
Cyber Security
It’s the 21st yearly Month of Cybersecurity Awareness, and we are addressing various aspects to aid organizations in handling their challenges related to cybersecurity. In this series of brief articles, we are concentrating on distinct job positions beyond...
Cyber Security
Aembit, the AI-powered identity management firm, has today introduced the appointment of Mario Duarte as the chief information security officer (CISO). Duarte, previously the security chief at Snowflake, has joined Aembit with a strong dedication to addressing...

Cyber Security
As mentioned in a recently published article at the 2024 Web Conference, what are known as “phantom domains” enable malicious individuals to seize hyperlinks and exploit the trust of users in familiar websites. The study describes phantom domains as live...
Cyber Security
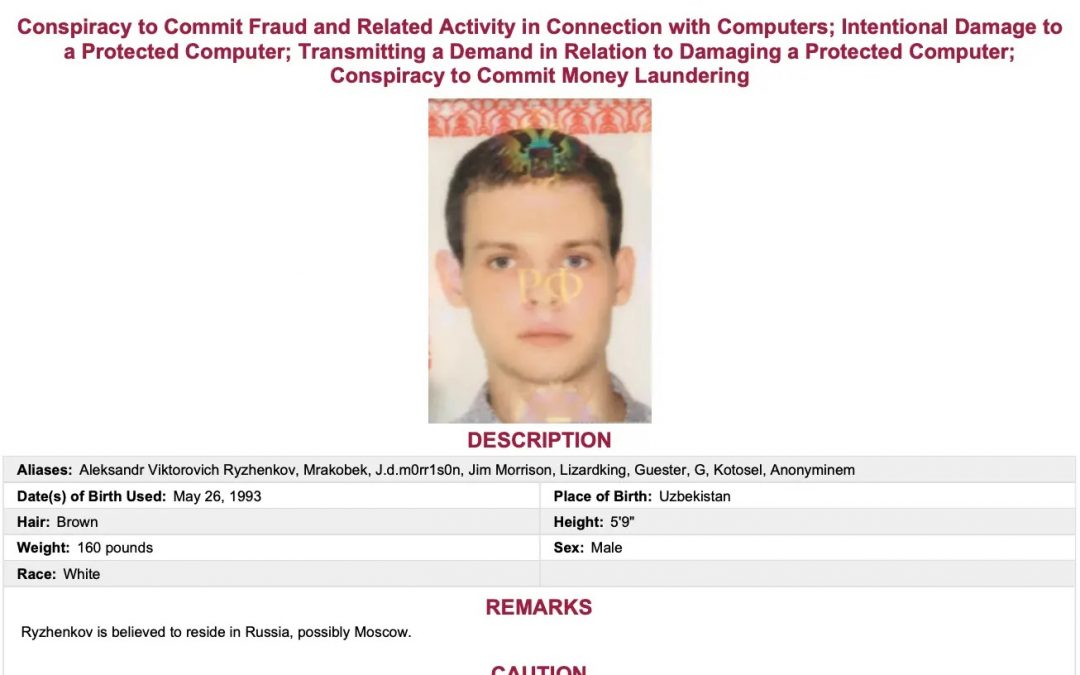
Authorities have identified Aleksandr Viktorovich Ryzhenkov, a Russian national, as a significant figure within the infamous Evil Corp cybercrime organization and as an affiliate involved in the LockBit ransomware scheme. Referred to by the alias...
Cyber Security
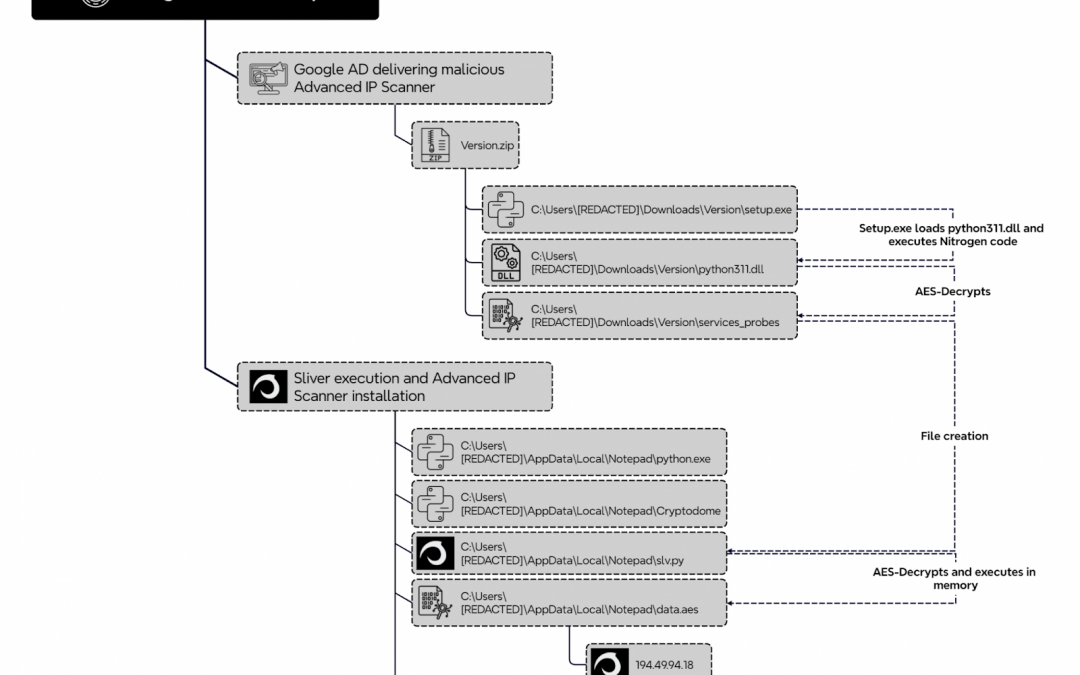
Silver and Cobalt Strike are advanced adversary simulation tools that see widespread usage in penetration testing and red team operations. These tools give security analysts the ability to imitate sophisticated persistent threats through features such as “covert...





