
Cyber Security
At a time when companies are increasingly dependent on artificial intelligence (AI) and advanced data capabilities, the importance of IT services is more crucial than ever. Nonetheless, despite the progress in technology, business leaders are growing more dissatisfied...
Cyber Security
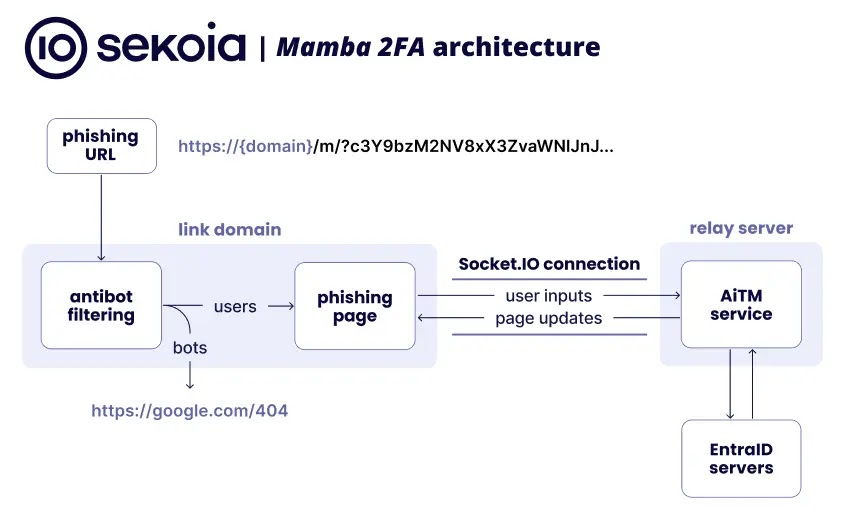
Deceptive cyber schemes known as phishing attacks involve threat actors masquerading as trusted sources to deceive individuals into disclosing sensitive data such as “passwords” or “financial information.” These fraudulent activities are...

Cyber Security
Common clouds currently encompass the majority of enterprise IT environments. As per Statista’s 2024 data, hybrid cloud models are used by 73% of enterprises, while 14% utilize multiple public clouds and 10% opt for a single public cloud solution. The remaining...
Cyber Security
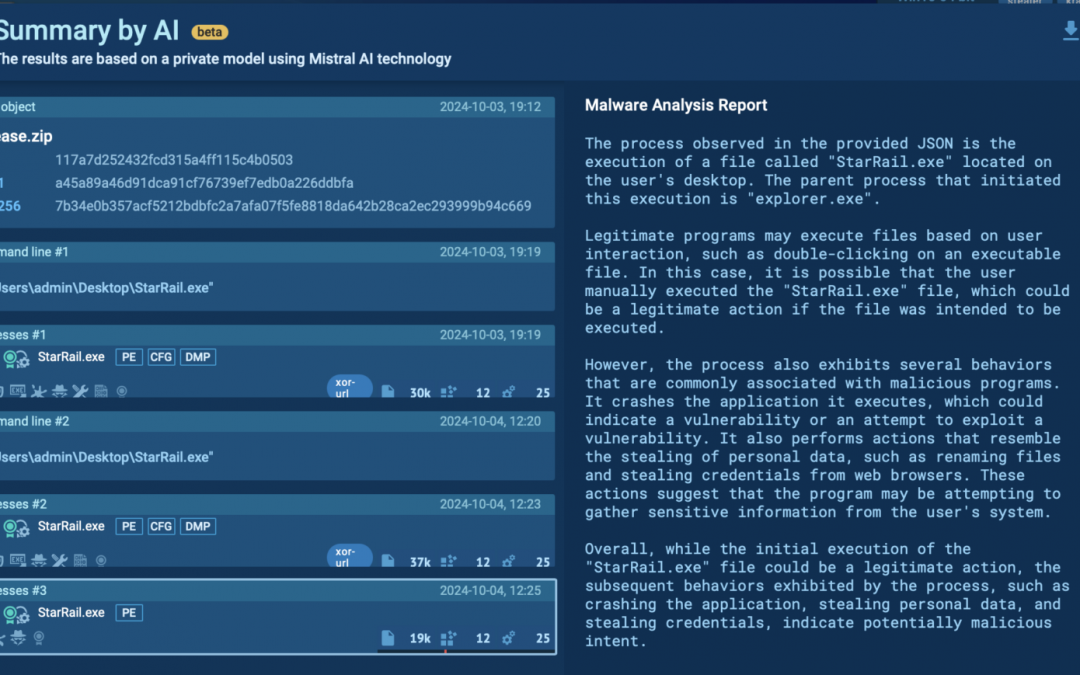
ANY.RUN enhanced its sandbox for analyzing malware by introducing a novel, private AI model, which supersedes the past publicly available ChatGPT-powered aide. The novel model exclusively operates on the proprietary infrastructure, enabling paying customers (Hunter...

Cyber Security
Regarding cybersecurity, the crucial point is the timing of an organization encountering a cyber incident, not a matter of if. Even the most advanced security utilities can’t resist the primary danger: human actions. October is recognized as the Month of...






