
Cyber Security
“`html OpenClaw Control Panels Unveiled A significant security breach in the swiftly evolving “agentic AI” landscape has rendered countless personal and corporate AI assistants entirely vulnerable to the public internet. Recent findings disclosed today by the...

Cyber Security
“`html An advanced phishing scheme is presently targeting Apple Pay users, employing fraudulent emails and telephone calls to extract private financial data. The assault usually initiates with a message that seems somewhat familiar, showcasing the official Apple...
Cyber Security
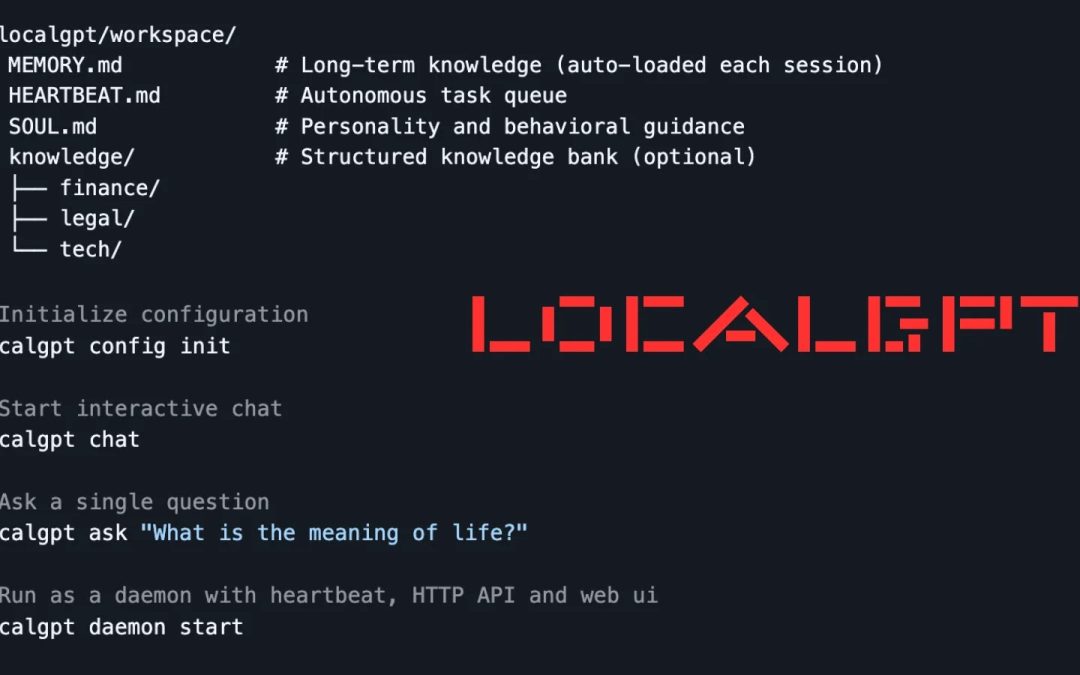
“`html LocalGPT In a time where AI assistants like ChatGPT and Claude prevail in cloud ecosystems, risking user data to remote invasions, a novel Rust-based utility known as LocalGPT offers a fortress-like alternative. Created as a single ~27MB executable,...

Cyber Security
“`html Claude Opus 4.6 Released Anthropic’s most recent AI model autonomously detects significant flaws in legacy codebases, amplifying the stakes for both defenders and adversaries. On February 5, 2026, Anthropic launched Claude Opus 4.6, boasting markedly...

Cyber Security
“`html CentOS 9 Vulnerability A severe use-after-free (UAF) vulnerability within the Linux kernel’s sch_cake queuing discipline (Qdisc) impacts CentOS 9, enabling local users to acquire root access. On February 5, 2026, security firm SSD Secure Disclosure...

Cyber Security
“`html The cybersecurity domain has become more ominous due to the intricate advancements of the KongTuke operation. Active since the middle of 2025, this group of threat actors has consistently honed its methods to circumvent traditional enterprise security...







