
Cyber Security
“`html In less than a week after remedying a critical Remote Code Execution (RCE) vulnerability, the React team has revealed three further security flaws impacting React Server Components (RSC). While attempting to circumvent the safeguards for the earlier...

Cyber Security
“`html Crucial security patches for Acrobat and Reader have been released, addressing numerous vulnerabilities that could permit attackers to execute arbitrary code and circumvent vital security measures. On December 9, 2025, Adobe released security bulletin...

Cyber Security
“`html Microsoft has issued critical security patches to tackle a zero-day flaw in the Windows Cloud Files Mini Filter Driver (cldflt.sys) that is currently being leveraged for malicious purposes. Designated with the identifier CVE-2025-62221, this privilege...

Cyber Security
“`html The Indian authorities are presently reviewing a controversial suggestion from the telecommunications sector that would require smartphone manufacturers to activate “always-on” satellite location tracking. This initiative has ignited considerable dissent...
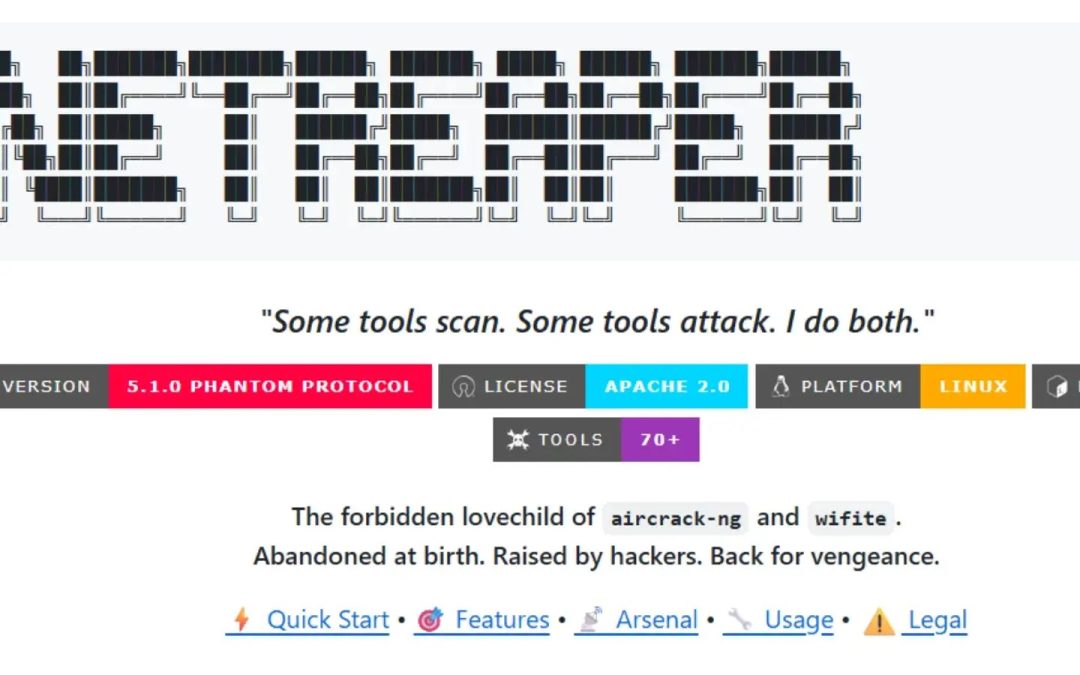
Cyber Security
“`html A comprehensive offensive security toolkit, NETREAPER, created by OFFTRACKMEDIA Studios, amalgamates more than 70 penetration testing tools into a single, intuitive command-line interface. This advancement eradicates the disorder of managing multiple...






