Cyber Security
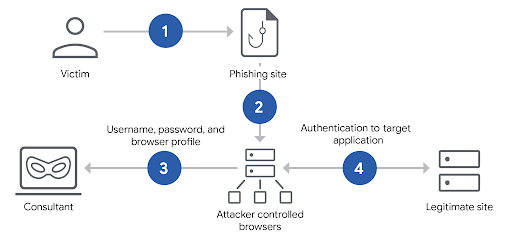
An advanced cyberattack method known as Browser-in-the-Middle (BitM) has surfaced, empowering malicious actors to circumvent multi-factor authentication (MFA) and snatch user sessions in just a few seconds. This strategy leverages web browser features to seize...
Cyber Security
The surge of remote work has significantly expanded the attack surface for cyber attackers, underscoring the heightened importance of robust cybersecurity solutions. With organizations adapting to a scenario where employees are working from diverse locations, the...
Cyber Security
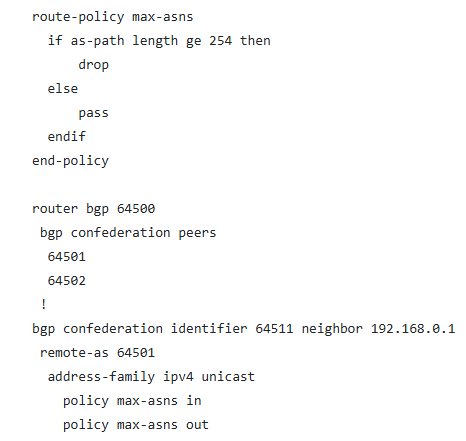
Cisco has released security notifications regarding various vulnerabilities impacting its IOS XR Software, focusing primarily on a notable memory corruption issue within the Border Gateway Protocol (BGP) confederation implementation. The identified vulnerability,...
Cyber Security
The CISA heightened its cybersecurity warning by including six critical Microsoft Windows vulnerabilities in its Known Exploited Vulnerabilities (KEV) Catalog, with four specifically impacting the New Technology File System (NTFS). These weaknesses identified as...
Cyber Security
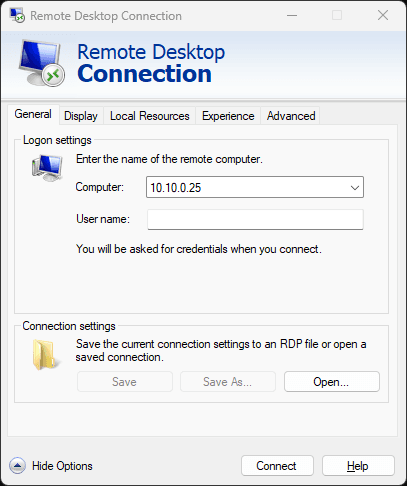
Microsoft’s Remote Desktop Protocol (RDP) has unveiled an obscure yet pivotal security attribute informally termed as “incognito mode” utilizing its /public command-line parameter. This feature, officially labeled as public mode, bars the client from...

Cyber Security
Elastic has published an urgent security alert regarding a crucial weakness in Kibana, dubbed as CVE-2025-25012, which permits authenticated intruders to carry out random commands on impacted systems. The imperfection, scoring 9.9 on the CVSS v3.1 scale, arises from a...






