Cyber Security
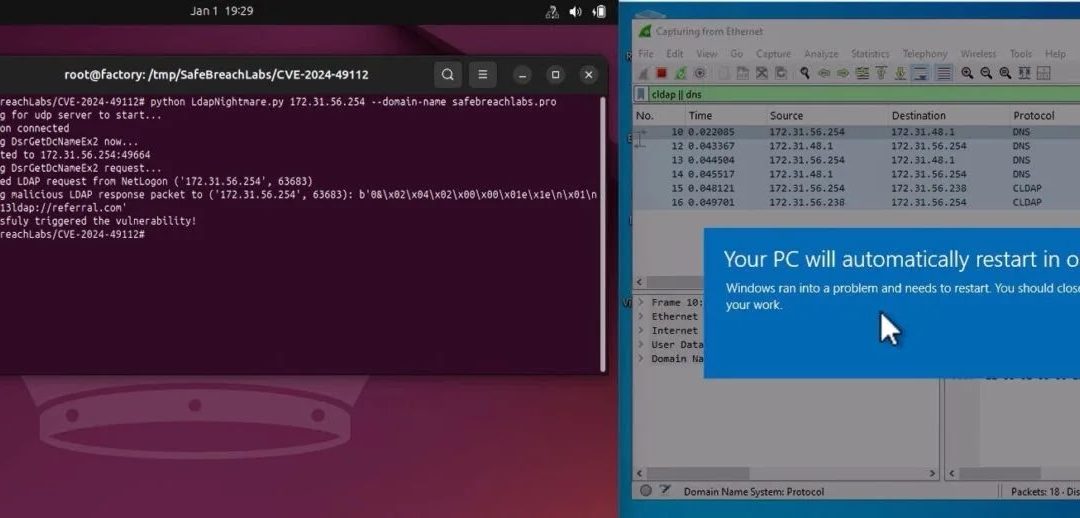
Researchers from SafeBreach Labs disclosed a proof-of-concept (PoC) exploit for a crucial vulnerability found in Windows Lightweight Directory Access Protocol (LDAP) known as CVE-2024-49112. This weakness, which was made public by Microsoft on December 10, 2024, as...

Cyber Security
The top cybersecurity recommendations have had a significant impact on safeguarding data from theft and compromise, both domestically and globally. These recommendations consist of extensive collections of suggested practices, procedures, and principles aimed at...
Cyber Security
Thomas Cook (India) Ltd, a premier travel services provider, has been a target of a cyber intrusion affecting its IT framework, as communicated by the company on Tuesday. This breach has resulted in substantial interruptions in its functions, leading the company to...

Cyber Security
Inquire with CISOs about the reasons behind the cyber skills deficit in their organization, their primary concerns, or the predominant issue encountered in the industry — invariably, budgets will emerge as a topic of discussion, though not necessarily the first point...

Cyber Security
Amid the ongoing struggle against online risks, the Cybersecurity and Infrastructure Security Agency (CISA) has highlighted a crucial weakness in Palo Alto Networks’ PAN-OS software that could render enterprise firewalls vulnerable to remote attacks. The...




