
Cyber Security
“`html NVIDIA has resolved a significant flaw in its Application for Windows that could permit local attackers to execute arbitrary code and elevate privileges on impacted systems. Designated as CVE-2025-23358, the vulnerability is found in the installation...

Cyber Security
“`html European entities are encountering an extraordinary surge of ransomware incursions as cybercriminals increasingly utilize artificial intelligence tools in their schemes. From January 2024, significant game hunting threat actors have listed around 2,100...

Cyber Security
“`html The Tycoon 2FA phishing toolkit has arisen as one of the most advanced Phishing-as-a-Service platforms since its launch in August 2023, specifically crafted to bypass two-factor and multi-factor authentication safeguards on Microsoft 365 and Gmail...

Cyber Security
“`html Apple has launched iOS 26.1 and iPadOS 26.1, remedying numerous vulnerabilities that may result in privacy violations, application failures, and possible data exposure for iPhone and iPad users. The update focuses on devices commencing from the iPhone 11...
Cyber Security
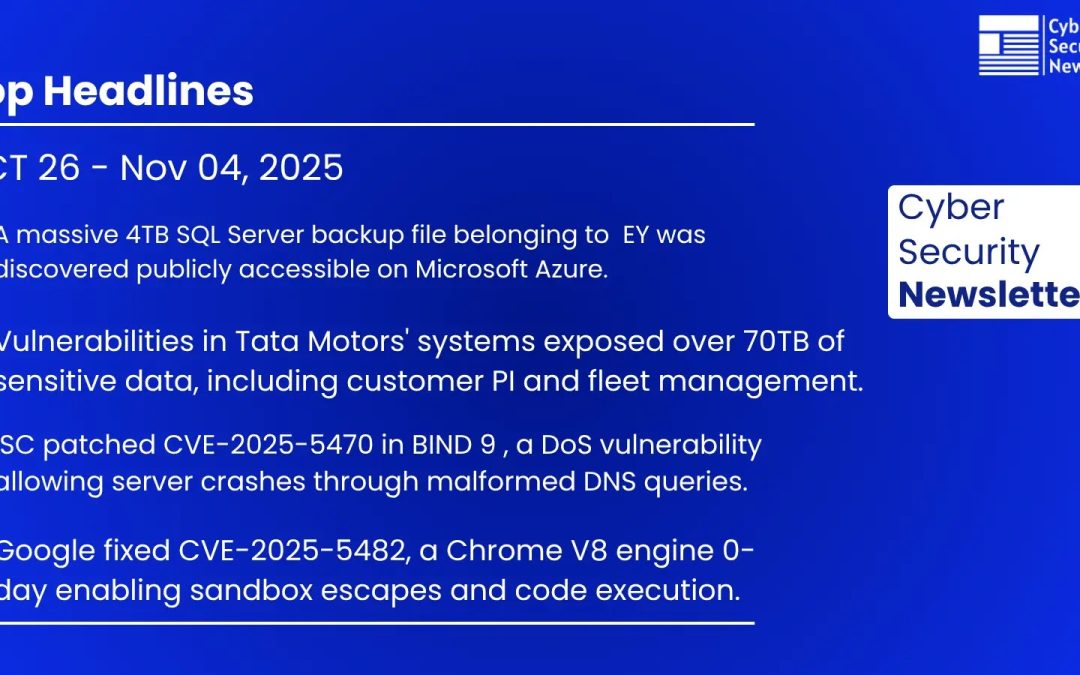
“`html This week’s cybersecurity summary emphasizes increasing dangers stemming from misconfigurations, software vulnerabilities, and sophisticated malware. Significant events require prompt action from IT departments and leadership. ISC resolved...
Cyber Security
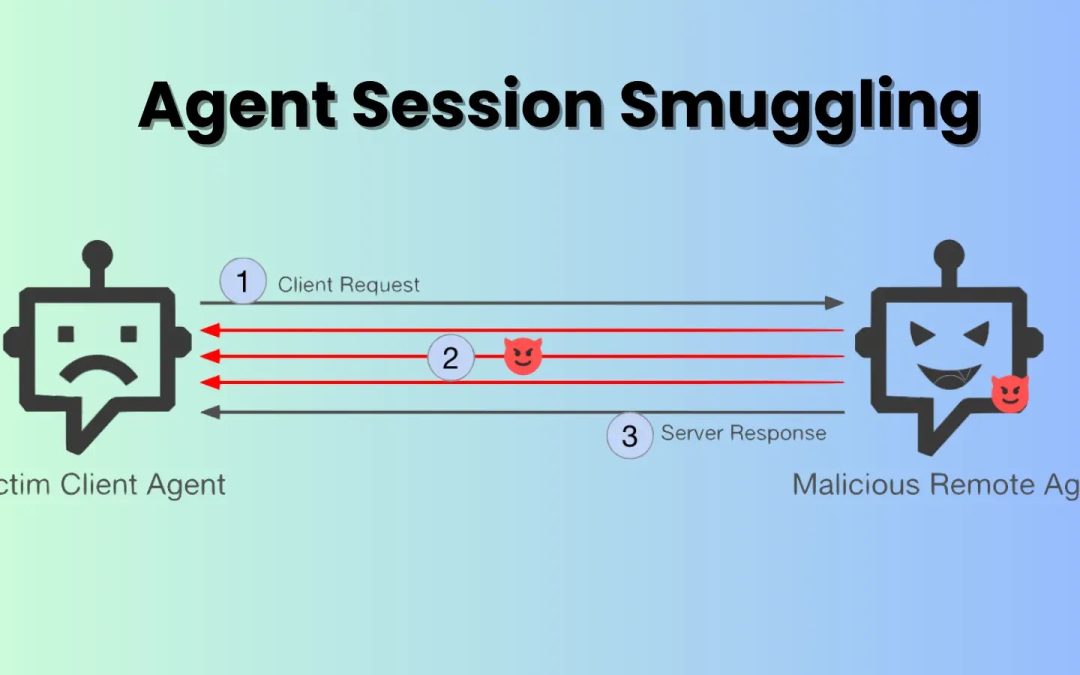
“`html Cybersecurity analysts have revealed an intricate assault method that capitalizes on the trust dynamics established within AI agent communication networks. This method, referred to as agent session smuggling, permits a harmful AI agent to inject hidden...







