
Cyber Security
“`html By 2026, personal information is not merely a privacy issue; it has evolved into a security threat. With the emergence of AI-based data gathering and artificial identity fraud, your digital traces are being collected like never before. Data erasure...

Cyber Security
“`html A significant sandbox escape weakness has been discovered in vm2. This extensively utilized Node.js library offers sandbox isolation for running untrusted code. The issue, recorded as CVE-2026-22709 (GHSA-99p7-6v5w-7xg8), impacts all releases up to and...

Cyber Security
“`html Microsoft issued urgent out-of-band security patches on January 26, 2026, to resolve CVE-2026-21509, a zero-day vulnerability that allows circumvention of security features in Microsoft Office, actively targeted by attackers. The defect, classified as...

Cyber Security
“`html Microsoft has initiated an urgent probe into substantial stability complications affecting the January 2026 security update for Windows 11, after reports indicate that the patch is resulting in serious boot failures on physical devices. The update,...
Cyber Security
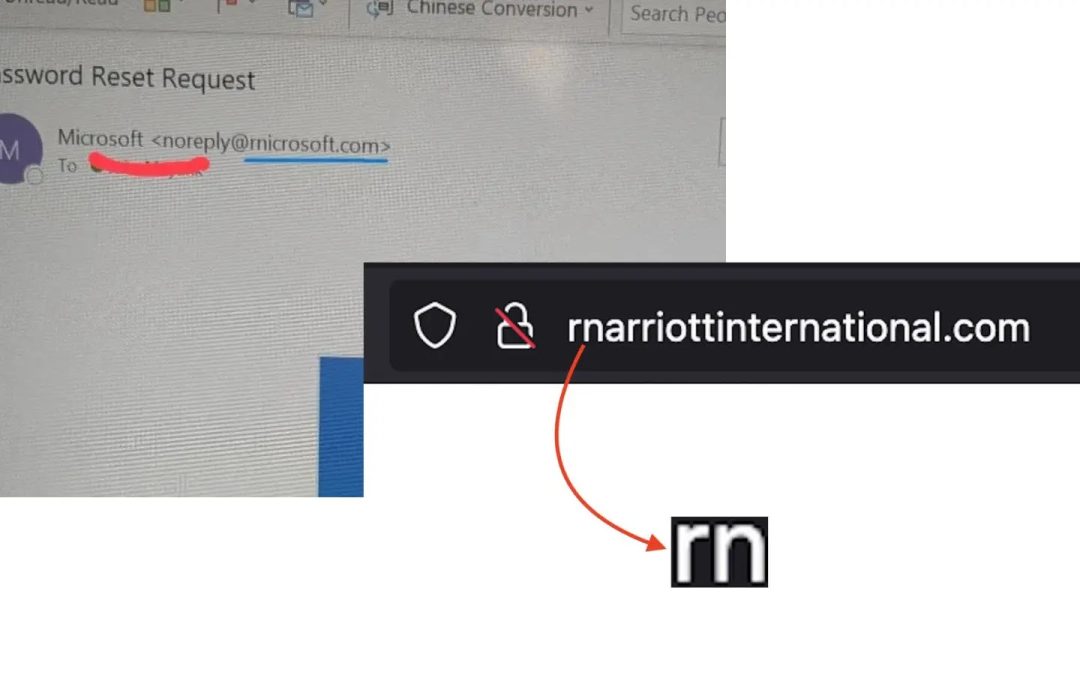
“`html A complex “homoglyph” phishing scheme aimed at patrons of Marriott International and Microsoft. Cybercriminals are registering domains that substitute the letter “m” with the pairing “rn” (r + n), generating counterfeit websites that appear remarkably...

Cyber Security
“`html Microsoft provided U.S. federal authorities the digital keys required to unlock three encrypted laptops associated with a significant COVID unemployment fraud in Guam. This situation illustrates how encryption keys stored in the cloud can assist law...







