
Cyber Security
“`html This week in cybersecurity experienced a relentless series of significant disclosures and record-breaking attack volumes, emphasizing the mounting difficulties faced by defenders. Taking center stage was Google’s urgent fix for yet another actively...

Cyber Security
“`html A sophisticated malvertising effort is utilizing counterfeit Microsoft Teams installers to infiltrate corporate networks, exploiting tainted search engine results and misused code-signing certificates to distribute the Oyster backdoor malware. The assault...

Cyber Security
“`html A complex new menace has surfaced in the cybersecurity realm, representing a considerable progression in malware creation. The LAMEHUG malware lineage, initially recognized by CERT-UA in July 2025, signifies a troubling advance in cyber attack strategies...

Cyber Security
“`html Living Security, a worldwide authority in Human Risk Management (HRM), has today revealed the complete roster of speakers for the Human Risk Management Conference (HRMCon 2025), occurring on October 20, 2025, at Austin’s Q2 Stadium and accessible...
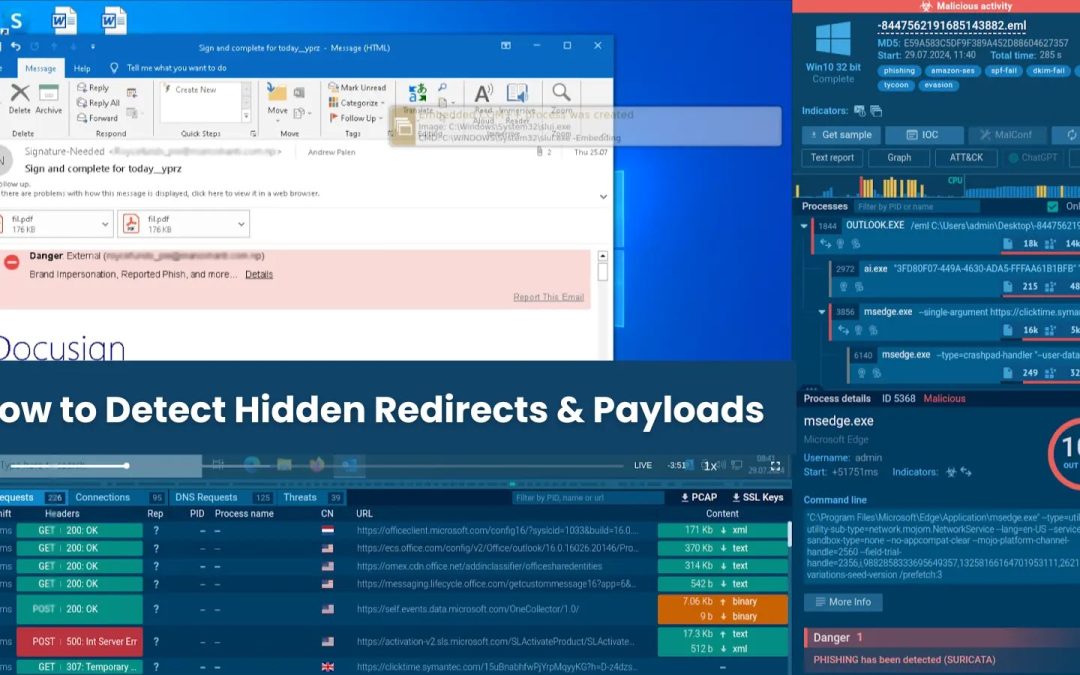
Cyber Security
“`html Phishing operations are becoming increasingly difficult to detect, at times lurking in files you’d never anticipate. ANY.RUN’s cybersecurity experts recently identified a specific instance: a harmful SVG masquerading as a PDF, situated on a credible...






