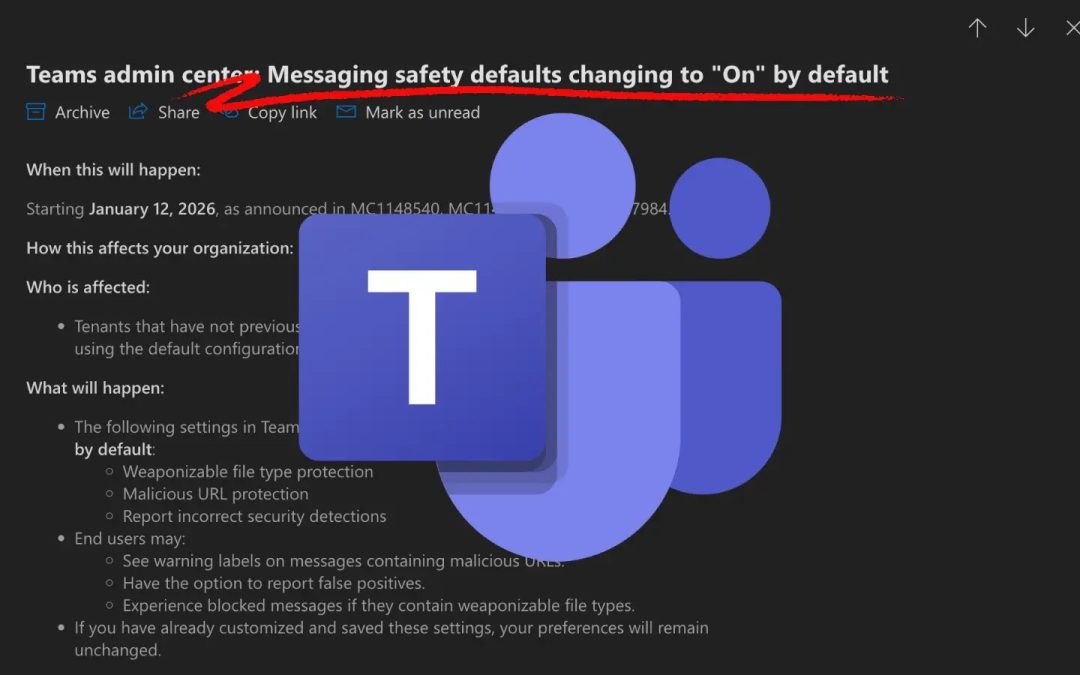
Cyber Security
“`html Microsoft is enhancing the security framework of corporate collaboration by automatically activating essential messaging safety features within Microsoft Teams. According to a recent administrative update, the corporation will set several protective...

Cyber Security
“`html BlindEagle, a South American threat faction, has initiated a sophisticated operation targeting Colombian governmental bodies, showcasing a concerning advancement in attack strategies. In the beginning of September 2025, the faction aimed at a governmental...






