Cyber Security
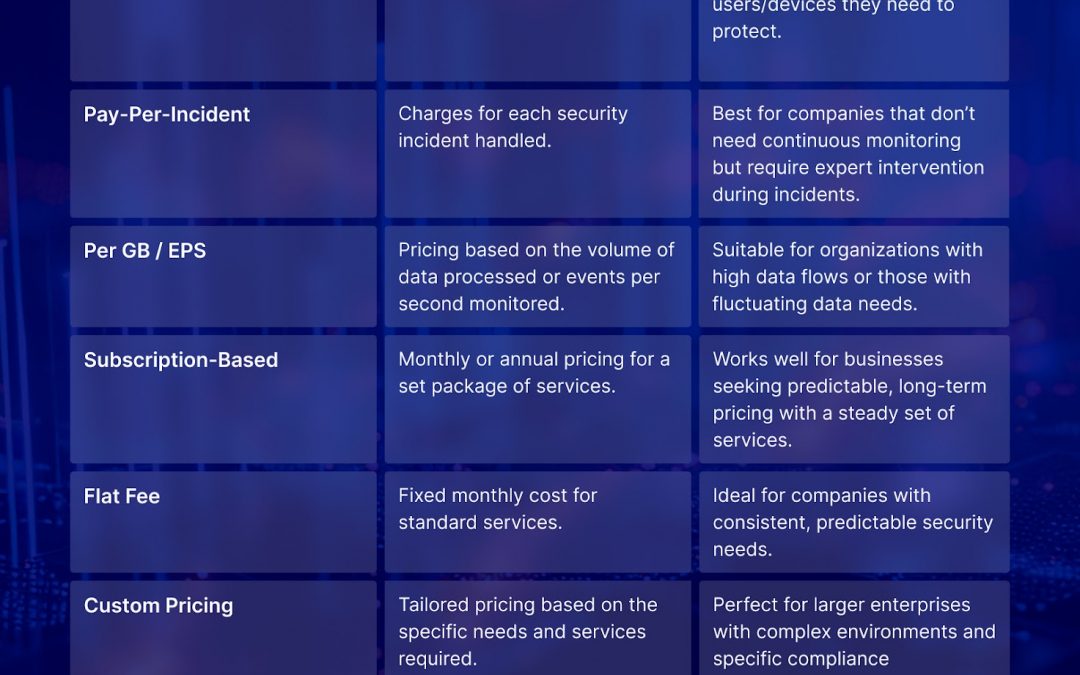
Online security is increasingly vital as cyber risks escalate in complexity and frequency. For companies of all sizes, relying on Managed Security Service Providers (MSSPs) is a wise decision to protect data and infrastructure. However, grasping MSSP pricing...

Cyber Security
Adversaries at the national level are shifting their strategies, moving away from destroying data towards emphasizing stealth and espionage. As stated in the Microsoft 2023 Digital Defense Report, “nation-state attackers are boosting their investments and...
Cyber Security
Let’s face it—nobody enjoys contemplating worst-case scenarios. However, in today’s digital landscape, cyberattacks are more a matter of “when” than “if.” The stakes become even greater when operating your business on AWS. Cloud...

Cyber Security
Nowadays, vital infrastructure organizations depend on operational technology (OT) to oversee and regulate the systems and procedures needed to sustain essential services to the public. However, given the highly interconnected nature of OT deployments, cybersecurity...
Cyber Security
SAP has unveiled its latest security patch update for July 2024, which has addressed 18 vulnerabilities across its products. This update comes with remedies for two critical flaws that have the potential to grant unauthorized entry to crucial data and systems. One of...
Cyber Security
Contemporary security tools are continuously developing, enhancing their capacity to shield organizations from cyber risks. Even with these advancements, malicious entities still manage to breach networks and endpoints at times. As a result, it is imperative for...





