Cyber Security
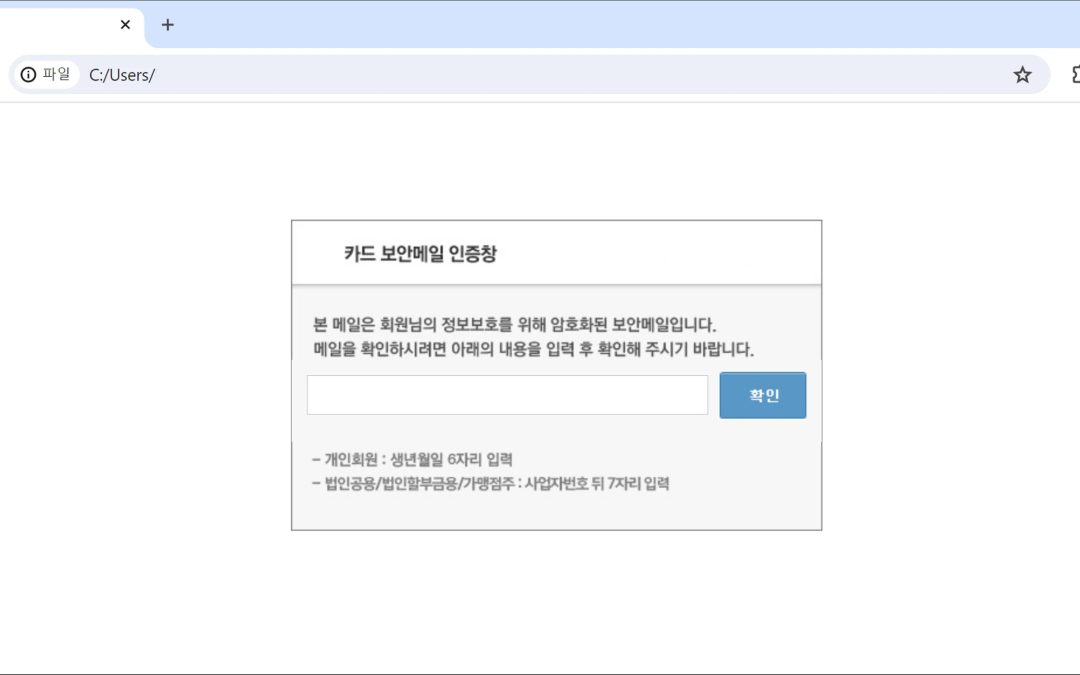
“`html Cybercriminals have advanced their social manipulation strategies with a complex malware initiative that takes advantage of users’ confidence in financial institutions. The newest menace entails a malicious LNK file posing as a credit card security email...
Cyber Security
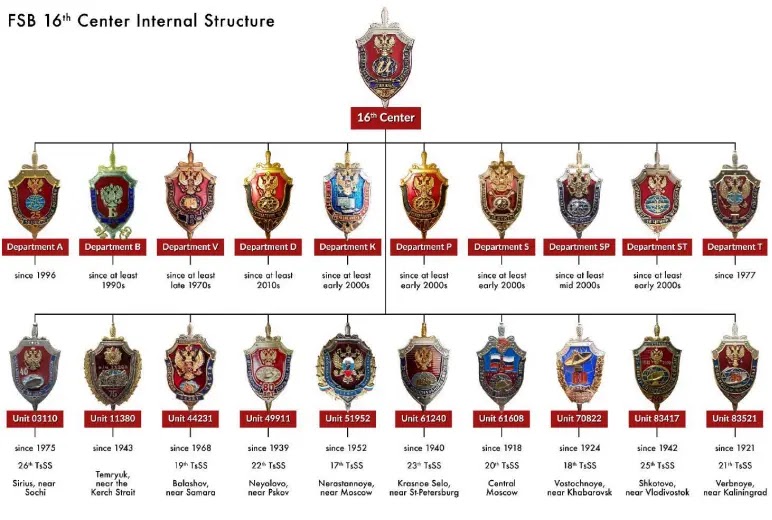
A revolutionary study has unveiled the hidden workings of one of Russia’s most secretive intelligence endeavors, disclosing remarkable insights about the Federal Security Service’s (FSB) 16th Center and its vast signals intelligence network. The analysis,...
Cyber Security
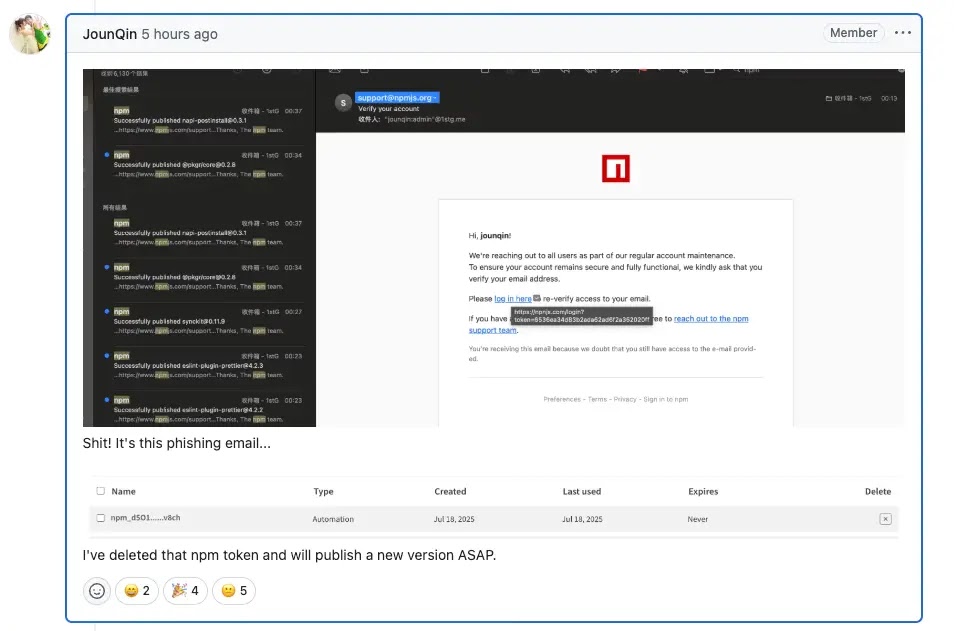
An advanced supply chain assault has compromised numerous extensively-utilized npm packages, such as eslint-config-prettier and eslint-plugin-prettier, after malicious actors successfully acquired maintainer authentication tokens via a focused phishing scheme. The...

Cyber Security
“`html The past week has been bustling with security notifications. Google is tackling yet another actively exploited zero-day in Chrome, while VMware has deployed crucial patches for its own array of vulnerabilities. Furthermore, we will dissect the techniques...

Cyber Security
An intricate phishing initiative directed at Turkish defense and aerospace companies has surfaced, delivering a highly stealthy variant of the Snake Keylogger malware through deceptive emails masquerading as TUSAŞ (Turkish Aerospace Industries). The nefarious campaign...






