
Cyber Security
AI and ML are becoming increasingly essential in cybersecurity systems. Companies require experts with a solid mix of AI/ML expertise and cybersecurity skills, like Nicole Carignan, the Vice President of Strategic Cyber AI at Darktrace. She possesses a unique...
Cyber Security
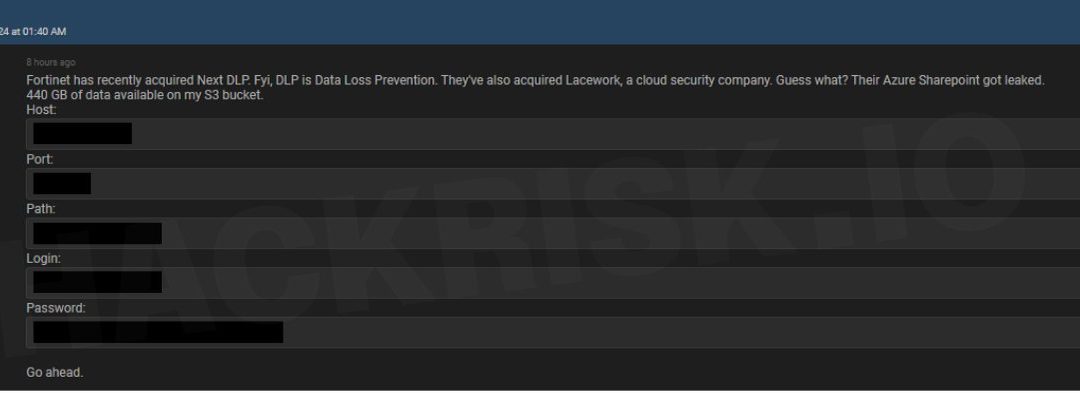
An assailant asserted illicit entry into a third-party cloud-based file-sharing platform utilized by Fortinet. The event purportedly impacted multiple Fortinet clients in the Asia-Pacific locale. “A person gained unauthorized entry to a restricted set of files...
Cyber Security
Cynet disrupted the security vendor market with a cutting-edge All-in-One Cybersecurity Platform that integrates a complete suite of essential capabilities in a single, streamlined solution, supported by expert assistance 24/7. This unified strategy enhances...

Cyber Security
Upon reviewing the recent cybersecurity study conducted by researchers Richard Fang, Rohan Bindu, Akul Gupta, and Daniel Kang, I found myself intrigued. Initially impressed by the capability of ChatGPT 4 to exploit the majority of vulnerabilities within a day, I began...
Cyber Security
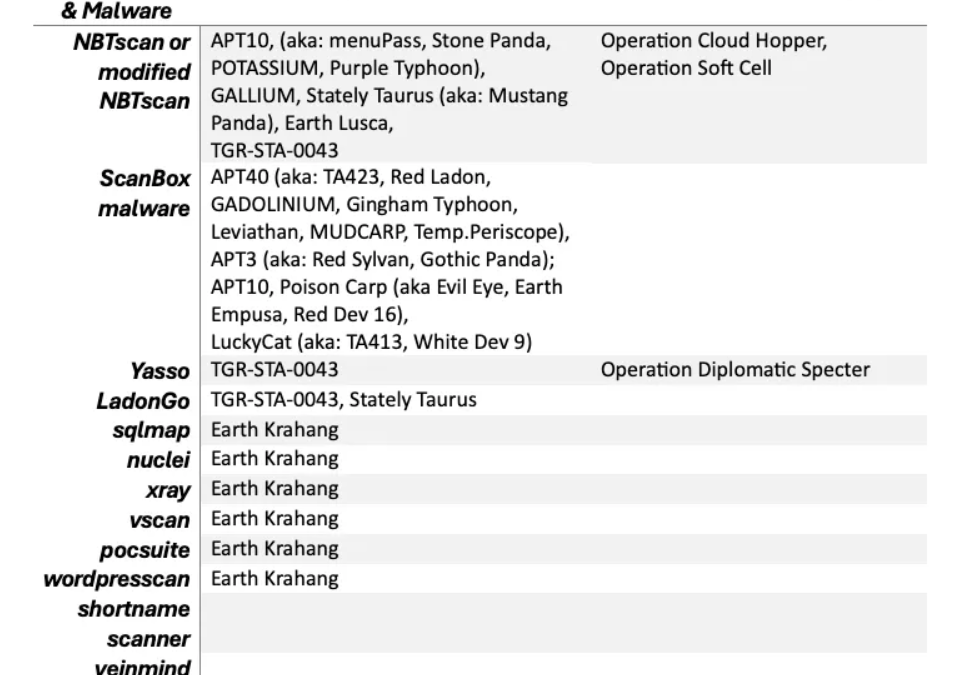
Recently unearthed by cybersecurity experts at Natto Thoughts, it has come to light that Chinese hackers are actively exploiting open-source utilities such as Nmap for carrying out cyber intrusions. Nmap, short for Network Mapper, stands out as a no-cost network...





