
Cyber Security
“`html The U.S. Cybersecurity and Infrastructure Security Agency has included this vulnerability in its Known Exploited Vulnerabilities catalog, with a deadline of September 2, 2025, for federal agencies to implement mitigations. WinRAR has unveiled version 7.13...
Cyber Security
“`html In a synchronized global initiative, law enforcement entities adeptly dismantled essential infrastructure associated with the BlackSuit ransomware faction, alternatively recognized as Royal, signifying a considerable triumph in the continuous struggle...

Cyber Security
“`html UAC‑0099, a sophisticated threat actor collective that has been operational since at least 2022, continues to represent a serious cybersecurity hazard through its evolving cyber-espionage initiatives aimed at Ukrainian governmental entities, military...
Cyber Security
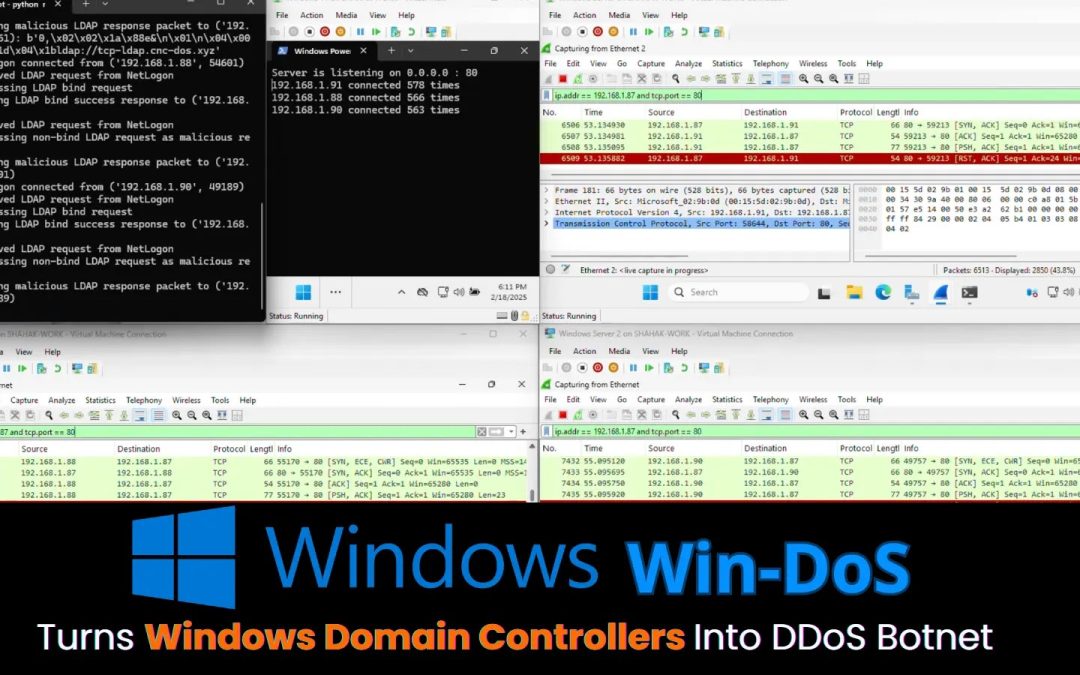
“`html LAS VEGAS — At DEF CON 33 cybersecurity conference, researchers Yair and Shahak Morag from SafeBreach Labs revealed a novel category of denial-of-service (DoS) attacks, termed the “Win-DoS Epidemic.” The pair shared their discoveries, which encompass four...
Cyber Security
“`html Darknet bazaars, functioning outside the grasp of conventional payment processors and legal frameworks, depend on escrow mechanisms to safeguard cryptocurrency exchanges between purchasers and sellers. These mechanisms, incorporating multisignature...

Cyber Security
“`html A complex new malware framework known as CastleBot has surfaced as a considerable danger to cybersecurity, functioning as a Malware-as-a-Service (MaaS) platform that permits cybercriminals to launch various harmful payloads, including infostealers and...







