Cyber Security
Amidst the ever-changing threat landscape of today, it is imperative for security executives to make well-informed choices in order to adeptly safeguard their organizations. The “MITRE Engenuity ATT&CK Evaluations: Enterprise” play a vital role as a key resource...

Cyber Security
Expect the unforeseen when inviting a comedian to deliver a keynote address. It was probably unexpected for attendees at Salesforce’s Dreamforce conference to hear John Mulaney criticize the tech innovators in the audience by denying their “trailblazer”...
Cyber Security
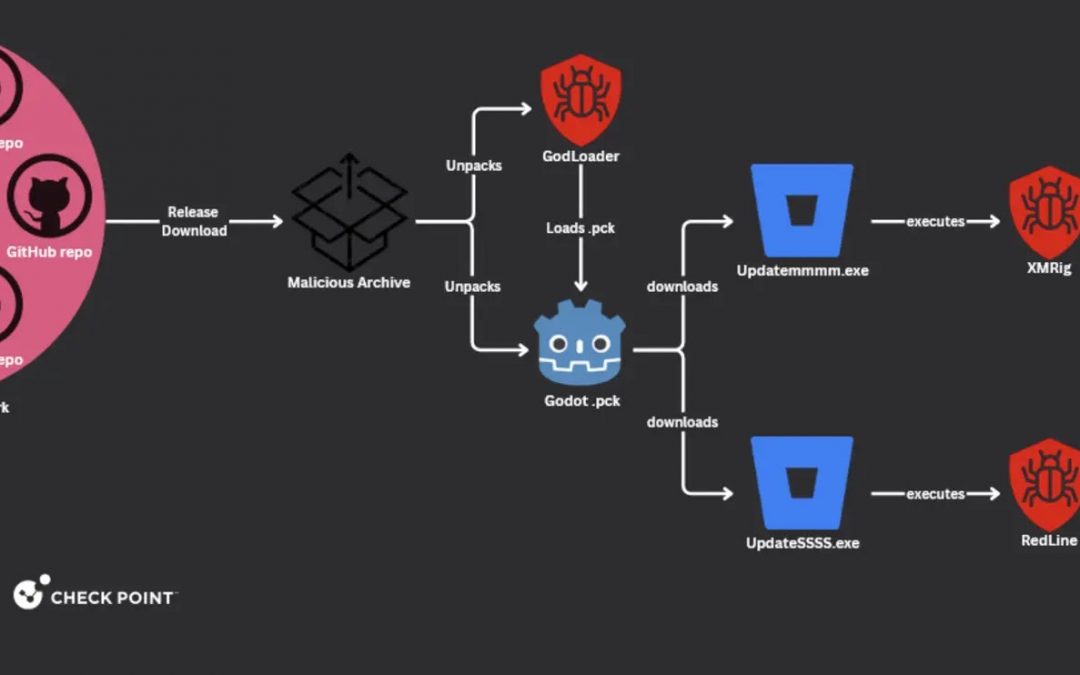
An emerging malicious software, known as GodLoader, has sparked concerns within the cybersecurity community due to its capability to covertly infiltrate devices running on various operating systems, such as Windows, macOS, Linux, Android, and iOS. Unveiled by Check...

Cyber Security
Brief summary This blog post is a continuation of a prior blog post about the PixPirate malware. If you haven’t gone through the initial post yet, we suggest you do so before delving into this additional material. Just a reminder, PixPirate malware is made up of...
Cyber Security
An operation carried out jointly by INTERPOL and AFRIPOL has resulted in the apprehension of 1,006 individuals and the disassembly of 134,089 harmful infrastructures spanning 19 African nations. Termed as Operation Serengeti, the initiative specifically aimed at cyber...



