
Cyber Security
“`html IBM has issued significant security patches that address two critical vulnerabilities in its AIX operating system, which could permit remote intruders to execute arbitrary commands on vulnerable systems. Both weaknesses arise from inadequate process...
Cyber Security
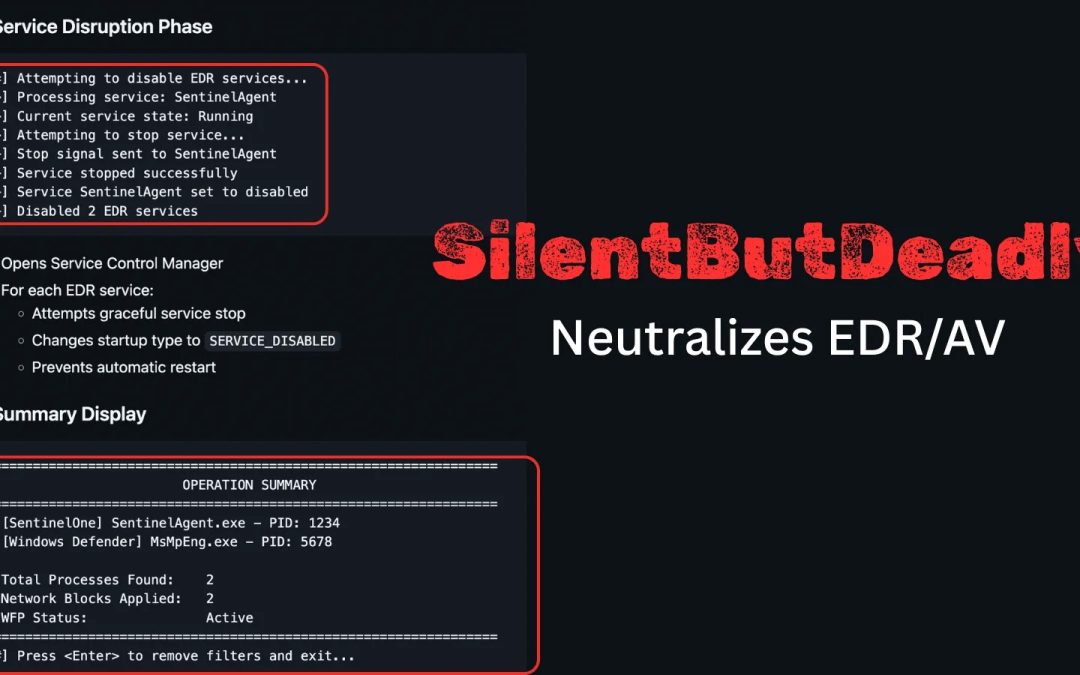
“`html A recent open-source application named SilentButDeadly has surfaced, designed to interfere with Endpoint Detection and Response (EDR) and antivirus (AV) programs by disrupting their network interactions. Created by security analyst Ryan Framiñán, the...

Cyber Security
“`html A critical security vulnerability in Cisco Catalyst Center Virtual Appliance has been uncovered, permitting attackers with minimal access to achieve full administrative control over the vulnerable systems. The flaw, designated as CVE-2025-20341, affects...

Cyber Security
“`html Fortinet has released an urgent notification cautioning about a serious flaw in its FortiWeb web application firewall (WAF) solution, which cybercriminals are currently exploiting in the field. Named CVE-2025-64446, the vulnerability arises from...

Cyber Security
“`html Threat actors are currently exploiting a significant authentication bypass weakness in Fortinet’s FortiWeb web application firewall (WAF) across the globe, urging defenders to enhance their alertness. Investigators at watchTowr Labs have countered by...






