
Cyber Security
“`html Microsoft has revealed hardware-accelerated BitLocker, a notable security upgrade aimed at eliminating performance restrictions caused by encryption on contemporary high-speed NVMe drives. This innovative technology tackles the increasing worries...
Cyber Security
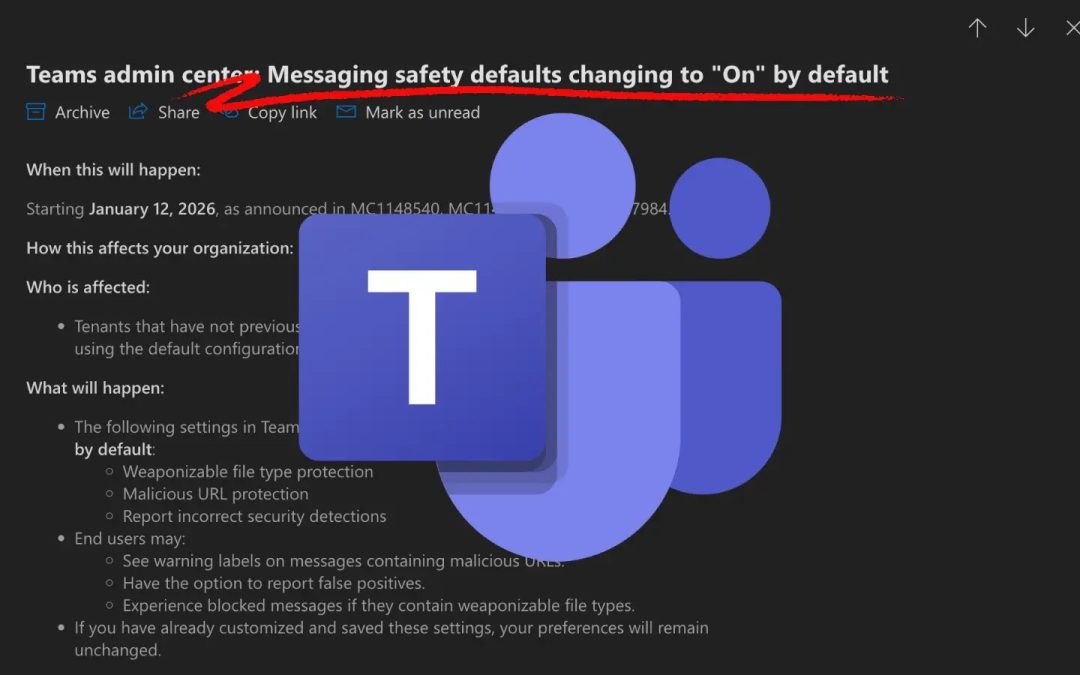
“`html Microsoft is enhancing the security framework of corporate collaboration by automatically activating essential messaging safety features within Microsoft Teams. According to a recent administrative update, the corporation will set several protective...

Cyber Security
“`html BlindEagle, a South American threat faction, has initiated a sophisticated operation targeting Colombian governmental bodies, showcasing a concerning advancement in attack strategies. In the beginning of September 2025, the faction aimed at a governmental...

Cyber Security
“`html During a week that exposed the weaknesses in digital trust, cybersecurity news was dominated by prominent breaches, zero-day vulnerabilities, and audacious nation-state espionage. Cybercriminals asserted that they had stolen usernames, email addresses,...

Cyber Security
“`html Cybersecurity analysts have discovered at least 120 Cisco Secure Email Gateway and Cisco Secure Email and Web Manager devices susceptible to a severe zero-day vulnerability that malicious actors are currently exploiting in the wild. The flaw, listed as...

Cyber Security
“`html In a significant interruption to remote work and collaboration, Microsoft Teams faced a considerable breakdown on Friday, impacting numerous users across various regions. Reports of message delays, unsuccessful message transmissions, and difficulties with...







