Cyber Security
Ascension Health, one of the biggest healthcare systems in the United States, has disclosed a substantial breach of data security that may impact approximately 5.6 million patient records, encompassing patients and staff. The organization announced that unapproved...

Cyber Security
It is crucial for modern businesses to practice effective data cleanliness. From operational efficiency to cybersecurity readiness, the reliability of stored data is vital for ensuring your organization’s data hygiene policy is trustworthy. To guarantee that...
Cyber Security
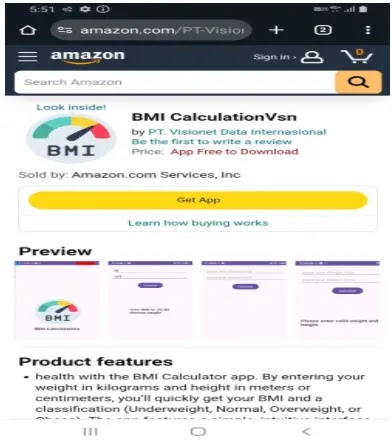
Recently, a rather innocuous application named “BMI CalculationVsn” has been uncovered on the Amazon App Store, posing as a regular health tool to pilfer information. This app engages in nefarious activities like screen recording, fetching a roster of all installed...

Cyber Security
Approaching 2025, it becomes crucial to review the advancements and various obstacles encountered in cybersecurity during the past year. Despite witnessing significant progress in security technologies and heightened awareness of emerging cybersecurity risks, 2024...
Cyber Security
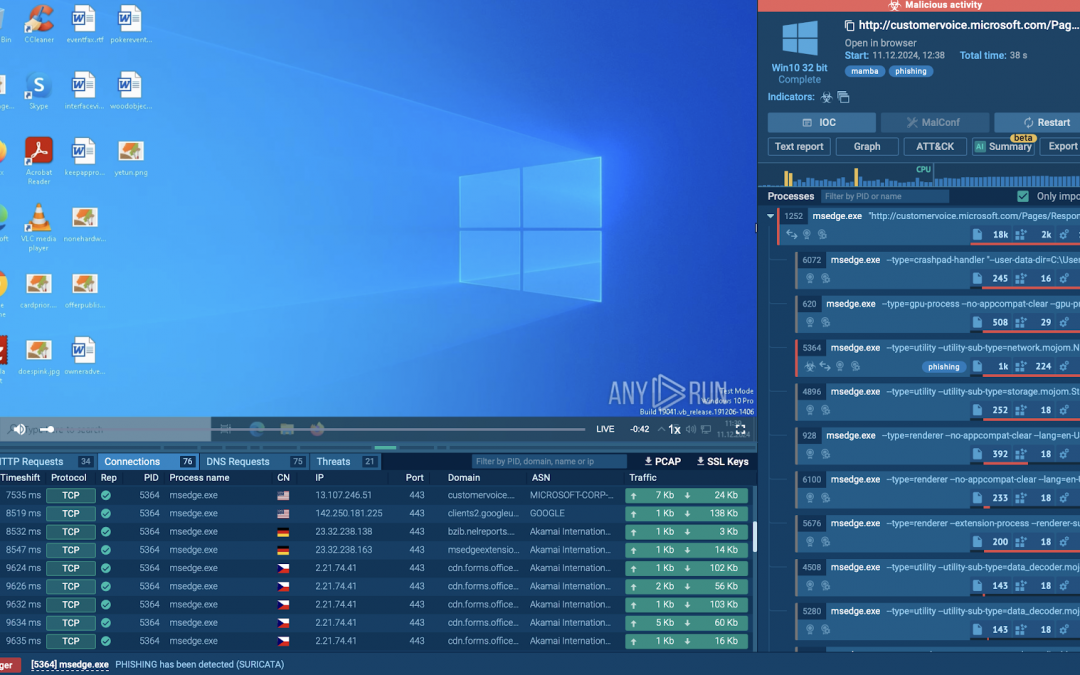
Phishing schemes are constantly advancing, utilizing genuine platforms and services to trick unwary targets. A strategy highlighted by recent research from ANY.RUN involves the exploitation of Microsoft Dynamics 365. Let’s delve into how malicious actors...

Cyber Security
Over the past few years, significant focus has been placed on the developmental stage of artificial intelligence (AI) technology and its influence on cybersecurity. The potential risks associated with AI-generated attacks remain prevalent and worrisome in numerous...





