Cyber Security
Bitdefender Comprehensive Security faces susceptibility to Man-in-the-Middle (MITM) intrusions because of incorrect validation of certificates when performing HTTPS scanning. The existence of this weakness, as detected in multiple CVEs, raises significant concerns for...

Cyber Security
The shortage of staff in cybersecurity — commonly known as the “competency gap” — is causing an increase in the expenses associated with data breaches in recent times, as indicated by ten years of studies conducted by IBM. The IBM Report on Data Breaches...
Cyber Security
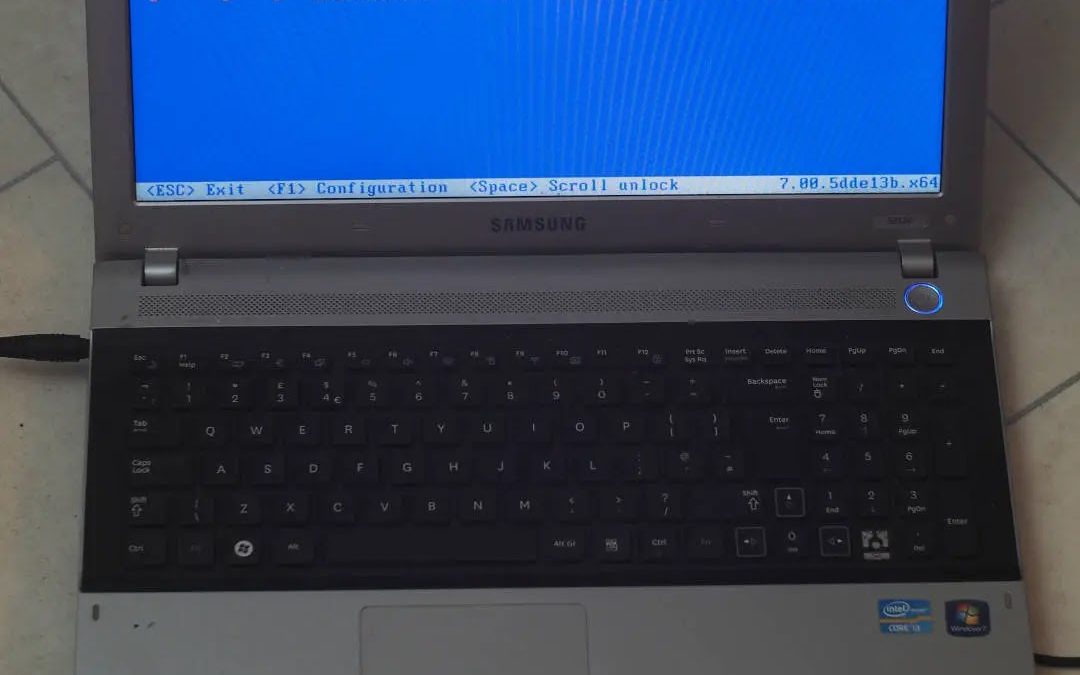
An ordinary grill lighter has been utilized to identify vulnerabilities in laptops, achieving root privileges through a novel method called electromagnetic fault injection (EMFI). Professional hardware researcher David Buchanan showcased this unorthodox technique by...

Cyber Security
Despite our lack of constant awareness, artificial intelligence has permeated various aspects of our lives. Familiar instances include customized recommendations in online shopping, interactive chatbots powered by conversational AI, and many more. In the domain of...
Cyber Security
The initiation of the Android boot sequence begins with the “Boot ROM,” which sets up the “bootloader.” Subsequently, the bootloader loads the kernel, responsible for managing system resources and launching the init process. Recently, cybersecurity experts at...



