
Cyber Security
“`html Ukrainian intelligence agencies have released an urgent alert concerning a complex malware operation directed at governmental and essential infrastructure sectors utilizing weaponized XLL files disseminated via compressed folders. This nefarious campaign...

Cyber Security
“`html At the end of September 2025, the Cybersecurity and Infrastructure Security Agency (CISA) released a public warning regarding the active exploitation of a severe command injection weakness labeled as CVE-2025-59689 in Libraesva Email Security Gateway...
Cyber Security
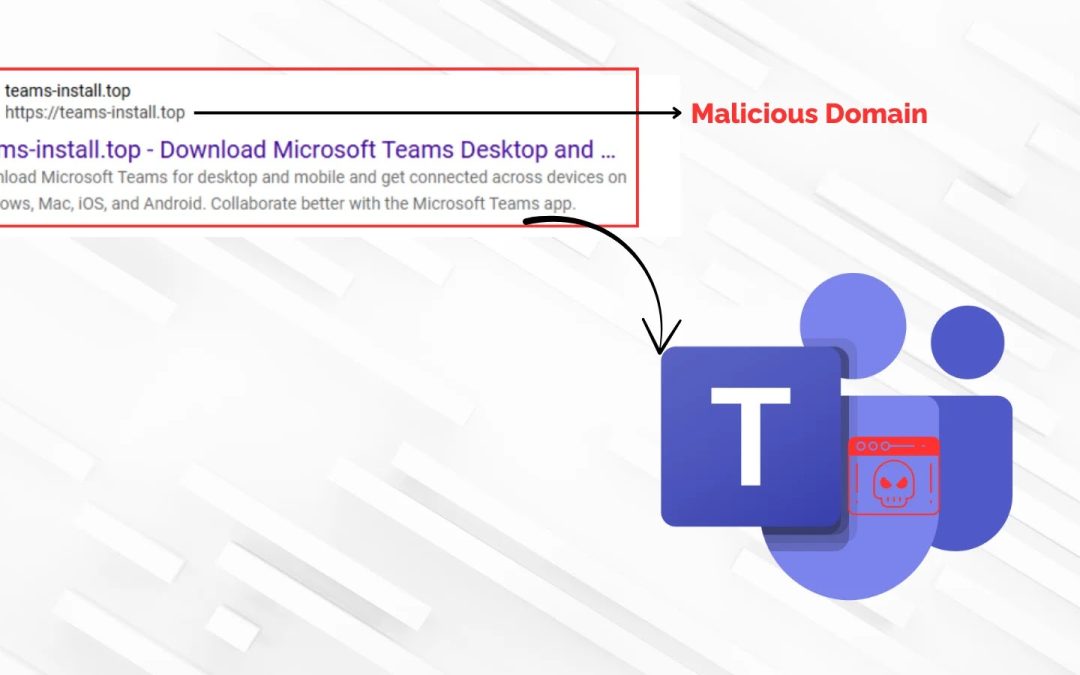
“`html An advanced cyber initiative is taking advantage of the confidence users have in well-known collaborative software, deceiving them into installing a compromised version of Microsoft Teams to secure remote access to their systems. Malicious actors are...

Cyber Security
“`html This week in cybersecurity experienced a relentless series of significant disclosures and record-breaking attack volumes, emphasizing the mounting difficulties faced by defenders. Taking center stage was Google’s urgent fix for yet another actively...

Cyber Security
“`html A sophisticated malvertising effort is utilizing counterfeit Microsoft Teams installers to infiltrate corporate networks, exploiting tainted search engine results and misused code-signing certificates to distribute the Oyster backdoor malware. The assault...

Cyber Security
“`html A complex new menace has surfaced in the cybersecurity realm, representing a considerable progression in malware creation. The LAMEHUG malware lineage, initially recognized by CERT-UA in July 2025, signifies a troubling advance in cyber attack strategies...







