
Cyber Security
From the outside, organizations are autonomous entities striving to establish their unique presence in the world. However, this perception does not align with reality. Businesses depend on other enterprises to sustain their operations. A grocery store relies on its...

Cyber Security
Currently, organizations are consistently confronted with a variety of rapidly-evolving cyber threats that regularly test the efficiency of their cybersecurity defenses. However, to stay updated, businesses require a preemptive and flexible approach to their security...
Cyber Security
Nominet, the authorized registrar for .uk domain names and one of the biggest country code registries worldwide, has exposed a major cybersecurity breach associated with a recently unearthed zero-day vulnerability in Ivanti’s Virtual Private Network (VPN) software....
Cyber Security
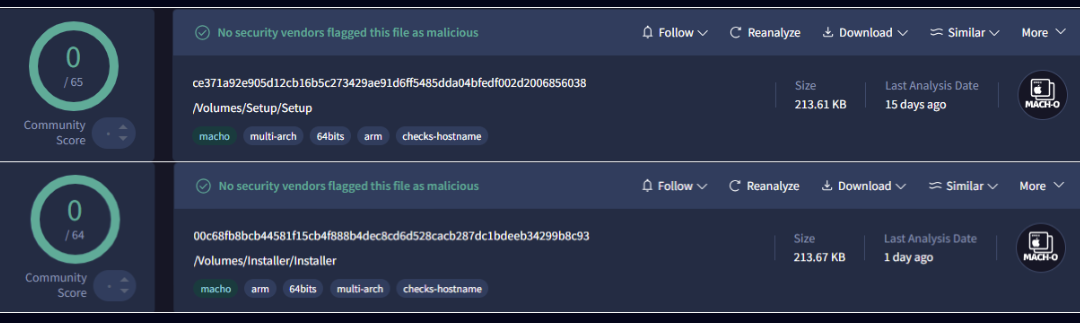
Recently examined were new iterations of the Banshee macOS Stealer prototype that managed to go unnoticed by most antivirus programs, as investigations unveiled that the malicious software utilized a distinctive string encryption method. The encryption mechanism...
Cyber Security
Experts in security have successfully breached the proprietary ACE3 USB-C controller made by Apple. This component, unveiled alongside the iPhone 15 and iPhone 15 Pro, signifies a notable advancement in USB-C technology, managing power delivery and functioning as a...




