
Cyber Security
Approaching 2025, it becomes crucial to review the advancements and various obstacles encountered in cybersecurity during the past year. Despite witnessing significant progress in security technologies and heightened awareness of emerging cybersecurity risks, 2024...
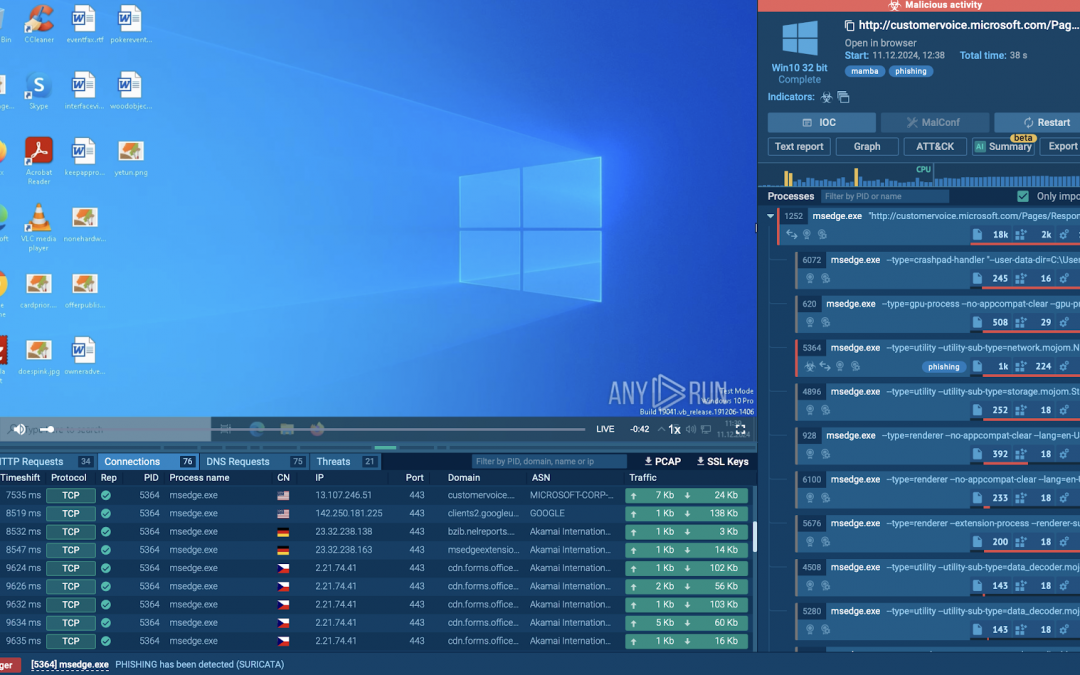
Cyber Security
Phishing schemes are constantly advancing, utilizing genuine platforms and services to trick unwary targets. A strategy highlighted by recent research from ANY.RUN involves the exploitation of Microsoft Dynamics 365. Let’s delve into how malicious actors...

Cyber Security
Over the past few years, significant focus has been placed on the developmental stage of artificial intelligence (AI) technology and its influence on cybersecurity. The potential risks associated with AI-generated attacks remain prevalent and worrisome in numerous...
Cyber Security
An advanced assault campaign utilizing Cloudflare’s Workers service to disseminate harmful applications camouflaged as authentic software. On December 17, 2024, the Ukrainian Computer Emergency Response Team (CERT-UA) disclosed that they had detected various websites...

Cyber Security
Artificial intelligence with generative capabilities (gen AI) is at the forefront of cybersecurity, with red teams playing a crucial role in pinpointing vulnerabilities that others may miss. Considering that the mean price of a data breach has surged to a record $4.88...





