
Cyber Security
“`html Nmap and Wireshark are among the most prominent tools for network penetration testing. Security experts encounter an ever-evolving threat environment, and selecting the appropriate penetration testing tools can significantly impact the distinction between...

Cyber Security
“`html The infamous APT-C-24 threat group, referred to as Sidewinder or Rattlesnake, has evolved its attack strategies by implementing sophisticated LNK file-based phishing initiatives targeting the governmental, energy, military, and mining industries across...

Cyber Security
“`html To guarantee the protection of confidential online information, it entails more than just encryption; it necessitates transparent principles, meticulous design, and documented support. Naman Jain is a Senior Software Development Engineer and an esteemed...

Cyber Security
“`html A remote code execution flaw has been identified in the Cursor AI Code Editor, allowing a malicious code repository to execute code on a user’s device upon automatic opening. The research group at Oasis Security revealed the vulnerability, which...
Cyber Security
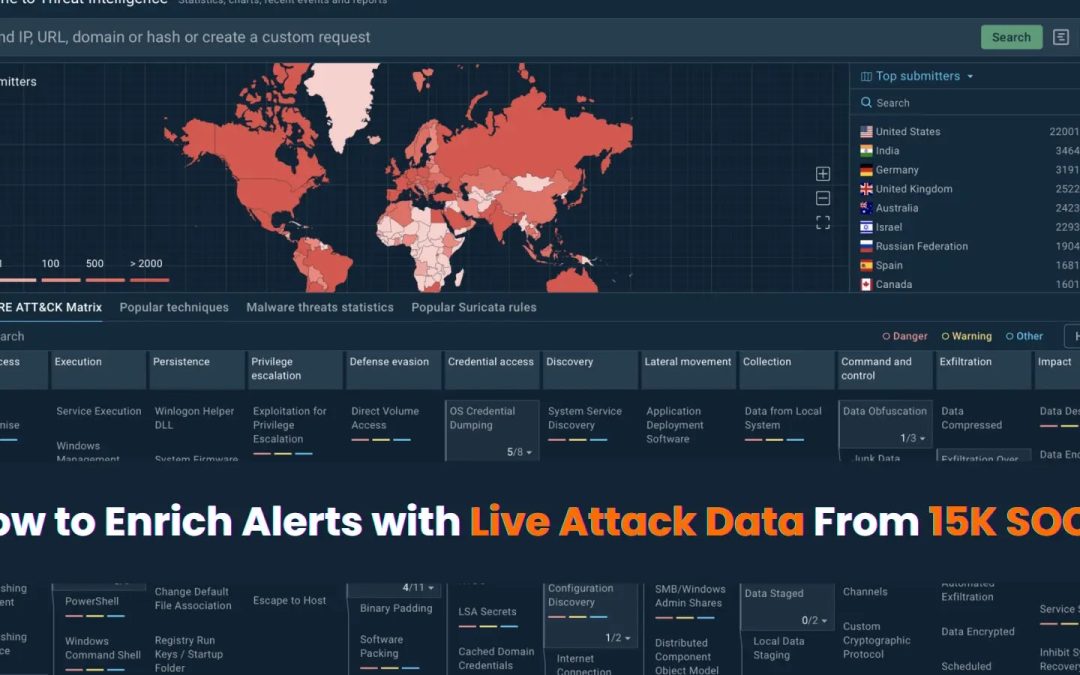
“`html Every SOC analyst understands the irritation. Your SIEM produces hundreds, occasionally thousands of alerts each day. Each alert requires focus, yet with limited time and resources, how do you rank them efficiently? Examining each alert separately leaves...

Cyber Security
“`html A significant security flaw has been identified in Progress OpenEdge, a system for creating and launching business applications. The defect, classified as CVE-2025-7388, permits remote code execution (RCE) and impacts numerous versions of the software,...







