Cyber Security
Halo Security’s Attack Surface Management Platform Recognized for Outstanding Innovation and Effective Implementation Through The Channel Halo Security has announced today that its attack surface management solution has been awarded the 2025 MSP Today Product of the...
Cyber Security
The Washington Post is undertaking an extensive inquiry into a complex cyber assault that breached the email accounts of several journalists, with cybersecurity professionals and federal agencies scrutinizing evidence that points to the involvement of a foreign...
Cyber Security
Cross-strait tensions have surged into a novel sphere as China and Taiwan partake in extraordinary reciprocal allegations of cyber warfare aimed at vital infrastructure systems. The diplomatic contention has amplified following Taiwan President Lai Ching-te’s...
Cyber Security
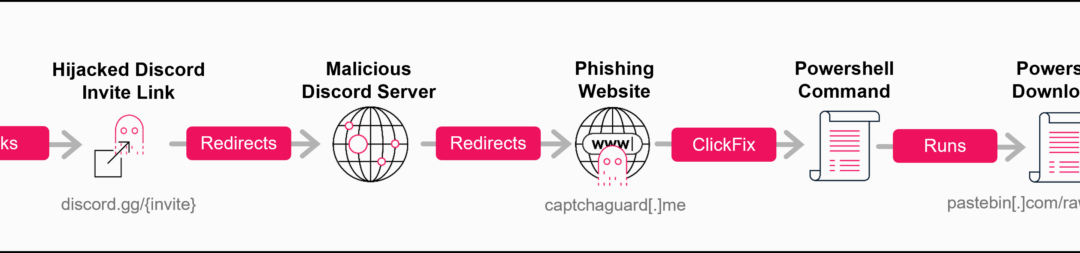
Cybercriminals have uncovered a complex new attack pathway that takes advantage of a pivotal vulnerability in Discord’s invitation framework, permitting them to commandeer obsolete invite links and reroute unwitting users to hazardous servers hosting sophisticated...
Cyber Security
“`html Secure code review is an essential security practice that thoroughly scrutinizes software source code to uncover and rectify security vulnerabilities prior to their deployment in production environments. This detailed assessment acts as a proactive...

