
Cyber Security
“`html Microsoft provided U.S. federal authorities the digital keys required to unlock three encrypted laptops associated with a significant COVID unemployment fraud in Guam. This situation illustrates how encryption keys stored in the cloud can assist law...
Cyber Security
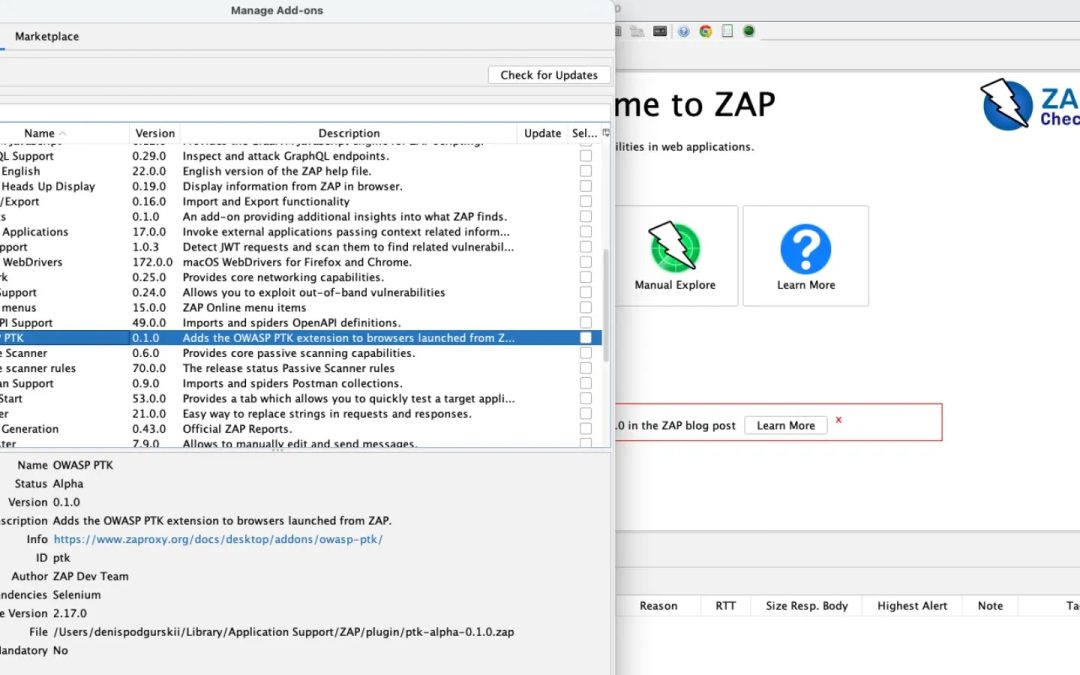
“`html The Zed Attack Proxy (ZAP) group has unveiled the OWASP PTK extension, version 0.2.0 alpha, which incorporates the OWASP Penetration Testing Kit (PTK) browser add-on directly into browsers initiated by ZAP. This enhances application security evaluation by...

Cyber Security
“`html Cisco has revealed a significant zero-day remote code execution (RCE) vulnerability, CVE-2026-20045, currently being exploited in real scenarios. This flaw impacts essential Unified Communications products, permitting unauthorized adversaries to execute...

Cyber Security
“`html Madison, USA, January 20th, 2026, CyberNewsWire Experienced cybersecurity executive contributes decades of expertise and patented advancements to propel the next generation of proactive security measures. Sprocket Security has today declared the selection...

Cyber Security
“`html A critical flaw within the Google ecosystem permitted intruders to circumvent Google Calendar’s privacy settings using a standard calendar invitation. This revelation emphasizes a rising category of threats termed “Indirect Prompt Injection,” wherein...

Cyber Security
“`html Microsoft has issued an out-of-band urgent update to fix a severe problem impacting Remote Desktop connections on Windows client devices. This issue arose immediately after the implementation of the January 2026 security update, labeled as KB5074109....







