
Cyber Security
“`html A perilous new Android banking malware titled FvncBot was first detected on November 25, 2025. This malicious software is crafted to expropriate sensitive financial data by recording keystrokes, capturing screens, and injecting counterfeit login...

Cyber Security
“`html Experts in security from the SAFA group have revealed four kernel heap overflow weaknesses in Avast Antivirus, all linked to the aswSnx kernel driver. The vulnerabilities, currently cataloged as CVE-2025-13032, might enable a local attacker to elevate...
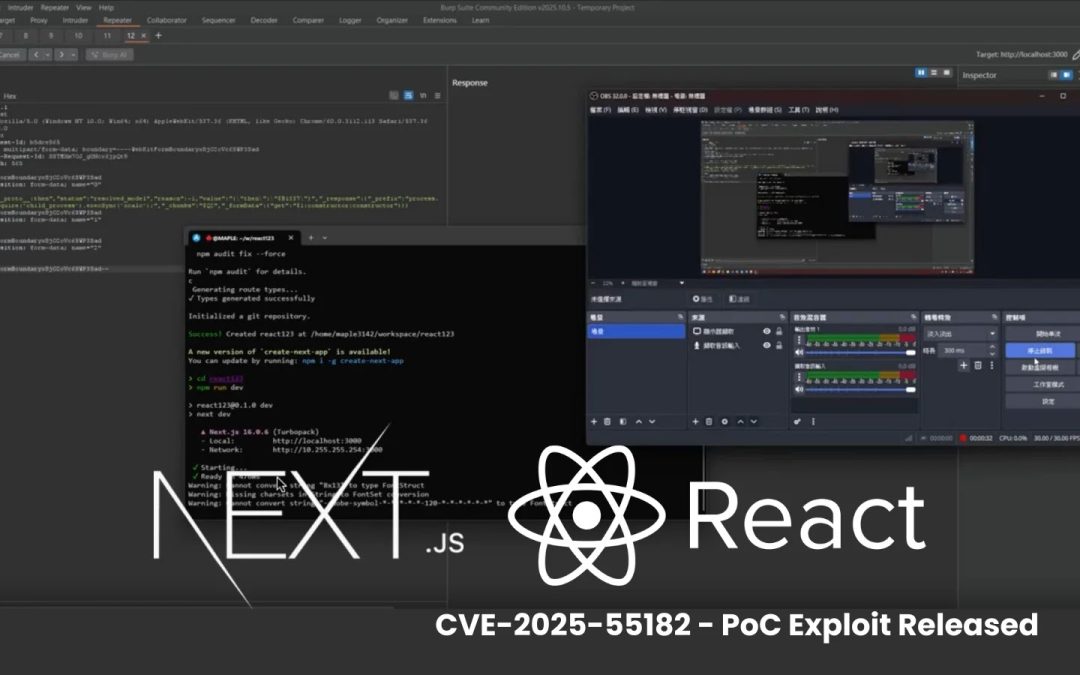
Cyber Security
“`html A proof-of-concept (PoC) exploit pertaining to CVE-2025-55182, a critical remote code execution (RCE) vulnerability in React Server Components, emerged publicly this week, raising concerns for developers globally. Referred to as “React2Shell” by several...

Cyber Security
“`html India has introduced a compulsory SIM-binding regulation for messaging platforms, including WhatsApp, Telegram, Signal, Snapchat, and others. The Department of Telecommunications released an order on November 28 requiring all app-based communication...

Cyber Security
“`html Google has officially elevated Chrome 143 to the Stable channel, releasing version 143.0.7499.40 for Linux and 143.0.7499.40/41 for Windows and Mac. This crucial upgrade tackles 13 security vulnerabilities, comprising several high-severity flaws that...






