Cyber Security
GeoServer is a freely accessible server for distributing geospatial data, and this freely accessible software server is coded in Java. It releases information from any key spatial data source utilizing open criteria. GeoServer is tailored for collaboration and...
Cyber Security
Welcome to the latest issue of our Cybersecurity Bulletin, your primary resource for staying updated on the newest advancements, perspectives, and expert evaluations in the realm of digital defense. In a period where cyber hazards are continually changing, being...
Cyber Security
SonicWall has circulated an urgent security alert concerning a crucial vulnerability (CVE-2024-40766) impacting its firewall products. The company cautions that this flaw in access control is potentially being leveraged in the wild, prompting immediate action from...

Cyber Security
Having artificial intelligence (AI) gaining popularity in various sectors and scenarios, safeguarding against AI-powered software supply chain attacks is now more vital than ever. A recent investigation by SentinelOne uncovered a new ransomware actor called NullBulge....
Cyber Security
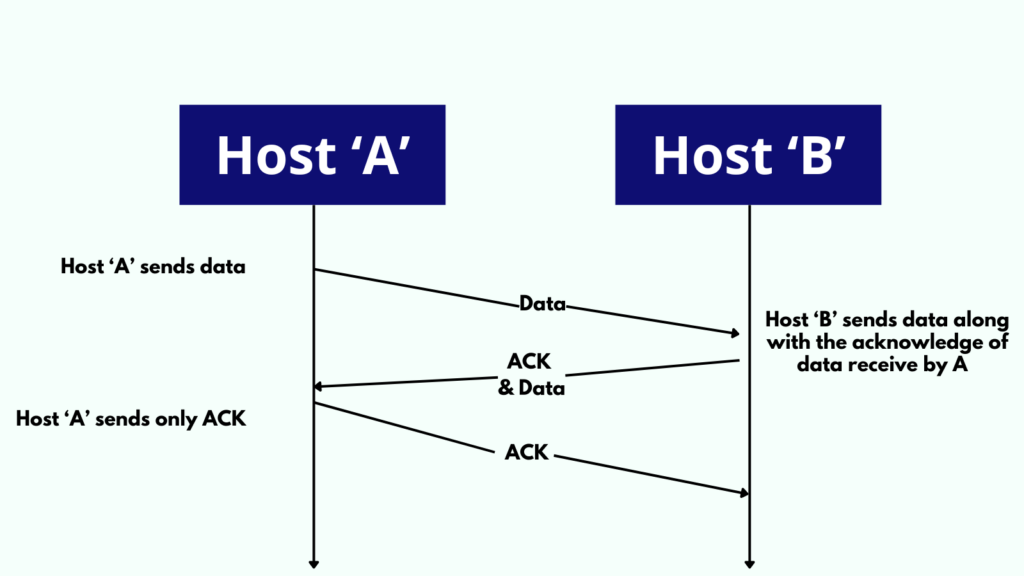
Hitchhiking is a term pertinent to computer networking and cybersecurity. It denotes tactics aimed at enhancing data transmission and, conversely, illicit entry into networks. This piece delves deep into the notion of hitchhiking, delving into its utilization in data...


