
Cyber Security
The disparity in cybersecurity between genders isn’t a recent problem. The shortage of women in the cybersecurity and IT sector has been in the news for many years, even decades. Although there has been some progress, there is still a substantial amount of work...
Cyber Security
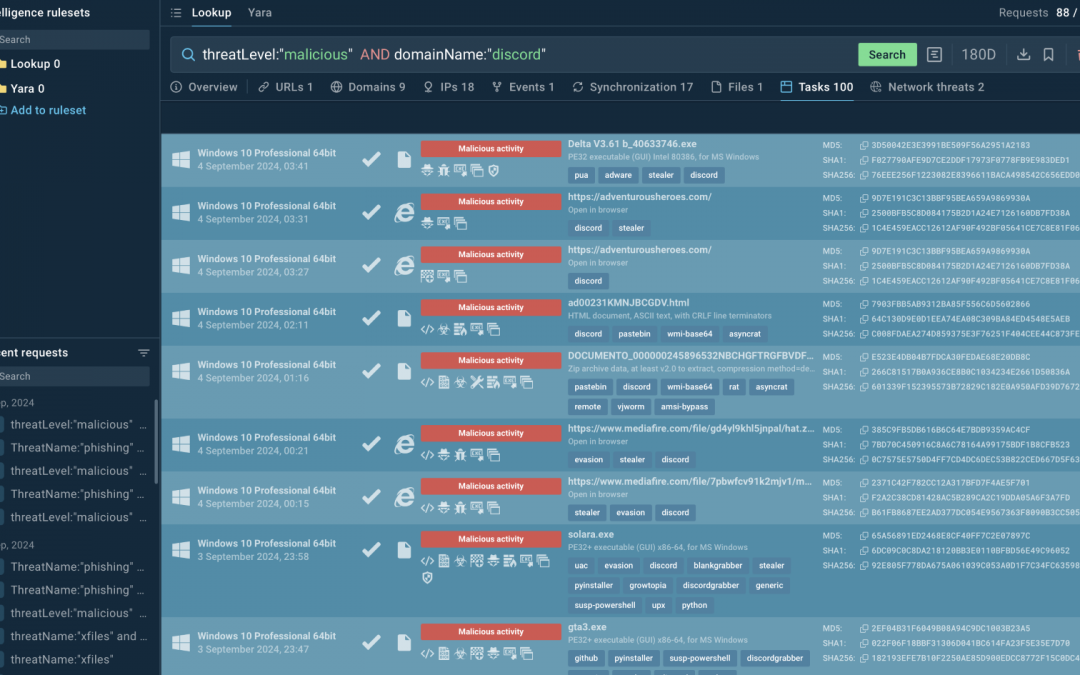
Even though Discord and Telegram stand out as some of the most prevalent communication channels these days, they are not solely utilized for chatting and messaging. It is becoming increasingly prevalent for malevolent actors to exploit these platforms as part of their...
Cyber Security
AI SPERA, a reputable company in Cyber Threat Intelligence (CTI) sector, has attained certification for its flagship search engine product, Criminal IP. This milestone follows the previous year’s accomplishment of PCI DSS v3.2.1 (Payment Card Industry Data...

Cyber Security
For individuals employed in the information security and cybersecurity sectors, the technical consequences of a data breach are commonly comprehended. However, for those outside these technical roles, like executives, operators, and business support units,...
Cyber Security
An important security flaw has been identified in the DAP-2310, specifically impacting Hardware Revision A with Firmware version 1.16RC028. The vulnerability, dubbed “BouncyPufferfish,” was discovered by Hahna Latonick from Dark Wolf Solutions. It exploits...




