Cyber Security
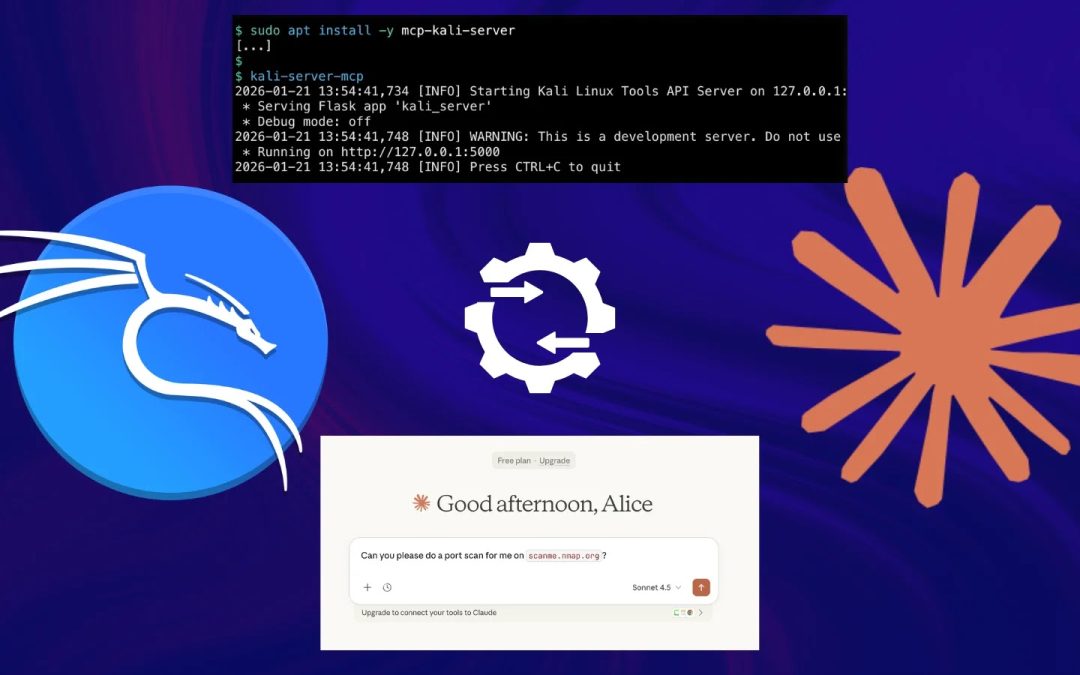
“`html Kali Linux Integrates Claude AI Kali Linux has officially launched a built-in AI-supported penetration testing workflow, allowing security experts to issue commands in natural language via Anthropic’s Claude AI, which are subsequently converted into live...

Cyber Security
“`html GitHub Copilot Exploited A significant AI-driven security flaw in GitHub Codespaces, termed RoguePilot, which allowed intruders to stealthily commandeer a repository by incorporating harmful instructions within a GitHub Issue. The vulnerability,...
Cyber Security
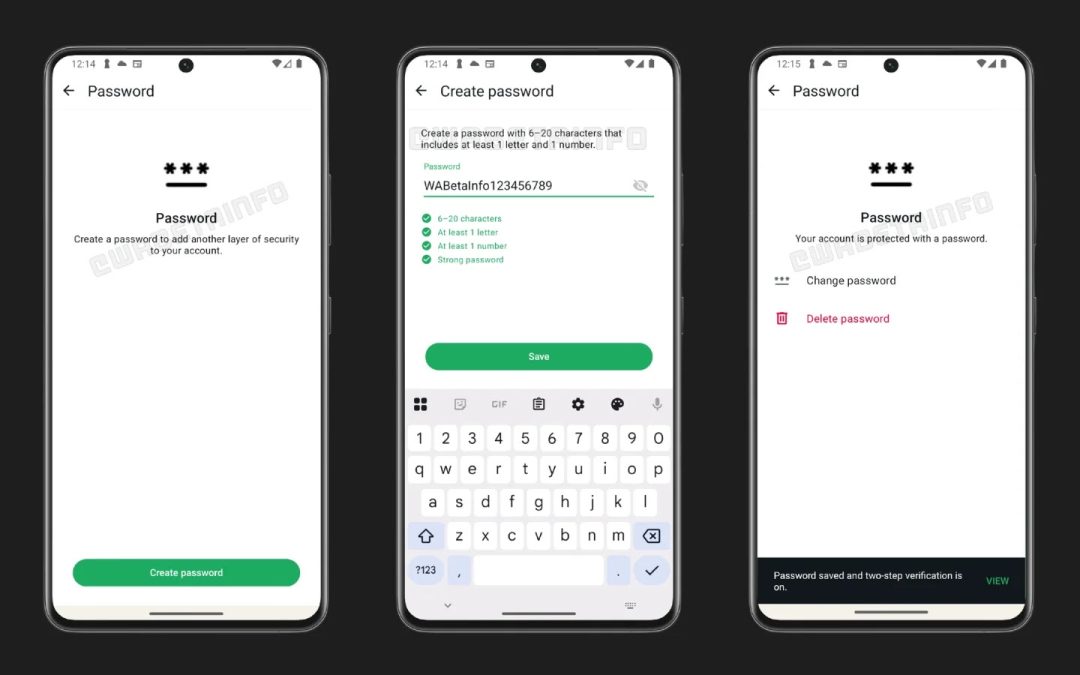
“`html WhatsApp Password Feature (Source: Wabetainfo) WhatsApp has launched a new Android update via the Google Play Beta Program, elevating the version to 2.26.7.8. This update indicates that WhatsApp is actively working on an optional password feature for...

Cyber Security
“`html Google Blocked 1.75 million malicious Apps from Play Store AI-driven security frameworks obstructed over 1.75 million harmful or policy-breaching applications from accessing the Play Store in 2025, bolstering Android security. As per Google’s most recent...

Cyber Security
“`html Hacking Groups Exploit OpenClaw Instances A widespread misuse of OpenClaw, previously referred to as MoltBot and ClawdBot, by various hacking factions to release harmful payloads. OpenClaw, an open-source self-operating AI framework created by Peter...

Cyber Security
“`html PayPal Data Breach PayPal has released an official data breach alert revealing that a programming flaw in its PayPal Working Capital (PPWC) loan application compromised the personally identifiable information (PII) of an undisclosed number of clients for...







