Cyber Security
Welcome to the current Cybersecurity Bulletin, where you can discover the most recent updates and perspectives from the realm of cybersecurity. Stay enlightened and safeguarded with our prime stories. Remain up-to-date on the most recent risks and progressions in the...
Cyber Security
Threat actors from North Korea, likely associated with BlueNoroff, have initiated multi-stage malware assaults directed at cryptocurrency enterprises, expanding the array of tools utilized to also encompass RustDoor/ThiefBucket and RustBucket campaigns. A threat actor...

Cyber Security
A new Android malware variety known as SpyAgent is currently circulating — and pilfering screenshots as it operates. Leveraging optical character recognition (OCR) technology, the malware aims for cryptocurrency recovery phrases often preserved in snapshots on user...
Cyber Security
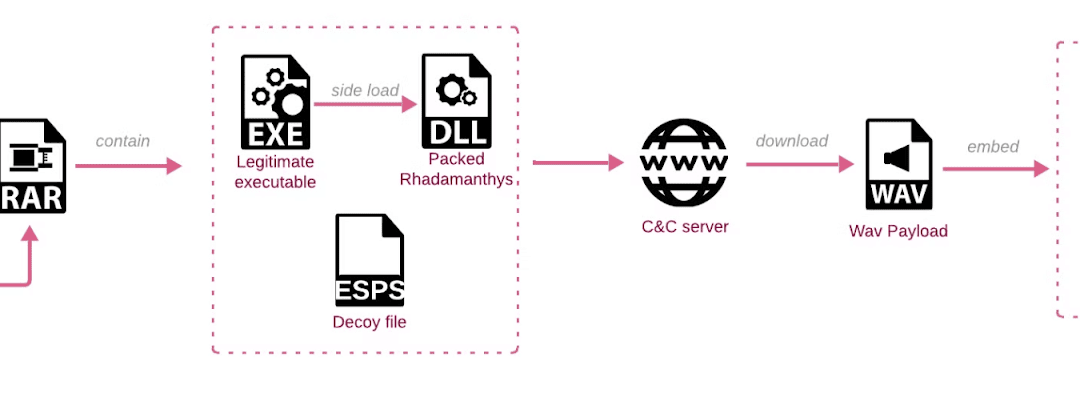
Thieving malware is a form of malicious program crafted to breach computers and extract confidential data. Upon installation, it establishes connection with a command-and-control server managed by cybercriminals, allowing for data theft such as stored passwords and...

Cyber Security
Given the escalating number of cybersecurity breaches on a global scale, organizations dealing with confidential data are particularly susceptible. In the year 2024, the average financial loss resulting from a data breach in the financial sector hit $6.08 million,...




