Cyber Security
An advanced assault campaign utilizing Cloudflare’s Workers service to disseminate harmful applications camouflaged as authentic software. On December 17, 2024, the Ukrainian Computer Emergency Response Team (CERT-UA) disclosed that they had detected various websites...

Cyber Security
Artificial intelligence with generative capabilities (gen AI) is at the forefront of cybersecurity, with red teams playing a crucial role in pinpointing vulnerabilities that others may miss. Considering that the mean price of a data breach has surged to a record $4.88...
Cyber Security
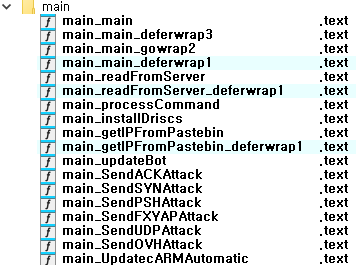
The ASEC Security Intelligence Center has discovered a novel variation of DDoS malware, dubbed cShell, with a focus on inadequately managed Linux SSH servers (screen and hping3). This malware capitalizes on feeble SSH credentials and utilizes Linux utilities for...
Cyber Security
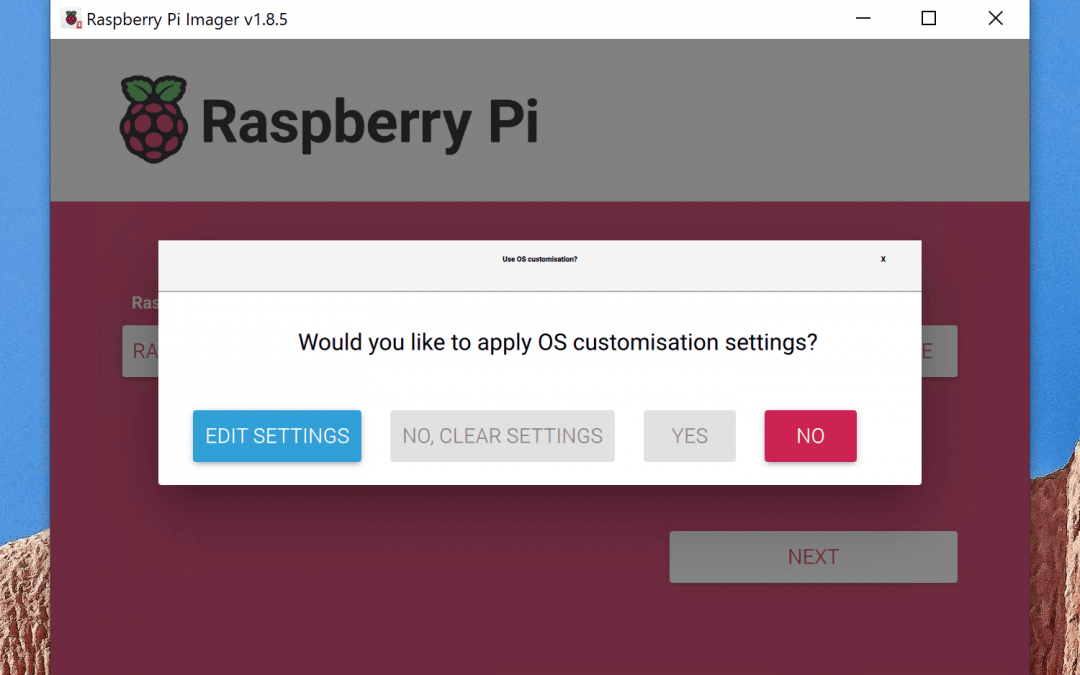
The long-awaited final launch of Kali Linux for version 2024.4 has arrived, brimming with numerous enhancements, fresh hacking utilities, and robust functionalities, ranging from an updated default Python edition to the discontinuance of i386 kernel backing. Kali...
Cyber Security
Welcome to this week’s Cyber Security Newsletter, where we explore the most recent advancements and critical updates in the field of cybersecurity. Your participation in this swiftly changing digital domain is crucial, and our goal is to furnish you with the...

Cyber Security
During the night before Christmas in 2023, cyber attackers struck the Ohio State Lottery, forcing the shutdown of various systems. Simultaneously, the Dark Web hosted a “Leaksmas” event, where cyber offenders shared pilfered data as a holiday gesture. The month of...




