
Cyber Security
A new Android malware variety known as SpyAgent is currently circulating — and pilfering screenshots as it operates. Leveraging optical character recognition (OCR) technology, the malware aims for cryptocurrency recovery phrases often preserved in snapshots on user...
Cyber Security
Thieving malware is a form of malicious program crafted to breach computers and extract confidential data. Upon installation, it establishes connection with a command-and-control server managed by cybercriminals, allowing for data theft such as stored passwords and...

Cyber Security
Given the escalating number of cybersecurity breaches on a global scale, organizations dealing with confidential data are particularly susceptible. In the year 2024, the average financial loss resulting from a data breach in the financial sector hit $6.08 million,...
Cyber Security
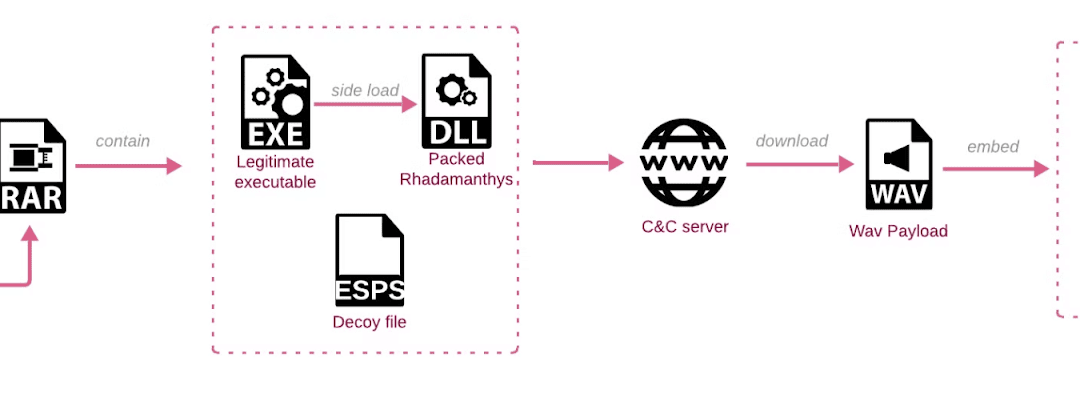
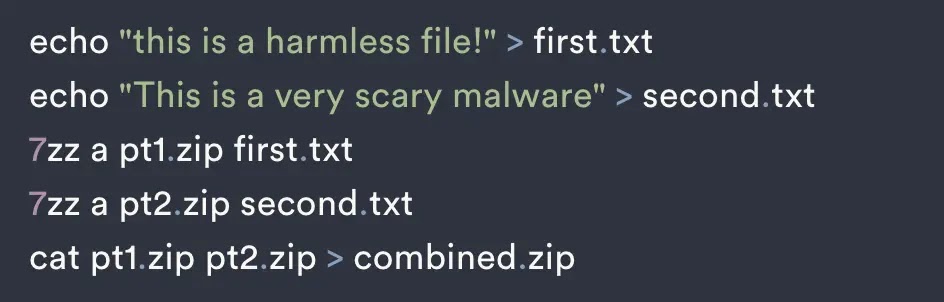
Malevolent hackers employ an advanced evasion scheme known as ZIP bundle merging to target Windows users in particular. This maneuver involves amalgamating multiple ZIP files into a singular archive, complicating the detection of harmful content by security software....

Cyber Security
Ever since its debut in August 2013, Telegram has emerged as the preferred messaging application for individuals who prioritize privacy. To commence utilizing the application, users have the option to register using either their genuine phone number or an undisclosed...






