
Cyber Security
Thinking of TikTok as the place to discover new recipes and chuckle at amusing clips, one cannot overlook the cybersecurity worries associated with the platform. Nevertheless, TikTok is making efforts in recent times to uphold cybersecurity standards through its...
Cyber Security
The ransomware operators of Black Basta have enhanced their strategies by utilizing Microsoft Teams to distribute Zbot, DarkGate, and Custom Malware. In an ongoing social engineering operation, a threat actor overwhelms a user’s mailbox with spam before reaching out...

Cyber Security
In 2024, there was a notable rise in the skills, assertiveness, and unpredictability of ransomware assailants. Almost all the major statistics have increased — more ransomware factions, larger targets, and higher payouts. Criminal ransomware syndicates also target...
Cyber Security
One Identity – a Hot Company: Privileged Access Management (PAM) – secured the 12th Cyber Defense Magazine’s Annual InfoSec Awards at CyberDefenseCon 2024. Victorious in the Hot Company: Privileged Access Management (PAM) category, One Identity celebrates...

Cyber Security
Throughout numerous eras, the shadowy realm of the deep web has constructed and sustained its own ever-changing economy, fueled by the procurement and transactions of pilfered information, user authentication details, and corporate intellectual property. Similar to...
Cyber Security
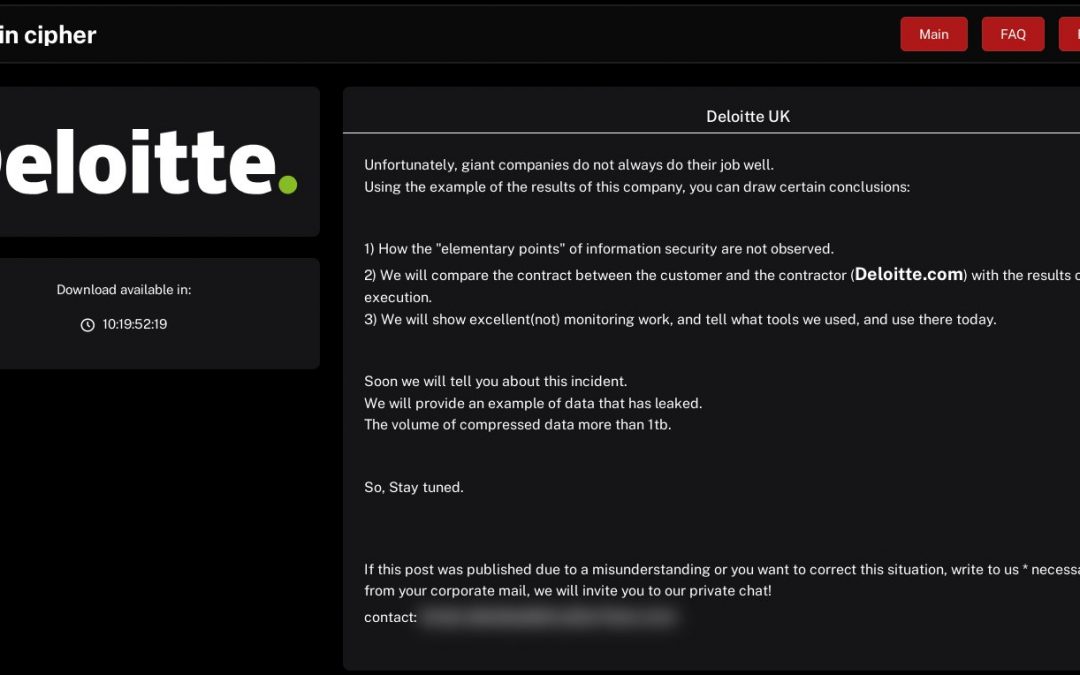
The infamous ransomware gang Brain Cipher has asserted that they successfully infiltrated Deloitte UK, supposedly extracting more than 1 terabyte of confidential information from the large professional services company. Brain Cipher, a ransomware syndicate that...






