Cyber Security
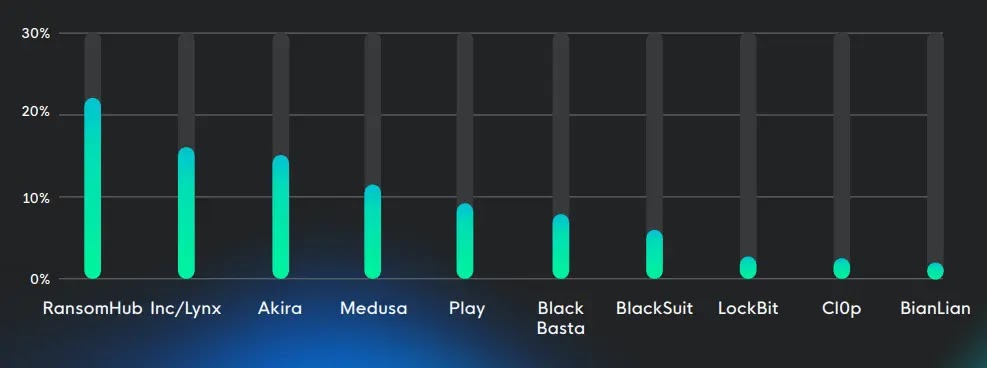
Recent studies uncover ransomware syndicates are hastening encryption timelines while embracing advanced evasion methods and data extortion tactics. According to a 2025 risk analysis by cybersecurity company Huntress, ransomware groups now require just 17 hours on...
Cyber Security
A significant authentication circumvention weakness in SonicWall firewalls, identified as CVE-2024-53704, is currently being actively utilized in the wild, as warned by cybersecurity firms. The spike in assaults comes after the public exposure of a proof-of-concept...
Cyber Security
The escalating impact of artificial intelligence (AI) is making numerous organizations rush to tackle the novel cybersecurity and data privacy concerns generated by the technology, especially as AI is utilized in cloud systems. Apple stands firm in addressing AI’s...

Cyber Security
When discussing cybersecurity, it is often technology that takes the spotlight. Nonetheless, the most effective preventative measures hinge on educating individuals in the use of technology. The initial step for organizations is to provide training to their employees....

Cyber Security
Machine learning (ML) is now actively engaged in the forefront of data security. However, when technological advancements progress swiftly, security frequently becomes a secondary priority. This trend is becoming more evident due to the improvised nature of many...





