
Cyber Security
Observe any article discussing recommended strategies for cybersecurity, and roughly third or fourth item on that list, you’ll come across advice on promptly and consistently implementing patches and updates. Applying patches for identified vulnerabilities is...
Cyber Security
Investigators uncovered a notable software supply chain weakness, leading to an impressive $50,500 reward from a prominent corporation’s bug bounty initiative. The pair’s triumph underscores the increasing significance of ensuring the security of the software...

Cyber Security
Synthetic intelligence (AI) and automated learning (ML) have made their way into the corporate environment. Per the IBM AI in Action 2024 Report, two main categories are adopting AI: Visionaries and scholars. Visionaries are observing quantifiable outcomes, with...

Cyber Security
In the education sector, there was a prevalent occurrence of ransomware incidents in 2024 that garnered considerable attention. A ransomware attack prompted the cancellation of classes at the Freehold Township School District in New Jersey at the start of the year....
Cyber Security
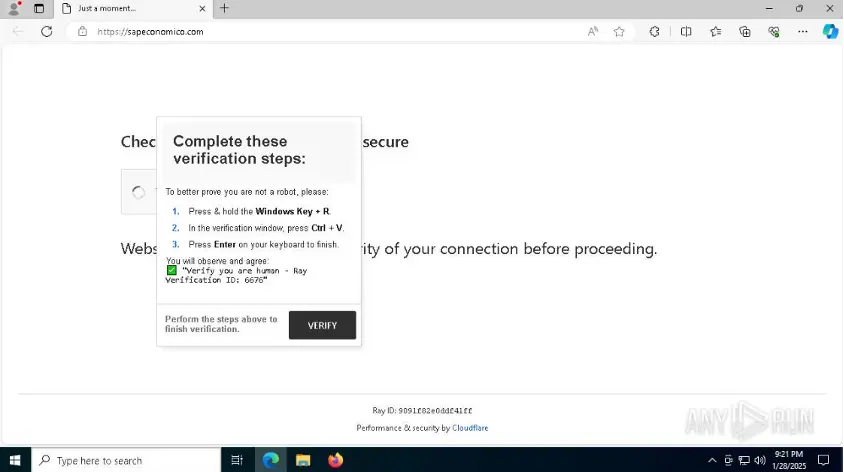
There has been a noticeable surge in the utilization of the NetSupport Remote Access Trojan (RAT) in recent times, as noted by cybersecurity professionals. This malevolent tool enables attackers to acquire complete control over systems that have been compromised. The...






