Cyber Security
“`html The cybersecurity realm has undergone a significant transformation as ransomware attackers increasingly focus on Linux and VMware environments, moving away from their historical emphasis on Windows platforms. Recent threat insights reveal that criminal...
Cyber Security
“`html Security analysts have verified the ongoing exploitation of a critical weakness in Wing FTP Server, only one day after the technical specifics were made public. This defect, noted as CVE-2025-47812, has attained the highest CVSS rating of 10.0 and...
Cyber Security
“`html In the current swiftly changing digital landscape, the prevalence and intricacy of cyber threats are escalating, rendering it essential to remain updated on emerging dangers. Our weekly dispatch acts as a crucial reference, providing a summary of relevant...
Cyber Security
“`html Trendyol’s application security division discovered a sequence of bypass methods that make Meta’s Llama Firewall protections ineffective against advanced prompt injection assaults. The results prompt renewed worries regarding the effectiveness of current...
Cyber Security
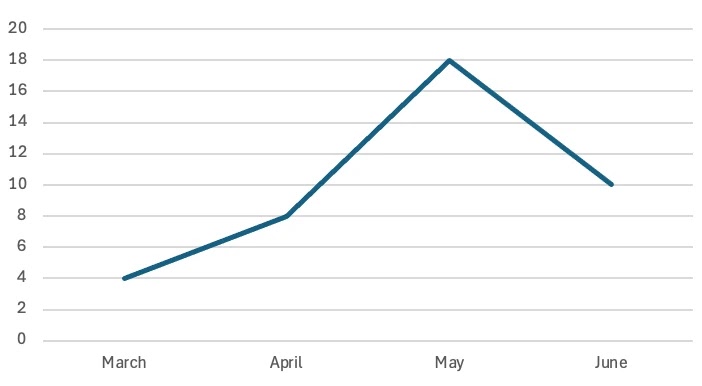
“`html State-sponsored threat actors from Iran have amplified their cyber offensives against essential infrastructure in the United States, witnessing a staggering 133% rise in malicious activity documented during May and June 2025. This intensification aligns...

Cyber Security
“`html A complex new variant of the macOS.ZuRu malware has arisen, aiming at macOS users via a compromised iteration of the widely-used Termius SSH client. This new version, uncovered in late May 2025, signifies a significant advancement in the tactics of threat...






