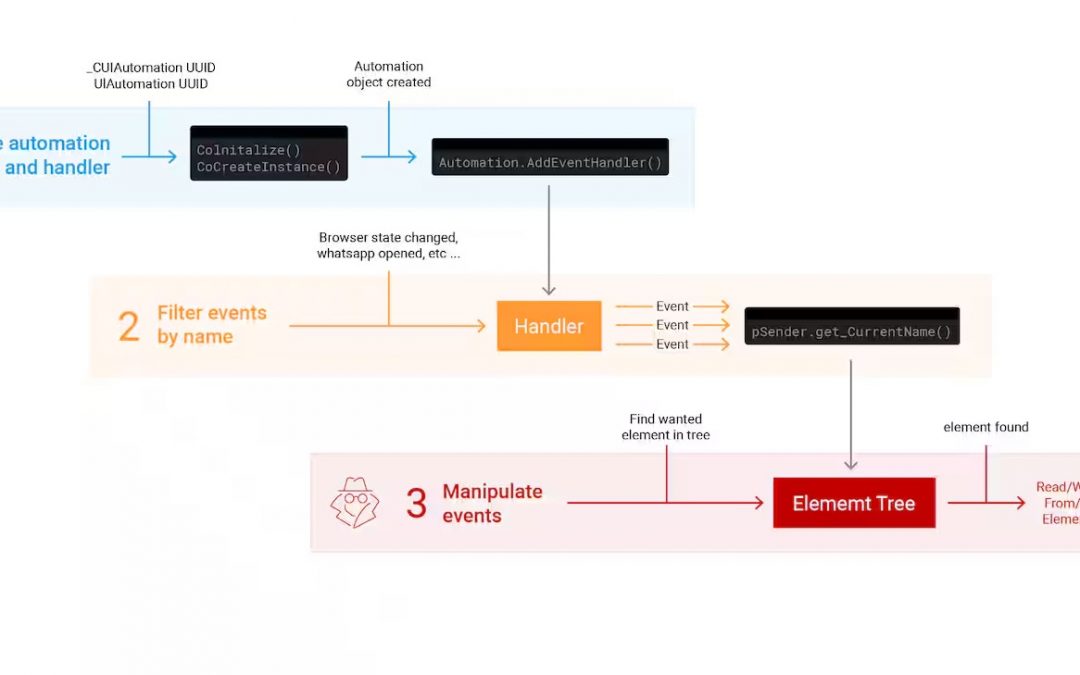
Cyber Security
There has been a recent discovery by security experts of an innovative attack strategy that takes advantage of Microsoft’s UI Automation framework, potentially putting a large number of Windows users at risk. A security researcher named Tomer Peled, working for...

Cyber Security
A newly discovered critical security flaw, labeled as CVE-2024-49138, has been detected as a zero-day vulnerability in the Windows Common Log File System (CLFS) Driver. The security breach has been confirmed by Microsoft as an Elevation of Privilege concern and has...

Cyber Security
As a professional dealing with cybersecurity incidents, the tranquility of life can swiftly transition into turmoil. What is it about the role of incident responder that attracts individuals to step forward for this pivotal position in the realm of cybersecurity?...
Cyber Security
Electrica Group, one of the prominent energy service providers in Romania, has confirmed that it is facing a ransomware incident. The cyber attack has led the company to activate its emergency protocols and closely cooperate with national cybersecurity authorities to...
Cyber Security
Welcome to this edition of the Cybersecurity Newsletter, where we delve into the most recent advancements and vital updates in the cybersecurity realm. Your pivotal role in this fast-paced digital domain is paramount, and we are here to provide you with the freshest...
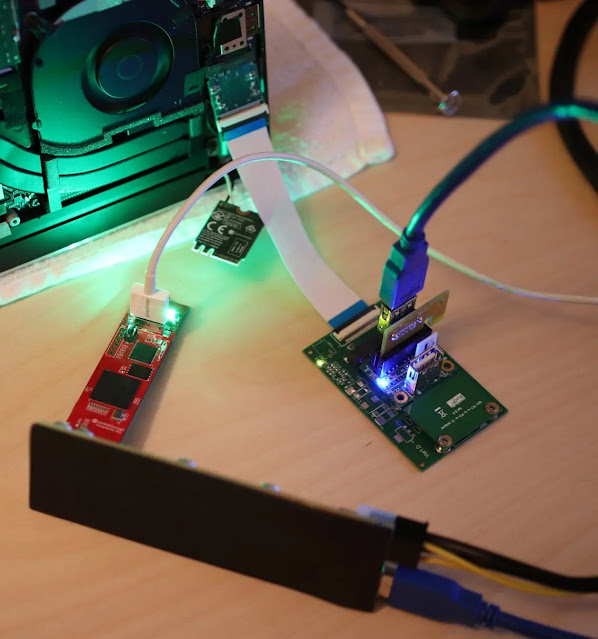
Cyber Security
A novel form of breach, named “DaMAgeCard,” capitalizes on the SD Express standard to gain direct entry to a device’s memory through its SD card reader. This technique sidesteps conventional security measures, enabling intruders to retrieve confidential information or...





