
Cyber Security
“`html The digital landscape consistently grapples with increasing risks related to software vulnerabilities, data leaks, and cyber supply chain intrusions. As organizations depend more on open-source software, external code, and cloud-based applications, the...

Cyber Security
“`html Microsoft Defender for Endpoint is presently facing a glitch that produces erroneous alerts regarding outdated Basic Input/Output System (BIOS) versions, particularly impacting Dell devices. This concern, monitored by Microsoft under the reference ID...

Cyber Security
“`html Ukrainian intelligence agencies have released an urgent alert concerning a complex malware operation directed at governmental and essential infrastructure sectors utilizing weaponized XLL files disseminated via compressed folders. This nefarious campaign...

Cyber Security
“`html At the end of September 2025, the Cybersecurity and Infrastructure Security Agency (CISA) released a public warning regarding the active exploitation of a severe command injection weakness labeled as CVE-2025-59689 in Libraesva Email Security Gateway...
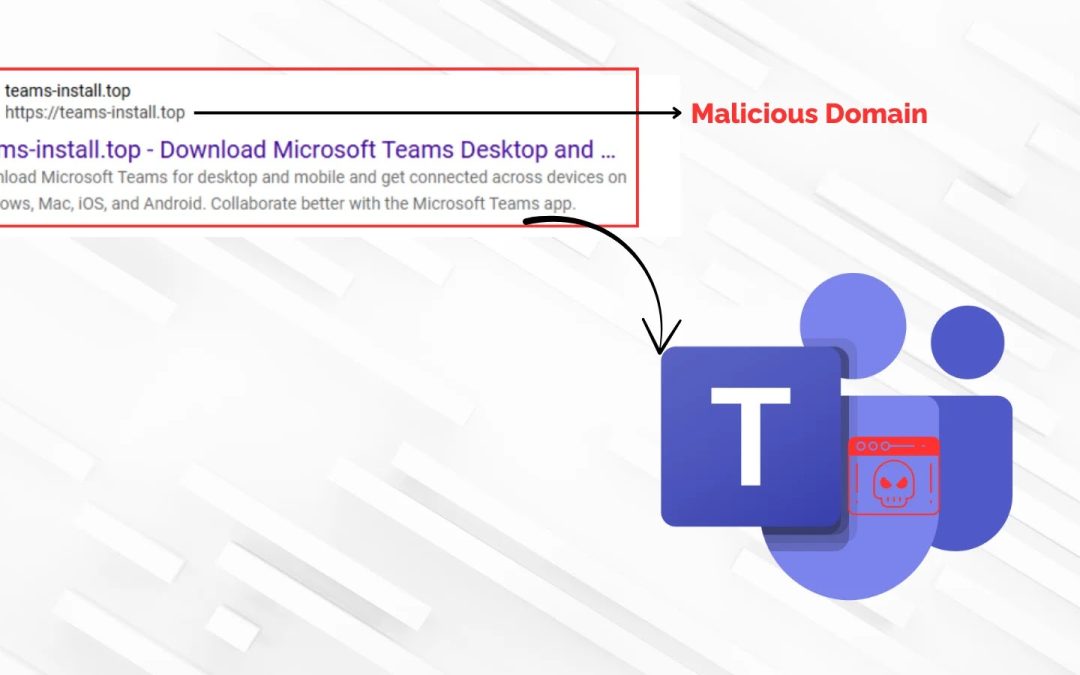
Cyber Security
“`html An advanced cyber initiative is taking advantage of the confidence users have in well-known collaborative software, deceiving them into installing a compromised version of Microsoft Teams to secure remote access to their systems. Malicious actors are...






